Reverse Engineering Microcontroller PIC16C558A Eeprom
Reverse Engineering Microcontroller PIC16C558A Eeprom
Microcontrollers like the PIC16C558A store critical firmware and data in their internal EEPROM, often under protective security measures to prevent unauthorized access. However, in various scenarios—such as legacy system recovery, security analysis, or system optimization—it becomes necessary to restore, decrypt, or duplicate the locked firmware for further use. We specialize in Reverse Engineering Microcontroller PIC16C558A EEPROM, offering professional solutions to decode and clone its embedded program.

Az olyan mikrokontrollerek, mint a PIC16C558A, a kritikus firmware-t és adatokat belső EEPROM-jukban tárolják, gyakran biztonsági intézkedések mellett, hogy megakadályozzák az illetéktelen hozzáférést. Különféle forgatókönyvek esetén azonban – például a régi rendszer-helyreállításban, biztonsági elemzésben vagy rendszeroptimalizálásban – szükségessé válik a zárolt firmware visszaállítása, visszafejtése vagy másolása a további használathoz. Szakterületünk a PIC16C558A EEPROM Reverse Engineering mikrokontroller, amely professzionális megoldásokat kínál a beágyazott program dekódolására és klónozására.
Unlocking Protected PIC16C558A EEPROM
The PIC16C558A EEPROM is designed with secured features to prevent unauthorized access, but our advanced firmware decryption and binary analysis techniques allow us to attack these security barriers and retrieve the original heximal source code. Using specialized hardware and software tools, we can copy, extract, and restore the flash memory, providing a complete binary file for modification or further study.

PIC16C558A EEPROM разработан с защищенными функциями для предотвращения несанкционированного доступа, но наши передовые методы дешифрования прошивки и двоичного анализа позволяют нам атаковать эти барьеры безопасности и извлекать исходный шестнадцатеричный код. Используя специализированные аппаратные и программные инструменты, мы можем копировать, извлекать и восстанавливать флэш-память, предоставляя полный двоичный файл для модификации или дальнейшего изучения.
Our Expertise in Microcontroller Hacking and Cloning
- EEPROM Data Extraction – We use cutting-edge techniques to unlock and decrypt the secured firmware stored in flash memory.
- Reverse Engineering & Decompilation – Our team converts binary code into readable source code, making it easier to analyze and modify.
- Firmware Duplication & Cloning – Whether you need to duplicate, clone, or open an archived program, we ensure high accuracy and reliability.
- Security Research & Debugging – Identifying vulnerabilities in protected microcontrollers is crucial for debugging and cybersecurity assessments.

Nossa experiência em hacking e clonagem de microcontroladores
Extração de dados EEPROM – Usamos técnicas de ponta para desbloquear e descriptografar o firmware protegido armazenado na memória flash.
Engenharia reversa e descompilação – Nossa equipe converte código binário em código-fonte legível, facilitando a análise e a modificação.
Duplicação e clonagem de firmware – Se você precisa duplicar, clonar ou abrir um programa arquivado, garantimos alta precisão e confiabilidade.
Pesquisa e depuração de segurança – Identificar vulnerabilidades em microcontroladores protegidos é crucial para avaliações de depuração e segurança cibernética.
Why Choose Us?
- Proven expertise in microcontroller reverse engineering
- Advanced tools for breaking encrypted EEPROM firmware
- Confidential and secure services tailored to client needs
At [Your Company Name], we help you crack, copy, and decrypt PIC16C558A EEPROM firmware with precision. Contact us today to discuss your project and recover valuable memory files from locked microcontrollers!
The clock input (OSC1/CLKIN pin) is internally divided by four to generate four non-overlapping quadrature clocks namely Q1, Q2, Q3 and Q4. Internally, the program counter (PC) is incremented every Q1 if Reverse Engineering Microcontroller PIC16C558A Eeprom, the instruction is fetched from the program memory and latched into the instruction register in Q4. The instruction is decoded and executed during the following Q1 through Q4..
An “Instruction Cycle” consists of four Q cycles (Q1, Q2, Q3 and Q4). The instruction fetch and execute are pipelined such that fetch takes one instruction cycle while decode and execute takes another instruction cycle similar to the process of Reverse Engineering Microcontroller PIC16F73 Program.

Reverse Engineering Microcontroller PIC16C558A Eeprom
However, due to the pipelining, each instruction effectively executes in one cycle. If an instruction causes the program counter to change (e.g., GOTO) then two cycles are required to complete the instruction (Example 3-1) after Reverse engineering Microcontroller. A fetch cycle begins with the program counter (PC) incrementing in Q1.
