Posts Tagged ‘Ataque o microprocessador criptografado PIC18F67K22 e copie o conteúdo do firmware’
 Attack PIC18F67K22 Microcontroller Memory
Attack PIC18F67K22 Microcontroller Memory
Attack PIC18F67K22 Microcontroller Memory can help engineer to disable the protection of MCU, and embedded binary from PIC18F67K22 MCU will be unlocked and extracted;

All of the devices in the PIC18F67K22 family offer different oscillator options, allowing users a range of choices in developing application hardware. These include:
· A Phase Lock Loop (PLL) frequency multiplier, available to the external oscillator modes which allows clock speeds of up to 64 MHz. PLL can also be used with the internal oscillator.
· An internal oscillator block that provides a 16 MHz clock (±2% accuracy) and an INTRC source (approximately 31 kHz, stable over temperature and VDD)
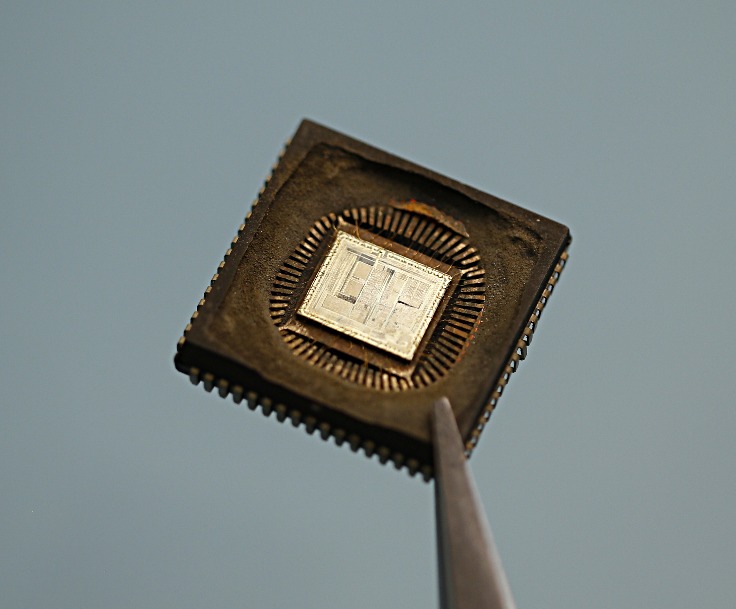
The PIC18F67K22 family provides ample room for application code, from 32 Kbytes to 128 Kbytes of code space. The Flash cells for program memory are rated to last up to 10,000 erase/write cycles. Data retention without refresh is conservatively estimated to be greater than 40 years.

saldırı şifreli MICROCHIP PIC18F67K22 mikrodenetleyici flash belleği ve eeprom belleği, mühendisin koruyucu PIC18F67K22 MCU’nun korumasını devre dışı bırakmasına yardımcı olabilir ve orijinal ana mikroişlemci PIC18F67K22’den gelen ikili dosyanın veya onaltılık verilerin gömülü aygıt yazılımının kilidi açılacak ve çıkarılacaktır;
The Flash program memory is readable and writable. During normal operation, the PIC18F87K22 family also provides plenty of room for dynamic application data with up to 3,862 bytes of data RAM. Should 128 Kbytes of memory be inadequate for an application, the 80-pin members of the PIC18F87K22 family have an External Memory Bus (EMB) enabling the controller’s internal program counter to address a memory space of up to 2 Mbytes. This is a level of data access that few 8-bit devices can claim and enables:
атака зашифрованная флэш-память микроконтроллера MICROCHIP PIC18F67K22 и память EEPROM могут помочь инженеру отключить защиту защитного микроконтроллера PIC18F67K22, а встроенная прошивка двоичного файла или шестнадцатеричных данных из исходного главного микропроцессора PIC18F67K22 будет разблокирована и извлечена;
The PIC18F67K22 family implements the optional extension to the PIC18 instruction set, adding eight new instructions and an Indexed Addressing mode. Enabled as a device configuration option, the extension has been specifically designed to optimize re-entrant application code originally developed in high-level languages, such as ‘C’.

ataque criptografado à memória flash do microcontrolador MICROCHIP PIC18F67K22 e à memória eeprom pode ajudar o engenheiro a desativar a proteção do MCU protetor PIC18F67K22, e o firmware incorporado do arquivo binário ou dados heximais do microprocessador mestre original PIC18F67K22 será desbloqueado e extraído;