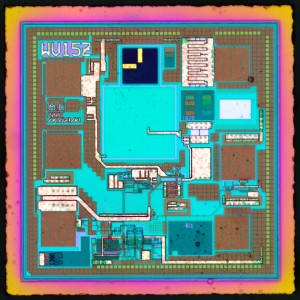
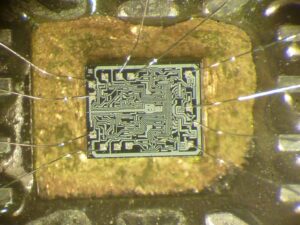
Recover Microcontroller MC68HC908JB16 Firmware
Recover Microcontroller MC68HC908JB16 Firmware
Recover Microcontroller MC68HC908JB16 Firmware from flash memory include the program and data, the heximal file can be copied to new MCU MC68HC908JB16;
Recover Microcontroller MC68HC908JB16 Firmware from flash memory include the program and data, the heximal file can be copied to new MCU MC68HC908JB16
Features of the Microcontroller MC68HC908JB16 include the following:
High-performance M68HC08 architecture
Fully upward-compatible object code with M6805, M146805, and
M68HC05 families
Low-power design; fully static with stop and wait modes
6-MHz internal bus frequency
16,384 bytes of on-chip FLASH memory with security1 feature
384 bytes of on-chip random access memory (RAM)
Up to 21 general-purpose input/output (I/O) pins, including:
– 15 shared-function I/O pins
– 8-bit keyboard interrupt port
– 10mA high current drive for PS/2 connection on 2 pins (with USB module disabled)
– 1 dedicated I/O pin, with 25mA direct drive for infrared LED (32-pin package) if recover Microcontroller STM32F107RCT6 code
– 6 dedicated I/O pins, with 25mA direct drive for infrared LED on 2 pins and 10mA direct drive for normal LED on 4 pins (28-pin package)
Two 16-bit, 2-channel timer interface modules (TIM1 and TIM2) with selectable input capture, output compare, PWM capability on each channel, and external clock input option (TCLK)
Universal Serial Bus specification 2.0 low-speed functions:
– 1.5Mbps data rate
– On-chip 3.3V regulator
– Endpoint 0 with 8-byte transmit buffer and 8-byte receive buffer
– Endpoint 1 with 8-byte transmit buffer
– Endpoint 2 with 8-byte transmit buffer and 8-byte receive buffer
Serial communications interface module (SCI)
Dual clock generator modules (CGM) (32-pin package)
In-circuit programming capability using USB communication or standard serial link on PTA0 pin
System protection features:
– Optional computer operating properly (COP) reset
– Optional Low-voltage detection with reset
– Illegal opcode detection with reset
– Illegal address detection with reset
Master reset pin with internal pull-up and power-on reset
IRQ interrupt pin with internal pull-up and schmitt-trigger input
32-pin low-profile quad flat pack (LQFP) and 28-pin small outline
integrated circuit package (SOIC)
Features of the CPU08 include the following:
Enhanced HC05 programming model
Extensive loop control functions
16 addressing modes (eight more than the HC05)
16-bit index register and stack pointer
Memory-to-memory data transfers
Fast 8 × 8 multiply instruction
Fast 16/8 divide instruction
Binary-coded decimal (BCD) instructions
Optimization for controller applications
Third party C language support
 Recover Chip PIC16F913 Binary
Recover Chip PIC16F913 Binary
When working with embedded systems, one of the most challenging tasks can be extracting or recovering chip PIC16F913 binary data. This microcontroller, produced by Microchip Technology, is commonly found in remote controls, industrial equipment, and sensor-based systems. Unlike many older or simpler microcontrollers, the PIC16F913 features advanced security mechanisms, making its firmware difficult to access or duplicate without specialized skills and tools.

Podczas pracy z systemami wbudowanymi jednym z najtrudniejszych zadań może być wyodrębnienie lub odzyskanie danych binarnych układu PIC16F913. Ten mikrokontroler, wyprodukowany przez Microchip Technology, jest powszechnie spotykany w pilotach zdalnego sterowania, sprzęcie przemysłowym i systemach opartych na czujnikach. W przeciwieństwie do wielu starszych lub prostszych mikrokontrolerów, PIC16F913 posiada zaawansowane mechanizmy bezpieczeństwa, co utrudnia dostęp do jego oprogramowania układowego lub jego kopiowanie bez specjalistycznych umiejętności i narzędzi.
At CIRCUIT ENGINEERING CO.,LTD we offer professional services to read out, restore, and recover PIC16F913 binaries, whether for software migration, security auditing, or backup purposes. Our process allows clients to unlock, decode, and decrypt protected memory, giving full access to the firmware, EEPROM, or flash data stored inside the microcontroller.
What Makes PIC16F913 Unique?
Compared to simpler chips like the PIC16C554 or PIC12CE519, the PIC16F913 includes:
Extended instruction set (Mid-Range architecture) with more advanced features.
Integrated LCD driver module, making it more common in display-based applications.
More robust memory protection, including locked and encrypted flash/eeprom blocks, making unauthorized binary readouts or program duplication more difficult.

تحليل ثنائي وفك تشفير البرامج الثابتة بمجرد استخراجها، تُحلل الملفات الثنائية أو السداسية لتحديد أنماط التعليمات، ومقاطع البيانات، والهياكل المنطقية. ثم يقوم فريقنا بفك تشفير أرشيف البرامج الثابتة، وإعادة بناء تسلسل الكود الأصلي ومنطقه. استعادة البرامج الثابتة واستعادة الكود المصدري عند الحاجة، نستعيد الكود المصدري من الملف الثنائي المفكك. على الرغم من أن ملف البرنامج المستعاد قد لا يتطابق تمامًا مع الكود الأصلي المكتوب بلغة C، إلا أنه يوفر تمثيلًا قابلاً للاستخدام والقراءة، ويمكن تعديله أو نسخه حسب الحاجة. الاستنساخ والنسخ بعد استعادة البيانات، نساعد عملائنا على استنساخ أو نسخ البرامج الثابتة على شرائح أو أجهزة جديدة. سواءً للنسخ الاحتياطي أو الإنتاج، يتيح هذا النسخ الكامل للبرنامج الأصلي المؤمّن.
On-board comparators, analog modules, and enhanced I/O, increasing complexity of its firmware structure.
This chip’s secured and embedded firmware is designed to prevent unauthorized duplication or tampering. However, with the right techniques, even protected programs and data archives can be successfully recovered.
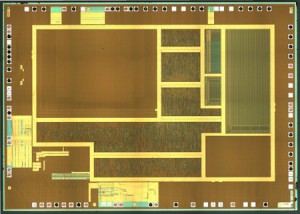
Recover Chip PIC16F913 Binary is a process of dumping heximal from MCU’s PIC16F913 flash memory, the status of Microcontroller PIC16F913 can be changed from locked to open by MCU Cracking technique
Recover Chip PIC16F913 Binary is a process of dumping heximal from MCU’s PIC16F913 flash memory, the status of Microcontroller PIC16F913 can be changed from locked to open by MCU Cracking technique;
High-Performance RISC CPU:
· Only 35 instructions to learn:
– All single-cycle instructions except branches
· Operating speed:
– DC – 20 MHz oscillator/clock input
– DC – 200 ns instruction cycle
· Program Memory Read (PMR) capability
· Interrupt capability
· 8-level deep hardware stack
· Direct, Indirect and Relative Addressing modes
Special Microcontroller Features:
· Precision Internal Oscillator:
– Factory calibrated to ±1%, typical
– Software selectable frequency range of
8 MHz to 125 kHz
– Software tunable
– Two-Speed Start-up mode
– External Oscillator fail detect for critical applications
– Clock mode switching during operation for power savings
· Software selectable 31 kHz internal oscillator
· Power-Saving Sleep mode
· Wide operating voltage range (2.0V-5.5V)
· Industrial and Extended temperature range
· Power-on Reset (POR)
· Power-up Timer (PWRT) and Oscillator Start-up
Timer (OST)
· Brown-out Reset (BOR) with software control option
· Enhanced Low-Current Watchdog Timer (WDT) with on-chip oscillator (software selectable nominal 268 seconds with full prescaler) with software enable
· Multiplexed Master Clear with pull-up/input pin
· Programmable code protection
· High-Endurance Flash/EEPROM cell:
– 100,000 write Flash endurance
– 1,000,000 write EEPROM endurance
– Flash/Data EEPROM retention: > 40 years