In the execution cycle, the fetched instruction is latched into the “Instruction Register (IR)” in cycle Q1. This instruction is then decoded and executed during the Q2, Q3, and Q4 cycles. Data memory is read during Q2 (operand read) and written during Q4 (destination write).
The PIC16C55X(A) has a 13-bit program counter capable of addressing an 8K x 14 program memory space. Only the first 512 x 14 (0000h – 01FFh) for the PIC16C554(A), 1K x 14 (0000h – 03FFh) for the PIC16C556A and 2K x 14 (0000h – 07FFh) for the PIC16C558(A) are physically implemented.
Accessing a location above these boundaries will cause a wrap-around within the first 512 x 14 space PIC16C554(A) or 1K x 14 space PIC16C556A or 2K x 14 space PIC16C558(A). The reset vector is at 0000h and the interrupt vector is at 0004h when Recover MCU PIC16F74A Binary.
The data memory (Figure 4-4 and Figure 4-5) is partitioned into two Banks which contain the general purpose registers and the special function registers. Bank 0 is selected when the RP0 bit is cleared. Bank 1 is selected when the RP0 bit (STATUS <5>) is set.
The Special Function Registers are located in the first 32 locations of each Bank. Register locations 20-6Fh (Bank0) on the PIC16C554(A)/556A and 20-7Fh (Bank0) and A0-BFh (Bank1) on the PIC16C558(A) are general purpose registers implemented as static RAM when Reverse Engineering Microcontroller PIC16C558A Eeprom. Some special purpose registers are mapped in Bank 1
 Break IC PIC16C556A Softwares
Break IC PIC16C556A Softwares
Break IC PIC16C556A Software: Reverse Engineering and Extraction
The PIC16C556A is a secured microcontroller (MCU) developed by Microchip, designed for embedded applications with high-security requirements. However, in cases where firmware recovery, replication, or reverse engineering is necessary, specialized techniques are required to extract, copy, or decrypt its internal memory.
PIC16C556A হল মাইক্রোচিপ দ্বারা তৈরি একটি সুরক্ষিত মাইক্রোকন্ট্রোলার (MCU), যা উচ্চ-নিরাপত্তা প্রয়োজনীয়তা সহ এমবেডেড অ্যাপ্লিকেশনগুলির জন্য ডিজাইন করা হয়েছে। তবে, যেখানে ফার্মওয়্যার পুনরুদ্ধার, প্রতিলিপি বা বিপরীত প্রকৌশল প্রয়োজন, সেখানে এর অভ্যন্তরীণ মেমরি এক্সট্র্যাক্ট, কপি বা ডিক্রিপ্ট করার জন্য বিশেষ কৌশল প্রয়োজন।
Understanding the PIC16C556A Security Features
The PIC16C556A features various protection mechanisms, including locked EEPROM, encrypted flash memory, and secured program data to prevent unauthorized access. Manufacturers use these security measures to protect intellectual property, but for legacy system recovery, forensic analysis, or duplication for industrial purposes, it becomes essential to break, attack, or decrypt the chip’s firmware.
Methods to Break PIC16C556A Software
Several advanced hardware and software techniques are available to extract, dump, or clone the data from a protected PIC16C556A microcontroller:
- Decapsulation and Physical Analysis
This method involves chemically or mechanically removing the chip’s protective layer to directly access the die. It allows probing the internal circuits to recover firmware, EEPROM, and flash memory content. - Voltage and Clock Glitching
By introducing sudden voltage fluctuations or clock glitches, the chip’s security mechanisms can be bypassed to extract the locked program or binary data. - Microprobing and Fault Injection
This technique enables direct access to the memory bus, allowing engineers to copy, decrypt, or dump protected files stored in the MCU. - Software Exploitation and Reverse Engineering
Firmware extraction can sometimes be achieved through vulnerabilities in the binary code, program archives, or encryption algorithms used in the chip’s architecture.
Có một số kỹ thuật phần cứng và phần mềm tiên tiến để trích xuất, đổ hoặc sao chép dữ liệu từ vi điều khiển PIC16C556A được bảo vệ:
Phân tách và phân tích vật lýPhương pháp này liên quan đến việc loại bỏ lớp bảo vệ của chip bằng phương pháp hóa học hoặc cơ học để truy cập trực tiếp vào khuôn. Phương pháp này cho phép thăm dò các mạch bên trong để khôi phục chương trình cơ sở, EEPROM và nội dung bộ nhớ flash.
Lỗi điện áp và xung nhịpBằng cách đưa vào các biến động điện áp đột ngột hoặc lỗi xung nhịp, các cơ chế bảo mật của chip có thể bị bỏ qua để trích xuất chương trình hoặc dữ liệu nhị phân bị khóa.
