Posts Tagged ‘brute force chip crack’
 Brute Force Chip Break Application
Brute Force Chip Break Application
Brute force chip break can be also applied to a hardware design implemented into an ASIC or a CPLD. In this case the chip breaker tries to apply all possible logic combinations to the input of the device while observing all its outputs.
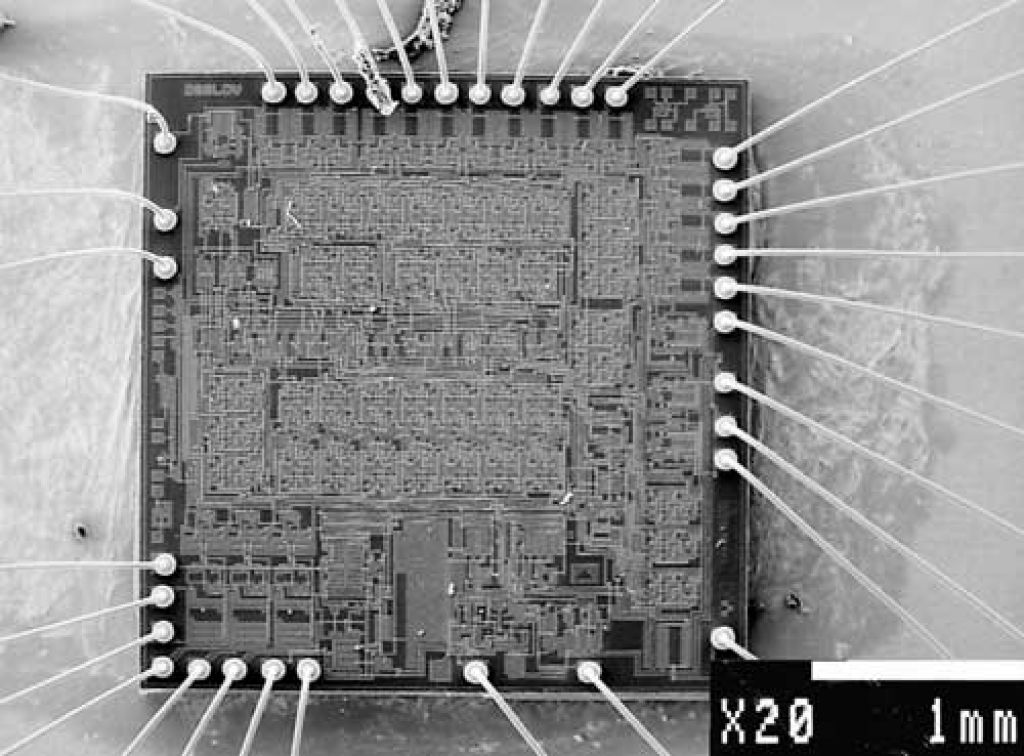
That kind of microcontroller breaking could be also called black-box analysis because the MCU cracker does not have to know anything about the design of the device under test.
He only tries to understand the function of the device by trying all possible combinations of signals. This approach works well only for relatively small logic devices. Another problem the MCU reading process will face is that designs implemented in CPLDs or ASICs have flip-flops, so the output will probably be function of both the previous state and the input.
But the search space can be significantly reduced if the signals are observed and analysed beforehand. For example, clock inputs, data buses and some control signals could be easily identified, significantly reducing the area of search.
 Brute Force Chip Attack
Brute Force Chip Attack
Brute Force Chip Attack include invasive and semi-invasive microcontroller cracking, hardware attacking will be able to get access to embedded memory such as flash and eeprom memory, then readout firmware from Microprocessor memory;
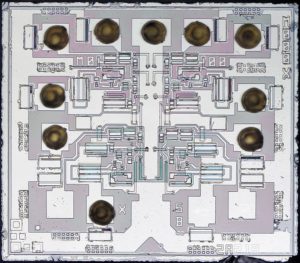
Brute Force Chip Attack include invasive and semi-invasive microcontroller cracking, hardware attacking will be able to get access to embedded memory such as flash and eeprom memory, then readout firmware from Microprocessor memory
MCU Attack has different meanings for cryptography and semiconductor hardware. In cryptography, a brute force chip attack would be defined as the methodical application of a large set of trials for a key to the system. This is usually done with a computer or an array of FPGAs delivering patterns at high speed and looking for success.