Quando si lavora con sistemi embedded, uno dei compiti più impegnativi può essere l’estrazione o il recupero dei dati binari del chip PIC16F913. Questo microcontrollore, prodotto da Microchip Technology, è comunemente presente in telecomandi, apparecchiature industriali e sistemi basati su sensori. A differenza di molti microcontrollori più vecchi o più semplici, il PIC16F913 è dotato di meccanismi di sicurezza avanzati, che rendono il suo firmware difficile da accedere o duplicare senza competenze e strumenti specializzati.
Low-Power Features:
· Standby Current:
– <100 nA @ 2.0V, typical
· Operating Current:
– 11 ìA @ 32 kHz, 2.0V, typical
– 220 ìA @ 4 MHz, 2.0V, typical
· Watchdog Timer Current:
– 1 ìA @ 2.0V, typical
Peripheral Features:
· Liquid Crystal Display module:
– Up to 60/96/168 pixel drive capability on 28/40/64-pin devices, respectively
– Four commons
· Up to 24/35/53 I/O pins and 1 input-only pin:
– High-current source/sink for direct LED drive
– Interrupt-on-change pin
– Individually programmable weak pull-ups
· In-Circuit Serial Programming™ (ICSP™) via two pins
· Analog comparator module with:
– Two analog comparators
– Programmable on-chip voltage reference (CVREF) module (% of VDD)
– Comparator inputs and outputs externally accessible
· A/D Converter:
– 10-bit resolution and up to 8 channels
· Timer0: 8-bit timer/counter with 8-bit
programmable prescaler
· Enhanced Timer1:
– 16-bit timer/counter with prescaler
– External Timer1 Gate (count enable)
– Option to use OSC1 and OSC2 as Timer1 oscillator if INTOSCIO or LP mode is selected
· Timer2: 8-bit timer/counter with 8-bit period register, prescaler and postscaler
· Addressable Universal Synchronous
Asynchronous Receiver Transmitter (AUSART)
· Up to 2 Capture, Compare, PWM modules:
– 16-bit Capture, max. resolution 12.5 ns
– 16-bit Compare, max. resolution 200 ns
– 10-bit PWM, max. frequency 20 kHz
· Synchronous Serial Port (SSP) with I2C™
 Copy Chip AT89S8252 Flash
Copy Chip AT89S8252 Flash
In the world of embedded systems, accessing and duplicating secured microcontrollers is often essential for product maintenance, migration, and system upgrades. One such frequently used microcontroller is the AT89S8252, an 8051-based device from Atmel (now Microchip), known for its built-in flash memory, EEPROM, and high-performance architecture. At [Your Company Name], we offer specialized services to copy chip AT89S8252 flash, helping clients unlock, readout, and replicate protected firmware from embedded systems.
![В мире встраиваемых систем доступ к защищенным микроконтроллерам и их дублирование часто необходимы для обслуживания продукта, миграции и обновления системы. Одним из таких часто используемых микроконтроллеров является AT89S8252, устройство на базе 8051 от Atmel (теперь Microchip), известное своей встроенной флэш-памятью, EEPROM и высокопроизводительной архитектурой. В [Your Company Name] мы предлагаем специализированные услуги по копированию флэш-памяти чипа AT89S8252, помогая клиентам разблокировать, считывать и копировать защищенную прошивку из встраиваемых систем.](https://www.ic-crack.com/wp-content/uploads/2014/04/5a300c56-52a4-11e4-b366-001f16e3c682-663x528_0_0-300x239.jpeg)
В мире встраиваемых систем доступ к защищенным микроконтроллерам и их дублирование часто необходимы для обслуживания продукта, миграции и обновления системы. Одним из таких часто используемых микроконтроллеров является AT89S8252, устройство на базе 8051 от Atmel (теперь Microchip), известное своей встроенной флэш-памятью, EEPROM и высокопроизводительной архитектурой. В [Your Company Name] мы предлагаем специализированные услуги по копированию флэш-памяти чипа AT89S8252, помогая клиентам разблокировать, считывать и копировать защищенную прошивку из встраиваемых систем.
When a microcontroller like the AT89S8252 is deployed in commercial or industrial systems, its firmware is often encrypted, locked, or secured with protective memory configurations to prevent unauthorized access. While this protection enhances security, it can also be an obstacle when legitimate recovery, duplication, or system analysis is required. Our service is designed to crack, decode, and open locked flash archives for clients who need to access their own systems or legally replicate legacy hardware and firmware.

Wenn ein Mikrocontroller wie der AT89S8252 in kommerziellen oder industriellen Systemen eingesetzt wird, ist seine Firmware häufig verschlüsselt, gesperrt oder mit schützenden Speicherkonfigurationen geschützt, um unbefugten Zugriff zu verhindern. Dieser Schutz erhöht zwar die Sicherheit, kann aber auch ein Hindernis darstellen, wenn eine legitime Wiederherstellung, Duplizierung oder Systemanalyse erforderlich ist. Unser Service ist darauf ausgelegt, gesperrte Flash-Archive für Kunden zu knacken, zu entschlüsseln und zu öffnen, die auf ihre eigenen Systeme zugreifen oder veraltete Hardware und Firmware legal replizieren müssen.
Unlocking the Value of Legacy Embedded Systems
Many companies rely on legacy hardware platforms with embedded microcontrollers like the AT89S8252. However, over time, documentation, source code, or development tools may become unavailable. In such cases, our ability to restore and replicate embedded flash and EEPROM memory becomes invaluable. We help our clients copy and duplicate the flash contents of secured chips, enabling them to maintain production, repair critical systems, or migrate to new hardware platforms without rewriting entire firmware packages from scratch.
Our solutions ensure the safe readout and backup of binary or heximal program files, preserving the full operational behavior of the original embedded device. Whether you’re looking to replicate locked program data, decrypt encrypted firmware archives, or simply clone the contents of a protective chip, we have the tools and experience to deliver accurate and reliable results.