Dò vi mô và tiêm lỗiKỹ thuật này cho phép truy cập trực tiếp vào bus bộ nhớ, cho phép các kỹ sư sao chép, giải mã hoặc đổ các tệp được bảo vệ được lưu trữ trong MCU.
Khai thác phần mềm và kỹ thuật đảo ngượcĐôi khi có thể thực hiện trích xuất chương trình cơ sở thông qua các lỗ hổng trong mã nhị phân, kho lưu trữ chương trình hoặc thuật toán mã hóa được sử dụng trong kiến trúc của chip.
Conclusion
Breaking or hacking the PIC16C556A chip requires specialized tools and expertise in reverse engineering and security analysis. If you need assistance with firmware recovery, microcontroller cloning, or data extraction, our expert team can help with a tailored approach to safely retrieve your secured firmware and ensure your project’s continuity.
A PIC16C556A chip feltörése vagy feltörése speciális eszközöket és szakértelmet igényel a visszafejtés és a biztonsági elemzés terén. Ha segítségre van szüksége a firmware helyreállításában, a mikrokontroller klónozásában vagy az adatok kinyerésében, szakértői csapatunk személyre szabott megközelítéssel segít a védett firmware biztonságos visszanyerésében és a projekt folytonosságának biztosításában.
We can Break IC PIC16C556A Softwares, please view the IC PIC16C556A features for your reference:
Table 1-1 shows the features of the PIC16C55X(A) mid-range microcontroller families. A simplified block diagram of the PIC16C55X(A) is shown in below Figure.
Break IC PIC16C556A Softwares
The PIC16C55X(A) series fit perfectly in applications ranging from motor control to low-power remote sensors. The EPROM technology makes customization of application programs (detection levels, pulse generation, timers, etc.) extremely fast and convenient.
The small footprint packages make this microcontroller series perfect for all applications with space limitations. Low-cost, low-power, high-performance, ease of use and I/O flexibility make the PIC16C55X(A) very versatile.
Those users familiar with the PIC16C5X family of microcontrollers will realize that this is an enhanced version of the PIC16C5X architecture. Please refer to Appendix A for a detailed list of enhancements. Code written for PIC16C5X can be easily ported to PIC16C55X(A) family of devices (Appendix B) after Break IC PIC16C556A Softwares.
The PIC16C55X(A) family fills the niche for users wanting to migrate up from the PIC16C5X family and not needing various peripheral features of other members of the PIC16XX mid-range microcontroller family.
The PIC16C55X(A) family is supported by a full-featured macro assembler, a software simulator, an in-circuit emulator, a low-cost development programmer and a full-featured programmer. A “C” compiler and fuzzy logic support tools are also available after the completion of MCU Crack.
A variety of frequency ranges and packaging options are available. Depending on application and production requirements the proper device option can be selected using the information in the PIC16C55X(A) Product Identification System section at the end of this datasheet to Break Chip PIC16F720 Firmware. When placing orders, please use this page of the data sheet to specify the correct part number.
 Recover Chip PIC16C554A Eeprom
Recover Chip PIC16C554A Eeprom
The PIC16C55X(A) are 18 and 20-Pin EPROM-based members of the versatile PIC16CXX family of low-cost, high-performance, CMOS, fully-static, 8-bit microcontrollers. All PICmicro™ microcontrollers employ an advanced RISC architecture. The PIC16C55X(A) have enhanced core features, eight-level deep stack, and multiple internal and external interrupt sources which is critical for Recover Chip PIC16C554A Eeprom. The separate instruction and data buses of the Harvard architecture allow a 14-bit wide instruction word with the separate 8-bit wide data.
