Posts Tagged ‘smartcard flash decrypt’
 Decrypt IC Flash
Decrypt IC Flash
Decrypt IC Flash memory, reset the Microcontroller security fuse bit when crack microcontroller using focus ion beam, and extract IC flash memory code in the format of heximal;
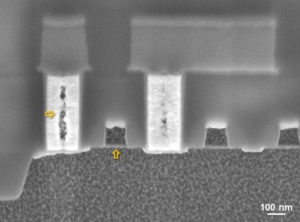
Decrypt IC Flash memory, reset the Microcontroller security fuse bit when crack microcontroller using focus ion beam, and extract IC flash memory code in the format of heximal
Invasive MCU breaking start with partial or full removal of the chip package in order to expose the silicon die. There are several methods, depending upon the package type and the requirements for further analysis. For microcontrollers, partial decapsulation is normally used, so that the device can be placed in a standard programmer unit and tested.
Some devices cannot be decapsulated and still maintain their electrical integrity. In this case the chip die has to be bonded to a chip carrier using a bonding machine which connects to the bonding pads on the die with thin aluminium or gold wire. Such bonding machines are available from different manufacturers and can be bought second-hand for less than £5,000. The contacts to the die can be also established using microprobing needles on a probing station.
To undertake further work under a FIB or a SEM the chip surface has to be coated with a thin gold layer making it conductive, otherwise it will very quickly accumulate charge and the picture become dark. We used an Emitech K550 gold sputter coater to coat samples prior to the FIB work. Some modern FIB machines have a built-in video camera for optical navigation, eliminating the need for the special coating.