जब AT89S8252 जैसे माइक्रोकंट्रोलर को वाणिज्यिक या औद्योगिक सिस्टम में तैनात किया जाता है, तो अनधिकृत पहुँच को रोकने के लिए इसके फ़र्मवेयर को अक्सर एन्क्रिप्ट किया जाता है, लॉक किया जाता है या सुरक्षात्मक मेमोरी कॉन्फ़िगरेशन के साथ सुरक्षित किया जाता है। जबकि यह सुरक्षा सुरक्षा को बढ़ाती है, यह वैध पुनर्प्राप्ति, दोहराव या सिस्टम विश्लेषण की आवश्यकता होने पर बाधा भी बन सकती है। हमारी सेवा उन क्लाइंट के लिए लॉक किए गए फ़्लैश आर्काइव को क्रैक, डिकोड और खोलने के लिए डिज़ाइन की गई है, जिन्हें अपने सिस्टम तक पहुँचने या लीगेसी हार्डवेयर और फ़र्मवेयर को कानूनी रूप से दोहराने की ज़रूरत है। लीगेसी एम्बेडेड सिस्टम के मूल्य को अनलॉक करना कई कंपनियाँ AT89S8252 जैसे एम्बेडेड माइक्रोकंट्रोलर वाले लीगेसी हार्डवेयर प्लेटफ़ॉर्म पर निर्भर करती हैं। हालाँकि, समय के साथ, दस्तावेज़ीकरण, स्रोत कोड या विकास उपकरण अनुपलब्ध हो सकते हैं। ऐसे मामलों में, एम्बेडेड फ़्लैश और EEPROM मेमोरी को पुनर्स्थापित और दोहराने की हमारी क्षमता अमूल्य हो जाती है। हम अपने क्लाइंट को सुरक्षित चिप्स की फ़्लैश सामग्री को कॉपी और डुप
Comprehensive Firmware Recovery and Cloning Services
We serve a wide range of industries that rely on the integrity of firmware and memory data in their embedded controllers. Our services are often used to break open locked flash memory, decrypt proprietary binary code, or duplicate secured program files for product recovery and system continuity. These solutions are especially critical when dealing with protected embedded files that cannot be easily recompiled or replaced due to the absence of source code or original development teams.
By offering advanced techniques to unlock and replicate flash and EEPROM memory archives, we provide our clients with peace of mind—knowing their embedded systems can be supported long after the original manufacturer has moved on.
Copy Chip AT89S8252 Flash content has to decapsulate the silicon package of AT89S8252 which act as the 1st layer of tamper resistent protection, unlock Microcontroller AT89S8252 also needs to modify its security fuse bit;
Features
· Compatible with MCS®51 Products
· 8K Bytes of In-System Reprogrammable Downloadable Flash Memory
– SPI Serial Interface for Program Downloading
– Endurance: 1,000 Write/Erase Cycles
2K Bytes EEPROM
– Endurance: 100,000 Write/Erase Cycles
4V to 6V Operating Range
Fully Static Operation: 0 Hz to 24 MHz
Three-level Program Memory Lock
256 x 8-bit Internal RAM
32 Programmable I/O Lines
Three 16-bit Timer/Counters
Nine Interrupt Sources
Programmable UART Serial Channel
SPI Serial Interface
Low-power Idle and Power-down Modes
Interrupt Recovery from Power-down
Programmable Watchdog Timer
Dual Data Pointer
Power-off Flag
Description
The AT89S8252 is a low-power, high-performance CMOS 8-bit microcontroller with 8K bytes of downloadable Flash programmable and erasable read-only memory and 2K bytes of EEPROM. The device is manufactured using Atmel’s high-density nonvolatile memory technology and is compatible with the industry-standard 80C51 instruction set and pinout.
The on-chip downloadable Flash allows the program memory to be reprogrammed In-System through an SPI serial interface or by a conventional nonvolatile memory programmer. By combining a versatile 8-bit CPU with downloadable Flash on a monolithic chip, the Atmel AT89S8252 is a powerful microcontroller, which provides a highly-flexible and cost-effective solution to many embedded control applications.
The AT89S8252 provides the following standard features: 8K bytes of downloadable Flash, 2K bytes of EEPROM, 256 bytes of RAM, 32 I/O lines, programmable watchdog timer, two data pointers, three 16-bit timer/counters, a six-vector two-level interrupt architecture, a full duplex serial port, on-chip oscillator, and clock circuitry.
In addition, the Copy Chip AT89S8252 is designed with static logic for operation down to zero frequency and supports two software selectable power saving modes. The Idle Mode stops the CPU while allowing the RAM, timer/counters, serial port, and interrupt system to continue functioning. The Power-down mode saves the RAM contents but freezes the oscillator, disabling all other chip functions until the next external interrupt or hardware reset.
The downloadable Flash can be changed a single byte at a time and is accessible through the SPI serial interface. Holding RESET active forces the SPI bus into a serial programming interface and allows the program memory to be written to or read from unless lock bits have been activated.
 Copy Microcontroller PIC16F684 Firmware
Copy Microcontroller PIC16F684 Firmware
The PIC16F684 microcontroller from Microchip is a popular choice for compact, low-power embedded applications. It is frequently found in consumer electronics, industrial controls, automotive systems, and security devices. Its cost-efficiency, reliability, and rich feature set make it ideal for a range of embedded projects. However, when developers or engineers need to copy microcontroller PIC16F684 firmware, they often face challenges due to protective mechanisms such as code locking, encryption, and memory protection fuses.
At Circuit Engineering Co.,LTD, we provide specialized services to restore, unlock, and duplicate firmware from protected microcontrollers like the PIC16F684. Whether for legacy system recovery, competitive analysis, or functional migration, we assist clients in decoding, reading out, and replicating embedded firmware safely and securely.
Understanding the Importance of Firmware Duplication
In many real-world scenarios, access to the original firmware binary or heximal file is lost or was never made available. This creates major difficulties for maintenance, upgrading, or cloning a system. Clients come to us when they need to copy microcontroller PIC16F684 firmware to:
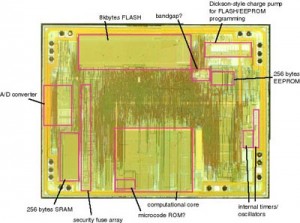
Copy Microcontroller PIC16F684 Firmware needs to unlock Microprocessor PIC16F684 security fuse bit, the silicon package can be removed by proper chemical solution, by focus ion beam will effectively modify the circuitry pattern of MCU PIC16F684
Copy Microcontroller PIC16F684 Firmware needs to unlock Microprocessor PIC16F684 security fuse bit, the silicon package can be removed by proper chemical solution, by focus ion beam will effectively modify the circuitry pattern of MCU PIC16F684;
High-Performance RISC CPU:
· Only 35 instructions to learn:
– All single-cycle instructions except branches
· Operating speed:
– DC – 20 MHz oscillator/clock input
– DC – 200 ns instruction cycle
· Interrupt capability
· 8-level deep hardware stack
Low-Power Features:
· Standby Current:
– 1 nA @ 2.0V, typical
· Operating Current:
– 8.5 µA @ 32 kHz, 2.0V, typical
– 100 µA @ 1 MHz, 2.0V, typical
· Watchdog Timer Current:
– 1 µA @ 2.0V, typical
· Direct, Indirect and Relative Addressing modes
Peripheral Features:
Mikrokontroler PIC16F684 firmy Microchip jest popularnym wyborem w przypadku kompaktowych, energooszczędnych aplikacji wbudowanych. Często można go znaleźć w elektronice użytkowej, sterowaniu przemysłowym, systemach samochodowych i urządzeniach zabezpieczających. Jego opłacalność, niezawodność i bogaty zestaw funkcji sprawiają, że idealnie nadaje się do wielu projektów wbudowanych. Jednak gdy programiści lub inżynierowie muszą skopiować oprogramowanie układowe mikrokontrolera PIC16F684, często stają przed wyzwaniami z powodu mechanizmów ochronnych, takich jak blokada kodu, szyfrowanie i bezpieczniki zabezpieczające pamięć.
Special Microcontroller Features:
· Precision Internal Oscillator:
– Factory calibrated to ±1%
– Software selectable frequency range of 8 MHz to 31 kHz
– Software tunable
– Two-speed Start-up mode
– Crystal fail detect for critical applications
– Clock mode switching during operation for power savings
· Power-saving Sleep mode
· Wide operating voltage range (2.0V-5.5V)
· Industrial and Extended Temperature range
· Power-on Reset (POR)
· Power-up Timer (PWRT) and Oscillator Start-up Timer (OST)
· Brown-out Detect (BOD) with software control option
· Enhanced low-current Watchdog Timer (WDT) with on-chip oscillator (software selectable nominal 268 seconds with full prescaler) with software enable;
· Multiplexed Master Clear with pull-up/input pin
· Programmable code protection
· High Endurance Flash/EEPROM cell:
– 100,000 write Flash endurance
– 1,000,000 write EEPROM endurance