1. चिप पहचान और विश्लेषण
हम माइक्रोकंट्रोलर संस्करण की पहचान करके, मेमोरी संरचना का विश्लेषण करके और सक्रिय सुरक्षा लॉक की जाँच करके शुरू करते हैं। यह चरण संरक्षित डेटा को डिक्रिप्ट और निकालने के लिए सबसे अच्छी विधि निर्धारित करने में मदद करता है।
2. सुरक्षित EEPROM डेटा पढ़ना
विशेष चिप प्रोग्रामर का उपयोग करके, हम मानक और उन्नत निष्कर्षण तकनीकों दोनों के माध्यम से EEPROM और फ्लैश मेमोरी को पढ़ने का प्रयास करते हैं। यदि डेटा लॉक या एन्क्रिप्टेड है, तो हम उन्नत हैकिंग और डिकोडिंग विधियों पर आगे बढ़ते हैं।
3. सुरक्षा सुरक्षा को दरकिनार करना
PIC16C554A के सुरक्षा फ़्यूज़ फ़र्मवेयर स्रोत कोड, बाइनरी फ़ाइलों या EEPROM अभिलेखागार तक सीधी पहुँच को रोकते हैं। हमारे विशेषज्ञ निम्न के संयोजन का उपयोग करते हैं:
मेमोरी को अनलॉक करने के लिए चिप को धोखा देने के लिए वोल्टेज गड़बड़ाना
आंतरिक सर्किटरी तक भौतिक रूप से पहुँचने के लिए डिकैपिंग तकनीकें
निष्पादन का अनुकरण करने और सुरक्षित डेटा को पुनः प्राप्त करने के लिए फ़र्मवेयर इम्यूलेशन
4. डेटा निष्कर्षण और क्लोनिंग
एक बार जब सुरक्षित फ़र्मवेयर और EEPROM फ़ाइलों तक पहुँच हो जाती है, तो हम बाइनरी और हेक्सिमल डेटा को पढ़ने योग्य प्रारूप में डिक्रिप्ट, कॉपी और डुप्लिकेट करते हैं। यह क्लाइंट को खोई हुई फ़ाइलों को पुनर्स्थापित करने, फ़र्मवेयर व्यवहार का विश्लेषण करने या एम्बेडेड प्रोग्राम को संशोधित करने की अनुमति देता है।
5. रीप्रोग्रामिंग और बहाली
सफल EEPROM रिकवरी के बाद, निकाले गए डेटा को किसी अन्य संगत PIC16C554A माइक्रोकंट्रोलर पर रीफ्लैश, रिस्टोर या क्लोन किया जा सकता है। यह सिस्टम रिपेयर, फ़र्मवेयर अपग्रेड और कस्टम एम्बेडेड सॉल्यूशन विकसित करने के लिए उपयोगी है।
The two-stage instruction pipeline allows all instructions to execute in a single-cycle, except for program branches (which require two cycles). A total of 35 instructions (reduced instruction set) are available. Additionally, a large register set gives some of the architectural innovations used to achieve a very high performance after Crack MCU.
PIC16C55X(A) microcontrollers typically achieve a 2:1 code compression and a 4:1 speed improvement over other 8-bit microcontrollers in their class. The PIC16C554(A) and PIC16C556A have 80 bytes of RAM. The PIC16C558(A) has 128 bytes of RAM. Each device has 13 I/O pins and an 8-bit timer/counter with an 8-bit programmable prescaler.
PIC16C55X(A) devices have special features to reduce external components, thus reducing cost, enhancing system reliability and reducing power consumption. There are four oscillator options, of which the single pin RC oscillator provides a low-cost solution, the LP oscillator minimizes power consumption, XT is a standard crystal, and the HS is for High Speed crystals in order to Break MCU PIC16F946 Program. The SLEEP (power-down) mode offers power saving.
![Der Mikrocontroller PIC16C554A wird aufgrund seiner Zuverlässigkeit, seines geringen Stromverbrauchs und seiner vielseitigen Flash-Speicherarchitektur häufig in eingebetteten Systemen eingesetzt. Ist sein EEPROM-Speicher jedoch gesperrt, verschlüsselt oder geschützt, wird der Zugriff auf die gespeicherte Firmware, Binärdateien oder Programmdaten zu einer Herausforderung. [Ihr Firmenname] ist auf Reverse Engineering, Cracking und Entschlüsselung gesicherter Mikrocontroller spezialisiert und bietet Ihnen Expertendienste zur Wiederherstellung und Duplizierung der im PIC16C554A EEPROM gespeicherten Daten.](https://www.ic-crack.com/wp-content/uploads/2015/03/微信图片_20250217164113-300x112.png)
Der Mikrocontroller PIC16C554A wird aufgrund seiner Zuverlässigkeit, seines geringen Stromverbrauchs und seiner vielseitigen Flash-Speicherarchitektur häufig in eingebetteten Systemen eingesetzt. Ist sein EEPROM-Speicher jedoch gesperrt, verschlüsselt oder geschützt, wird der Zugriff auf die gespeicherte Firmware, Binärdateien oder Programmdaten zu einer Herausforderung. [Ihr Firmenname] ist auf Reverse Engineering, Cracking und Entschlüsselung gesicherter Mikrocontroller spezialisiert und bietet Ihnen Expertendienste zur Wiederherstellung und Duplizierung der im PIC16C554A EEPROM gespeicherten Daten.
