Posts Tagged ‘read avr mcu heximal content’
 Read AVR ATmel MCU Firmware
Read AVR ATmel MCU Firmware
Read AVR ATmel MCU Firmware from ATmel AVR microcontroller program memory and data memory, remove the package by focus ion beam which is one of the most commonly used methods in MCU crack for Microcontroller content copying;
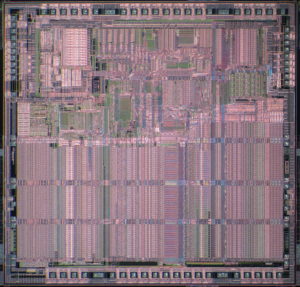
Read AVR ATmel MCU Firmware from ATmel AVR microcontroller program memory and data memory, remove the package by focus ion beam which is one of the most commonly used methods in MCU crack for Microcontroller content copying
These read avr mcu attacks require direct access to the internal components of the device. If it is a security module or a USB dongle, then it has to be opened to get access to the internal memory chips. In the case of a smartcard or a microcontroller, the packaging should be removed followed by FIB or laser depassivation to get access to the internal wires buried deep under the passivation layer of the chip. Such attacks normally require a well equipped and knowledgeable attacker to succeed. Meanwhile, invasive attacks are becoming constantly more demanding and expensive, as feature sizes shrink and device complexity increases.