يُعد المتحكم الدقيق PIC16F684 من Microchip خيارًا شائعًا للتطبيقات المدمجة صغيرة الحجم ومنخفضة الطاقة. يُستخدم بكثرة في الإلكترونيات الاستهلاكية، وأجهزة التحكم الصناعية، وأنظمة السيارات، وأجهزة الأمن. تجعله فعاليته من حيث التكلفة، وموثوقيته، ومجموعة ميزاته الغنية مثاليًا لمجموعة من المشاريع المدمجة. ومع ذلك، عندما يحتاج المطورون أو المهندسون إلى نسخ البرامج الثابتة للمتحكم الدقيق PIC16F684، غالبًا ما يواجهون تحديات بسبب آليات الحماية مثل قفل الكود، والتشفير، وصمامات حماية الذاكرة.
– Flash/Data EEPROM retention: > 40 years
· 12 I/O pins with individual direction control:
– High current source/sink for direct LED drive
– Interrupt-on-pin change
– Individually programmable weak pull-ups
– Ultra Low-power Wake-up (ULPWU)
· Analog comparator module with:
– Two analog comparators
– Programmable on-chip voltage reference (CVREF) module (% of VDD)
– Comparator inputs and outputs externally accessible
· A/D Converter:
– 10-bit resolution and 8 channels
· Timer0: 8-bit timer/counter with 8-bit programmable prescaler· Enhanced Timer1:
– 16-bit timer/counter with prescaler
– External Gate Input mode
– Option to use OSC1 and OSC2 in LP mode as Timer1 oscillator if INTOSC mode selected
· Timer2: 8-bit timer/counter with 8-bit period register, prescaler and postscaler
· Enhanced Capture, Compare, PWM module:
– 16-bit Capture, max resolution 12.5 ns
– Compare, max resolution 200 ns
– 10-bit PWM with 1, 2 or 4 output channels, programmable “dead time”, max frequency 20 kHz
· In-Circuit Serial ProgrammingTM (ICSPTM) via two pins.

میکروکنترلر PIC16F684 از Microchip یک انتخاب محبوب برای برنامه های جاسازی شده فشرده و کم مصرف است. اغلب در لوازم الکترونیکی مصرفی، کنترل های صنعتی، سیستم های خودرو و دستگاه های امنیتی یافت می شود. مقرون به صرفه بودن، قابلیت اطمینان و مجموعه ویژگی های غنی آن را برای طیف وسیعی از پروژه های تعبیه شده ایده آل می کند. با این حال، زمانی که توسعهدهندگان یا مهندسان نیاز به کپی کردن میانافزار میکروکنترلر PIC16F684 دارند، اغلب به دلیل مکانیسمهای حفاظتی مانند قفل کد، رمزگذاری و فیوزهای محافظت از حافظه با چالشهایی مواجه میشوند.
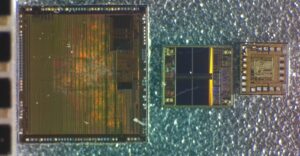
 Copy MCU PIC32MX440F512H Binary
Copy MCU PIC32MX440F512H Binary
Copy MCU PIC32MX440F512H Binary and rewrite the firmware from master Microcontroller PIC32MX440F512H to blank new Microprocessor, decapsulate the MCU PIC32MX440F512H and get access to the databus is the first step of MCU cracking;
High-Performance 32-bit RISC CPU:
· MIPS32® M4K® 32-bit core with 5-stage pipeline
· 80 MHz maximum frequency
· 1.56 DMIPS/MHz (Dhrystone 2.1) performance at 0 wait state Flash access
· Single-cycle multiply and high-performance divide unit
· MIPS16e® mode for up to 40% smaller code size
· Two sets of 32 core register files (32-bit) to reduce interrupt latency
· Prefetch Cache module to speed execution
· Operating temperature range of -40ºC to +105ºC
· Operating voltage range of 2.3V to 3.6V
· 32K to 512K Flash memory (plus an additional 12 KB of boot Flash)
· 8K to 32K SRAM memory
· Pin-compatible with most PIC24/dsPIC® DSC devices
· Multiple power management modes
· Multiple interrupt vectors with individually programmable priority
· Fail-Safe Clock Monitor Mode
· Configurable Watchdog Timer with on-chip Low-Power RC Oscillator for reliable operation
Peripheral Features:
· Atomic SET, CLEAR and INVERT operation on select peripheral registers
· Up to 4-channel hardware DMA with automatic data size detection
· USB 2.0-compliant full-speed device and On-The-Go (OTG) controller
· USB has a dedicated DMA channel
· 3 MHz to 25 MHz crystal oscillator
· Internal 8 MHz and 32 kHz oscillators
· Separate PLLs for CPU and USB clocks
· Two I2C™ modules
· Two UART modules with:
– RS-232, RS-485 and LIN support
– IrDA® with on-chip hardware encoder and decoder
· Up to two SPI modules
· Parallel Master and Slave Port (PMP/PSP) with 8-bit and 16-bit data and up to 16 address lines
· Hardware Real-Time Clock and Calendar (RTCC)
· Five 16-bit Timers/Counters (two 16-bit pairs combine to create two 32-bit timers)
· Five capture inputs
· Five compare/PWM outputs
· Five external interrupt pins
· High-Speed I/O pins capable of toggling at up to 80 MHz
· High-current sink/source (18 mA/18 mA) on all I/O pins
· Configurable open-drain output on digital I/O pins
Debug Features:
· Two programming and debugging Interfaces:
– 2-wire interface with unintrusive access and real-time data exchange with application
– 4-wire MIPS® standard enhanced JTAG interface
· Unintrusive hardware-based instruction trace
· IEEE Standard 1149.2-compatible (JTAG) boundary scan
Analog Features:
· Up to 16-channel 10-bit Analog-to-Digital Converter:
– 1000 ksps conversion rate
– Conversion available during Sleep, Idle
· Two Analog Comparators
 Recover IC STM32F107RCT6 Code
Recover IC STM32F107RCT6 Code
The STM32F107RCT6 is a high-performance ARM Cortex-M3 based microcontroller by STMicroelectronics, widely used in industrial, automotive, and embedded systems due to its integrated Ethernet MAC, USB OTG, CAN, and rich peripheral features. However, many applications implement protective measures to prevent firmware extraction, making it extremely difficult to readout, copy, or clone the original program. At [Your Company Name], we offer professional services to recover IC STM32F107RCT6 code, helping clients unlock, decrypt, and replicate protected firmware, even from locked or secured memory blocks.

