Posts Tagged ‘decipher avr mcu ic protected eeprom’
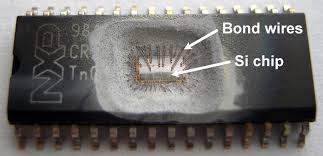
 Crack Motorola MC68HC05B6 Microcontroller
Crack Motorola MC68HC05B6 Microcontroller
Crack Motorola MC68HC05B6 Microcontroller by focus ion beam to modify MCU circuitry pattern for the purpose of reset encryption status, then the firmware can be readout from MCU;
the Motorola MC68HC05B6 microcontroller has a Mask ROM bootloader which prevents user code upload if the security bit is set. The part of the code responsible for the security. It checks the contents of the first byte in the EEPROM and if the bit 0, assigned as a security fuse, is programmed then the CPU goes into endless loop.
That sort of protection could be relatively easy defeated. As the CPU performs only one instruction in the loop, all the attacker has to do is apply different clock glitches to cause CPU malfunction. He does not even have to carefully synchronise the attack to microcontroller’s CPU clock signal, as doing glitches at a random time will give a success in a short number of attempts. Glitches could be inserted relatively easy without the use of any external generators by short circuiting the crystal resonator for a short time.
When the resonator starts it produces oscillations at different harmonics which cause many glitches. In most cases the attack has to be applied at a certain clock cycle to cause the desired result. In this case it is better to use either a signal pattern generator which can supply all the necessary signals to the chip or built such a generator using an FPGA prototyping board.