STM32F107RCT6 — это высокопроизводительный микроконтроллер на базе ARM Cortex-M3 от STMicroelectronics, широко используемый в промышленных, автомобильных и встраиваемых системах благодаря интегрированным Ethernet MAC, USB OTG, CAN и богатым периферийным функциям. Однако во многих приложениях реализованы защитные меры для предотвращения извлечения прошивки, что делает чрезвычайно сложным считывание, копирование или клонирование исходной программы. В Circuit Engineering Co.,LTD мы предлагаем профессиональные услуги по восстановлению кода IC STM32F107RCT6, помогая клиентам разблокировать, расшифровать и скопировать защищенную прошивку даже из заблокированных или защищенных блоков памяти.
Why Recover STM32F107RCT6 Firmware?
There are many valid reasons to recover embedded firmware from STM32 microcontrollers:
-
Legacy Support: Recovering firmware, binary, or heximal files from legacy systems where source code is lost.
-
System Migration: Transferring a protected program to a newer hardware platform.
-
Security Research: Analyzing secured firmware archives for vulnerabilities.
-
Product Cloning & Duplication: Replicating locked source code for batch production or testing.
Recover IC STM32F107RCT6 code from MCU STM32F107RCT6 program memory, use MCU cracking technique to remove the security fuse by focus ion beam
Recover IC STM32F107RCT6 code from MCU STM32F107RCT6 program memory, use MCU cracking technique to remove the security fuse by focus ion beam;
Core: ARM 32-bit Cortex™-M3 CPU
– 72 MHz maximum frequency, 1.25 DMIPS/MHz (Dhrystone 2.1) performance at 0 wait state memory
LQFP100 14 × 14 mm
LQFP64 10 × 10 mm
LFBGA100 10 × 10 mm
– Single-cycle multiplication and hardware division
Memories
– 64 to 256 Kbytes of Flash memory
– 64 Kbytes of general-purpose SRAM Clock, reset and supply management
– 2.0 to 3.6 V application supply and I/Os
– POR, PDR, and programmable voltage detector (PVD)
– 3-to-25 MHz crystal oscillator
– Internal 8 MHz factory-trimmed RC
– Internal 40 kHz RC with calibration
– 32 kHz oscillator for RTC with calibration

STM32F107RCT6는 STMicroelectronics의 고성능 ARM Cortex-M3 기반 마이크로컨트롤러로, 이더넷 MAC, USB OTG, CAN 및 풍부한 주변 장치 기능을 통합하여 산업, 자동차 및 임베디드 시스템에서 널리 사용됩니다. 그러나 많은 애플리케이션에서 펌웨어 추출을 방지하기 위한 보호 기능이 구현되어 있어 원본 프로그램을 읽거나 복사하거나 복제하는 것이 매우 어렵습니다. Circuit Engineering Co.,LTD는 IC STM32F107RCT6 코드 복구 전문 서비스를 제공하여 고객이 잠기거나 보안된 메모리 블록에서도 보호된 펌웨어를 잠금 해제, 복호화 및 복제할 수 있도록 지원합니다.
Low power
– Sleep, Stop and Standby modes
– VBAT supply for RTC and backup registers 2 × 12-bit, 1 µs A/D converters (16 channels)
– Conversion range: 0 to 3.6 V
– Sample and hold capability
– Temperature sensor
– up to 2 MSPS in interleaved mode 2 × 12-bit D/A converters DMA: 12-channel DMA controller
– Supported peripherals: timers, ADCs, DAC, I2Ss, SPIs, I2Cs and USARTs
Up to 10 timers with pinout remap capability
– Up to four 16-bit timers, each with up to 4 IC/OC/PWM or pulse counter and quadrature (incremental) encoder input
– 1 × 16-bit motor control PWM timer with dead-time generation and emergency stop
– 2 × watchdog timers (Independent and Window)
– SysTick timer: a 24-bit downcounter
– 2 × 16-bit basic timers to drive the DAC Up to 14 communication interfaces with pinout remap capability
– Up to 2 × I2C interfaces (SMBus/PMBus)

STM32F107RCT6, entegre Ethernet MAC, USB OTG, CAN ve zengin çevre birimi özellikleri sayesinde endüstriyel, otomotiv ve gömülü sistemlerde yaygın olarak kullanılan STMicroelectronics tarafından üretilen yüksek performanslı bir ARM Cortex-M3 tabanlı mikrodenetleyicidir. Ancak birçok uygulama, ürün yazılımının çıkarılmasını önlemek için koruyucu önlemler uygular ve bu da orijinal programı okumayı, kopyalamayı veya klonlamayı son derece zorlaştırır. Circuit Engineering Co.,LTD’de, IC STM32F107RCT6 kodunu kurtarmak için profesyonel hizmetler sunuyoruz ve müşterilerin kilitli veya güvenli bellek bloklarından bile korumalı ürün yazılımını kilidini açmalarına, şifresini çözmelerine ve çoğaltmalarına yardımcı oluyoruz.
– Up to 5 USARTs (ISO 7816 interface, LIN, IrDA capability, modem control)
– Up to 3 SPIs (18 Mbit/s), 2 with a multiplexed I2S interface that offers audio class accuracy via advanced PLL schemes
– 2 × CAN interfaces (2.0B Active) with 512 bytes of dedicated SRAM
– USB 2.0 full-speed device/host/OTG controller with on-chip PHY that supports
HNP/SRP/ID with 1.25 Kbytes of dedicated SRAM
– 10/100 Ethernet MAC with dedicated DMA and SRAM (4 Kbytes): IEEE1588 hardware support, MII/RMII available on all packages
– Cortex-M3 Embedded Trace Macrocell™ Up to 80 fast I/O ports
– 51/80 I/Os, all mappable on 16 external interrupt vectors and almost all 5 V-tolerant CRC calculation unit, 96-bit unique ID
 Copy IC ATmega8L Heximal
Copy IC ATmega8L Heximal
In the fast-moving world of embedded systems, accessing and analyzing firmware stored within microcontrollers is often essential for maintenance, debugging, legacy system recovery, or competitive analysis. One of the most frequently encountered chips in various industrial and consumer applications is the ATmega8L, a low-power CMOS 8-bit microcontroller based on the AVR enhanced RISC architecture. Many times, developers, engineers, or researchers need to copy IC ATmega8L heximal content to clone, replicate, or restore a program, especially when original source code is unavailable or the chip is protected by security fuses.
En el dinámico mundo de los sistemas embebidos, acceder y analizar el firmware almacenado en microcontroladores suele ser esencial para tareas de mantenimiento, depuración, recuperación de sistemas heredados o análisis de la competencia. Uno de los chips más comunes en diversas aplicaciones industriales y de consumo es el ATmega8L, un microcontrolador CMOS de 8 bits y bajo consumo basado en la arquitectura RISC mejorada por AVR. A menudo, desarrolladores, ingenieros o investigadores necesitan copiar el contenido heximal del IC ATmega8L para clonar, replicar o restaurar un programa, especialmente cuando el código fuente original no está disponible o el chip está protegido por fusibles de seguridad.
At [Your Company Name], we specialize in helping clients break, read out, and decode secured ATmega8L memory, offering reliable solutions to duplicate or unlock protected firmware for legal and technical purposes.

Copy IC Atmega8L Heximal from MCU ATmega8L flash memory, crack MCU protective system and disable its security fuse bit, the status of Microcontroller ATmega8L will be modified from locked to unlocked one
Copy IC Atmega8L Heximal from MCU ATmega8L flash memory, crack MCU ATmega8L protective system and disable its security fuse bit, the status of Microcontroller ATmega8L will be modified from locked to unlocked one;
High-performance, Low-power AVR 8-bit Microcontroller
· Advanced RISC Architecture
– 130 Powerful Instructions – Most Single-clock Cycle Execution
– 32 x 8 General Purpose Working Registers
– Fully Static Operation
– Up to 16 MIPS Throughput at 16 MHz
– On-chip 2-cycle Multiplier
High Endurance Non-volatile Memory segments

Der ATmega8L wird häufig in Automobilsystemen, industriellen Steuerungen, der Robotik und der Unterhaltungselektronik eingesetzt. Der Chip enthält internen Flash-Speicher, EEPROM und SRAM und ist über ISP (In-System Programming) programmierbar. Nach der Inbetriebnahme werden diese Bausteine jedoch häufig durch Sicherungsbits gesperrt oder verschlüsselt, um unbefugten Zugriff zu verhindern. Hier kommt unsere Expertise ins Spiel.
– 8K Bytes of In-System Self-programmable Flash program memory
– 512 Bytes EEPROM
– 1K Byte Internal SRAM
– Write/Erase Cycles: 10,000 Flash/100,000 EEPROM (1)(3)
– Data retention: 20 years at 85°C/100 years at 25°C (2)(3)
– Optional Boot Code Section with Independent Lock Bits
In-System Programming by On-chip Boot Program True Read-While-Write Operation
– Programming Lock for Software Security
Peripheral Features
– Two 8-bit Timer/Counters with Separate Prescaler, one Compare Mode
– One 16-bit Timer/Counter with Separate Prescaler, Compare Mode, and Capture Mode
– Real Time Counter with Separate Oscillator
– Three PWM Channels
– 8-channel ADC in TQFP and QFN/MLF package
Eight Channels 10-bit Accuracy
– 6-channel ADC in PDIP package
Six Channels 10-bit Accuracy
– Byte-oriented Two-wire Serial Interface
– Programmable Serial USART
– Master/Slave SPI Serial Interface
– Programmable Watchdog Timer with Separate On-chip Oscillator
– On-chip Analog Comparator
Special Microcontroller Features
– Power-on Reset and Programmable Brown-out Detection
– Internal Calibrated RC Oscillator
![Que vous ayez affaire à un microcontrôleur ATmega8L verrouillé, à une carte obsolète avec un firmware chiffré, ou que vous ayez simplement besoin de copier un fichier hexadécimal pour un projet de sauvegarde ou de duplication, [Nom de votre entreprise] est là pour vous aider. Notre équipe expérimentée peut déverrouiller, pirater et répliquer vos données embarquées avec rapidité, précision et sécurité.](https://www.ic-crack.com/wp-content/uploads/2014/04/s-l1200-3-300x300.jpg)
Que vous ayez affaire à un microcontrôleur ATmega8L verrouillé, à une carte obsolète avec un firmware chiffré, ou que vous ayez simplement besoin de copier un fichier hexadécimal pour un projet de sauvegarde ou de duplication, [Nom de votre entreprise] est là pour vous aider. Notre équipe expérimentée peut déverrouiller, pirater et répliquer vos données embarquées avec rapidité, précision et sécurité.
– Five Sleep Modes: Idle, ADC Noise Reduction, Power-save, Power-down, and Standby I/O and Packages
– 23 Programmable I/O Lines
– 28-lead PDIP, 32-lead TQFP, and 32-pad QFN/MLF Operating Voltages
– 2.7 – 5.5V (ATmega8L)
– 4.5 – 5.5V (ATmega8) Speed Grades
– 0 – 8 MHz (ATmega8L)
– 0 – 16 MHz (ATmega8)
Power Consumption at 4 Mhz, 3V, 25°C
– Active: 3.6 mA
– Idle Mode: 1.0 mA
– Power-down Mode: 0.5 µA
 Attack Chip dsPIC33FJ256GP506A Software
Attack Chip dsPIC33FJ256GP506A Software
The dsPIC33FJ256GP506A is a high-performance digital signal controller from Microchip, widely used in industrial, automotive, and embedded systems. However, its security mechanisms can be compromised through advanced techniques such as firmware dumping, reverse engineering, and decryption. This article explores methods to crack, decode, and clone the program stored in its flash memory and EEPROM.
El dsPIC33FJ256GP506A es un controlador de señales digitales de alto rendimiento de Microchip, ampliamente utilizado en sistemas industriales, automotrices y embebidos. Sin embargo, sus mecanismos de seguridad pueden verse comprometidos mediante técnicas avanzadas como el volcado de firmware, la ingeniería inversa y el descifrado. Este artículo explora métodos para descifrar, decodificar y clonar el programa almacenado en su memoria flash y EEPROM.
1. Dumping Firmware from Flash Memory
The primary step in attacking the dsPIC33FJ256GP506A is extracting the binary code from its internal flash memory. Attackers often use hardware tools like a programmer/debugger (PICKit, ICD, or J-Tag) to dump the firmware. If read protection is enabled, more invasive methods like decapsulating the chip and using microprobing or laser fault injection may be required.
Once extracted, the heximal data can be analyzed using disassemblers (IDA Pro, Ghidra) to reverse engineer the source code.
2. Breaking EEPROM Memory Protection
Many devices store critical data (encryption keys, calibration values) in EEPROM memory. Attackers can dump EEPROM contents using I2C/SPI sniffers or direct memory reading via debug interfaces. If the data is encrypted, brute-force attacks or side-channel analysis may help decrypt it.
DsPIC33FJ256GP506A to wydajny cyfrowy kontroler sygnału firmy Microchip, szeroko stosowany w systemach przemysłowych, motoryzacyjnych i wbudowanych. Jednak jego mechanizmy bezpieczeństwa mogą zostać naruszone za pomocą zaawansowanych technik, takich jak zrzucanie oprogramowania układowego, inżynieria wsteczna i deszyfrowanie. W tym artykule omówiono metody łamania, dekodowania i klonowania programu przechowywanego w pamięci flash i EEPROM.
3. Decoding and Reverse Engineering the Program File
After obtaining the binary dump, the next step is decoding the program file. Tools like Binary Ninja or Radare2 assist in converting machine code into readable assembly. Skilled attackers can reconstruct the original logic, modify functionalities, or clone the firmware for unauthorized replication.
4. Restoring Modified Firmware
Once reverse-engineered, attackers may modify the firmware to bypass security checks or introduce malicious code. The altered binary code can be re-flashed into a new chip, effectively cloning the original device.
5. Security Countermeasures
To prevent such attacks, developers should:
Enable code protection (CPS, WDT)
Use secure bootloaders with encryption (AES, RSA)
Implement tamper detection mechanisms
Obfuscate critical source code
Conclusion
The dsPIC33FJ256GP506A is vulnerable to firmware extraction, reverse engineering, and cloning if proper security measures are not applied. By understanding attack methods like memory dumping, decryption, and binary analysis, developers can better protect their designs from unauthorized recovery and copying.
For secure applications, always use hardware security modules (HSM) and encrypted firmware updates to mitigate risks.

Attack Chip dsPIC33FJ256GP506A and compromise Microcontroller dsPIC33FJ256GP506 tamper resistance system, readout MCU software from dsPIC33FJ256 flash and eeprom memory
Attack Chip dsPIC33FJ256GP506A and compromise Microcontroller dsPIC33FJ256GP506 tamper resistance system, readout MCU software from dsPIC33FJ256 flash and eeprom memory;
Operating Conditions
· 3.0V to 3.6V, -40ºC to +150ºC, DC to 20 MIPS
· 3.0V to 3.6V, -40ºC to +125ºC, DC to 40 MIPS
Core: 16-bit dsPIC33F CPU
Timers/Output Compare/Input Capture
· Up to nine 16-bit timers/counters. Can pair up to make four 32-bit timers;
· Eight Output Compare modules configurable as timers/counters;
Code-efficient (C and Assembly) architecture
Two 40-bit wide accumulators
Single-cycle (MAC/MPY) with dual data fetch
Single-cycle mixed-sign MUL plus hardware divide
· Eight Input Capture modules
Communication Interfaces
· Two UART modules (10 Mbps)
– With support for LIN 2.0 protocols and IrDA®
· Two 4-wire SPI modules (15 Mbps)
dsPIC33FJ256GP506A یک کنترل کننده سیگنال دیجیتال با کارایی بالا از Microchip است که به طور گسترده در سیستم های صنعتی، خودروسازی و تعبیه شده استفاده می شود. با این حال، مکانیسمهای امنیتی آن میتواند از طریق تکنیکهای پیشرفتهای مانند تخلیه سیستمافزار، مهندسی معکوس و رمزگشایی به خطر بیفتد. این مقاله روش هایی برای کرک کردن، رمزگشایی و شبیه سازی برنامه ذخیره شده در حافظه فلش و EEPROM آن را بررسی می کند.
Clock Management
· Up to two I2C™ modules (up to 1 Mbaud) with ±2% internal oscillator
Programmable PLLs and oscillator clock sources
Fail-Safe Clock Monitor (FSCM)
Independent Watchdog Timer (WDT)
Fast wake-up and start-up
SMBus support
· Up to two Enhanced CAN (ECAN) modules (1 Mbaud) with 2.0B support
· Data Converter Interface (DCI) module with I2S codec support
Power Management
· Low-power management modes (Sleep, Idle, Doze)
· Integrated Power-on Reset and Brown-out Reset
· 2.1 mA/MHz dynamic current (typical)
· 50 μA IPD current (typical)
Advanced Analog Features
· Two ADC modules:
– Configurable as 10-bit, 1.1 Msps with four S&H or 12-bit, 500 ksps with one S&H
– 18 analog inputs on 64-pin devices and up to 32 analog inputs on 100-pin devices
· Flexible and independent ADC trigger sources
Input/Output
· Sink/Source up to 10 mA (pin specific) for standard VOH/VOL, up to 16 mA (pin specific) for non-standard VOH1
· 5V-tolerant pins
· Selectable open drain, pull-ups, and pull-downs
· Up to 5 mA overvoltage clamp current
· External interrupts on all I/O pins
Qualification and Class B Support
· AEC-Q100 REVG (Grade 1 -40ºC to +125ºC)
· AEC-Q100 REVG (Grade 0 -40ºC to +150ºC)
· Class B Safety Library, IEC 60730
Debugger Development Support
Packages
In-circuit and in-application programming
Two program and two complex data breakpoints
IEEE 1149.2-compatible (JTAG) boundary scan
Trace and run-time watch
 Attack Microcontroller ST62T15C6 firmware
Attack Microcontroller ST62T15C6 firmware
The ST62T15C6 is an 8-bit microcontroller from STMicroelectronics, commonly used in embedded systems. Security researchers and hardware hackers often attempt to attack, crack, or reverse engineer its firmware for analysis, recovery, or cloning purposes. This article explores various techniques used to extract, decode, or dump the firmware from the ST62T15C6 microcontroller.
O ST62T15C6 é um microcontrolador de 8 bits da STMicroelectronics, comumente usado em sistemas embarcados. Pesquisadores de segurança e hackers de hardware frequentemente tentam atacar, crackear ou fazer engenharia reversa em seu firmware para fins de análise, recuperação ou clonagem. Este artigo explora várias técnicas usadas para extrair, decodificar ou despejar o firmware do microcontrolador ST62T15C6.
1. Firmware Extraction Methods
Dumping Flash Memory
The primary method to attack the ST62T15C6 involves dumping the contents of its flash memory or EEPROM memory. Since the firmware is stored in non-volatile memory, attackers use hardware tools like:
- Programmers/JTAG interfaces – If debug ports are accessible, firmware can be read directly.
- Logic analyzers & bus sniffers – Monitoring communication between the MCU and external memory (if any).
- Voltage glitching – Disrupting power or clock signals to bypass read protections.
Decapsulation & Microprobing
If security fuses are enabled, attackers may resort to decapsulating the chip to access the silicon die. Using microprobing, they can directly read the binary code from the memory cells. This method is expensive and requires advanced equipment.
ST62T15C6 — это 8-битный микроконтроллер от STMicroelectronics, обычно используемый во встраиваемых системах. Исследователи безопасности и хакеры оборудования часто пытаются атаковать, взломать или провести обратную разработку его прошивки для анализа, восстановления или клонирования. В этой статье рассматриваются различные методы, используемые для извлечения, декодирования или дампа прошивки из микроконтроллера ST62T15C6.
2. Reverse Engineering the Firmware
Once the heximal data or binary code is extracted, the next step is decoding or disassembling it. Common techniques include:
- Static analysis – Using disassemblers like Ghidra or IDA Pro to convert machine code into assembly.
- Dynamic analysis – Running the firmware in an emulator (e.g., QEMU) to observe behavior.
- Pattern recognition – Searching for known opcode sequences to identify functions.
Since the ST62T15C6 uses a proprietary architecture, custom tools may be needed to decrypt the program file fully.
3. Cloning & Firmware Modification
After successful extraction, attackers may:
- Copy the firmware to another ST62T15C6 chip.
- Modify the source code (if decompiled) to remove security checks.
- Restore corrupted firmware for device recovery.
4. Protection & Countermeasures
To prevent such attacks, manufacturers implement:
- Read-out protection bits – Locking firmware access.
- Encrypted firmware updates – Preventing easy decoding.
- Secure boot mechanisms – Blocking unauthorized code execution.
Conclusion
يُعد ST62T15C6 متحكمًا دقيقًا ثماني البتات من شركة STMicroelectronics، ويُستخدم عادةً في الأنظمة المدمجة. غالبًا ما يحاول باحثو الأمن ومخترقو الأجهزة مهاجمة أو اختراق أو عكس هندسة البرنامج الثابت الخاص به لأغراض التحليل أو الاستعادة أو الاستنساخ. تستكشف هذه المقالة التقنيات المختلفة المستخدمة لاستخراج أو فك تشفير أو تفريغ البرنامج الثابت من المتحكم الدقيق ST62T15C6
Attacking the ST62T15C6 microcontroller firmware requires a mix of hardware and software techniques, from dumping flash memory to reverse engineering binary code. While these methods can be used for legitimate recovery or research, they also pose security risks if exploited maliciously. Developers must implement strong protections to safeguard their firmware from unauthorized cloning or decryption.

Attack Microcontroller ST62T15C6 protective system and extract firmware from MCU ST62T15 memory, the whole tamper resistance system will be disable by Microprocessor unlocking technique
Attack Microcontroller ST62T15C6 protective system and extract firmware from MCU ST62T15 memory, the whole tamper resistance system will be disable by Microprocessor unlocking technique;
Memories
– 2K or 4K bytes Program memory (OTP, EPROM, FASTROM or ROM) with read-out protection
– 64 bytes RAM
Clock, Reset and Supply Management
– Enhanced reset system
– Low Voltage Detector (LVD) for Safe Reset
– Clock sources: crystal/ceramic resonator or RC network, external clock, backup oscillator (LFAO)
– Oscillator Safeguard (OSG)
– 2 Power Saving Modes: Wait and Stop
Interrupt Management
– 4 interrupt vectors plus NMI and RESET
– 20 external interrupt lines (on 2 vectors)
– 1 external non-interrupt line
– 20 multifunctional bidirectional I/O lines
– 16 alternate function lines
– 4 high sink outputs (20mA)
– Configurable watchdog timer
– 8-bit timer/counter with a 7-bit prescaler
Analog Peripheral
– 8-bit ADC with 16 input channels
Instruction Set
– 8-bit data manipulation
– 40 basic instructions
– 9 addressing modes
– Bit manipulation
The ST6215C, 25C devices are low cost members mable option bytes of the OTP/EPROM versions of the ST62xx 8-bit family of microcontrol-in the ROM option list applications. All ST62xx devices are based on a building block approach: a common core is surrounded by a number of on-chip peripherals for the purpose of IC program hacking.
Circuit Engineering Company Limited continues to be recognized as the Southern China Leader in Services for IC Break, MCU attack, Chip Recover, Microcontroller Copy service. With the advancement of today’s modern circuit board technology, it is more important than ever to have specialists available to help you at a moment’s notice. Our engineering and commercial teams collectively have a vast amount of electronic experience covering field include Consumer Electronics, Industrial Automation Electronics, Wireless Communication Electronics., etc. For more information please contact us through email.
 Attack MCU MSP430G2452IPW14R Heximal
Attack MCU MSP430G2452IPW14R Heximal
Attack MCU MSP430G2452IPW14R Hexadecimal: Firmware Extraction and Reverse Engineering
The MSP430G2452IPW14R is a low-power microcontroller from Texas Instruments, widely used in embedded systems. However, its flash memory and EEPROM memory can be targeted for firmware extraction, reverse engineering, or cloning. This article explores methods to crack, decode, and dump the hexadecimal data from this MCU.
MSP430G2452IPW14R è un microcontrollore a bassa potenza di Texas Instruments, ampiamente utilizzato nei sistemi embedded. Tuttavia, la sua memoria flash e la sua memoria EEPROM possono essere prese di mira per l’estrazione del firmware, il reverse engineering o la clonazione. Questo articolo esplora i metodi per crackare, decodificare e scaricare i dati esadecimali da questa MCU.
Dumping Firmware from Flash Memory
To extract the program file from the MSP430G2452IPW14R, attackers often use JTAG or SBW (Spy-Bi-Wire) interfaces. By connecting a programmer like the MSP-FET or a universal flash tool, the binary code can be read out and saved as a hex file. Some advanced techniques involve power glitching or timing attacks to bypass security fuses.
Decrypting and Reverse Engineering
Once the heximal data is dumped, the next step is decoding the firmware. Since the MSP430 uses a 16-bit RISC architecture, disassemblers like IDA Pro or Ghidra can help reverse engineer the source code. If the firmware is encrypted, brute-force attacks or side-channel analysis may be required to crack the protection.
MSP430G2452IPW14R से प्रोग्राम फ़ाइल को निकालने के लिए, हमलावर अक्सर JTAG या SBW (स्पाई-बाय-वायर) इंटरफेस का उपयोग करते हैं। MSP-FET या यूनिवर्सल फ्लैश टूल जैसे प्रोग्रामर को कनेक्ट करके, बाइनरी कोड को पढ़ा जा सकता है और हेक्स फ़ाइल के रूप में सहेजा जा सकता है। कुछ उन्नत तकनीकों में सुरक्षा फ़्यूज़ को बायपास करने के लिए पावर ग्लिचिंग या टाइमिंग अटैक शामिल हैं।
Cloning and Firmware Restoration
After successful decryption, the binary archive can be copied to another MSP430 chip, enabling cloning of the original device. Some attackers decapsulate the MCU to perform microprobing on the flash memory for direct data extraction.
Security Countermeasures
To prevent such attacks, developers should:
Enable read-out protection bits
Use encrypted firmware updates
Implement secure bootloaders
Despite these measures, skilled attackers can still break the security using advanced reverse engineering techniques. Therefore, protecting sensitive hexadecimal firmware remains a critical challenge in embedded security.
By understanding these attack vectors, engineers can better defend against firmware theft and unauthorized cloning of the MSP430G2452IPW14R.

Attack MCU MSP430G2452IPW14R flash memory and extract heximal from Microcontroller MSP430G2452, the status of Microprocessor will be reset from locked to open one after get access to the databus
Attack MCU MSP430G2452IPW14R flash memory and extract heximal from Microcontroller MSP430G2452, the status of Microprocessor will be reset from locked to open one after get access to the databus;
FEATURES
Low Supply Voltage Range: 1.8 V to 3.6 V
Ultra-Low Power Consumption
– Active Mode: 220 µA at 1 MHz, 2.2 V
– Standby Mode: 0.5 µA
– Off Mode (RAM Retention): 0.1 µA
Five Power-Saving Modes
Ultra-Fast Wake-Up From Standby Mode in Less Than 1 µs
16-Bit RISC Architecture, 62.5-ns Instruction Cycle Time Basic Clock Module Configurations
– Internal Frequencies up to 16 MHz With
Four Calibrated Frequencies
– Internal Very-Low-Power Low-Frequency (LF) Oscillator
– 32-kHz Crystal
– External Digital Clock Source
One 16-Bit Timer_A With Three Capture/Compare Registers

След като шестнадесетичните данни бъдат изхвърлени, следващата стъпка е декодирането на фърмуера. Тъй като MSP430 използва 16-битова RISC архитектура, дизасемблери като IDA Pro или Ghidra могат да помогнат за обратното проектиране на изходния код. Ако фърмуерът е криптиран, може да са необходими груби атаки или анализ на страничния канал, за да се пробие защитата.
Up to 16 Touch-Sense Enabled I/O Pins
Universal Serial Interface (USI) Supporting SPI and I2C
10-Bit 200-ksps Analog-to-Digital (A/D)
Converter With Internal Reference, Sample-and-Hold, and Autoscan (MSP430G2x52 Only)
On-Chip Comparator for Analog
Brownout Detector Serial Onboard Programming,
No External Programming Voltage Needed,
Programmable Code Protection by Security Fuse
On-Chip Emulation Logic With Spy-Bi-Wire Interface
Family Members are Summarized in Table 1 Package Options
– TSSOP: 14 Pin, 20 Pin
– PDIP: 20 Pin
– QFN: 16 Pin
For Complete Module Descriptions, See the MSP430x2xx Family User’s Guide (SLAU144)