A UV-erasable CERDIP-packaged version is ideal for code development while the cost-effective One-Time Programmable (OTP) version is suitable for production in any volume to faciliate the process of Break IC PIC16F917 Heximal.
![PIC16C554A माइक्रोकंट्रोलर अपनी विश्वसनीयता, कम बिजली की खपत और बहुमुखी फ्लैश मेमोरी आर्किटेक्चर के कारण एम्बेडेड सिस्टम में व्यापक रूप से उपयोग किया जाता है। हालाँकि, जब इसकी EEPROM मेमोरी लॉक, एन्क्रिप्टेड या संरक्षित होती है, तो संग्रहीत फ़र्मवेयर, बाइनरी फ़ाइलें या प्रोग्राम डेटा तक पहुँचना एक चुनौती बन जाती है। [आपकी कंपनी का नाम] में, हम रिवर्स इंजीनियरिंग, क्रैकिंग और सुरक्षित माइक्रोकंट्रोलर को डिक्रिप्ट करने में विशेषज्ञ हैं, जो PIC16C554A EEPROM में संग्रहीत डेटा को पुनर्प्राप्त करने, पुनर्स्थापित करने और डुप्लिकेट करने के लिए विशेषज्ञ सेवाएँ प्रदान करते हैं।](https://www.ic-crack.com/wp-content/uploads/2015/03/v2-af3d082248d7e9e2174ebe8ee0dbe000_r-1-300x225.jpg)
PIC16C554A माइक्रोकंट्रोलर अपनी विश्वसनीयता, कम बिजली की खपत और बहुमुखी फ्लैश मेमोरी आर्किटेक्चर के कारण एम्बेडेड सिस्टम में व्यापक रूप से उपयोग किया जाता है। हालाँकि, जब इसकी EEPROM मेमोरी लॉक, एन्क्रिप्टेड या संरक्षित होती है, तो संग्रहीत फ़र्मवेयर, बाइनरी फ़ाइलें या प्रोग्राम डेटा तक पहुँचना एक चुनौती बन जाती है। [आपकी कंपनी का नाम] में, हम रिवर्स इंजीनियरिंग, क्रैकिंग और सुरक्षित माइक्रोकंट्रोलर को डिक्रिप्ट करने में विशेषज्ञ हैं, जो PIC16C554A EEPROM में संग्रहीत डेटा को पुनर्प्राप्त करने, पुनर्स्थापित करने और डुप्लिकेट करने के लिए विशेषज्ञ सेवाएँ प्रदान करते हैं।
 Reverse Engineering Microcontroller PIC16C554 Software
Reverse Engineering Microcontroller PIC16C554 Software
We can Reverse engineering Microcontroller PIC16C554 Software, please view the Microcontroller PIC16C554 features for your reference:
High Performance RISC CPU:
· Only 35 instructions to learn
· All single-cycle instructions (200 ns), except for program branches which are two-cycle
· Operating speed:
– DC – 20 MHz clock input
– DC – 200 ns instruction cycle
फ़र्मवेयर एक्सट्रैक्शन – विशेष हार्डवेयर और सॉफ़्टवेयर टूल का उपयोग करके, हम माइक्रोकंट्रोलर से लॉक किए गए फ़्लैश और EEPROM मेमोरी को कॉपी और डिक्रिप्ट करते हैं, जिससे इसमें संग्रहीत बाइनरी या हेक्सिमल प्रोग्राम की पूरी पुनर्प्राप्ति सुनिश्चित होती है।
बाइनरी विश्लेषण और डिसअसेम्बली – एक बार निकाले जाने के बाद, फ़र्मवेयर बाइनरी का सावधानीपूर्वक विश्लेषण किया जाता है, असेंबली भाषा में डिसअसेम्बल किया जाता है, और अधिक पठनीय प्रारूप में परिवर्तित किया जाता है। यह चरण हमें एन्क्रिप्टेड इंस्ट्रक्शन सेट को डिकोड करने और सोर्स कोड संरचना को फिर से बनाने में मदद करता है।
डिकंपाइलेशन और कोड पुनर्निर्माण – उन्नत डिकंपाइलेशन तकनीकों को लागू करके, हम संरक्षित प्रोग्राम को C-जैसे सोर्स कोड प्रारूप में पुनर्स्थापित करते हैं, जिससे नए हार्डवेयर प्लेटफ़ॉर्म के लिए एम्बेडेड सॉफ़्टवेयर को संशोधित, अनुकूलित या क्लोन करना आसान हो जाता है।
रीप्रोग्रामिंग और डुप्लीकेशन – रिवर्स इंजीनियरिंग के बाद, हम माइक्रोकंट्रोलर फ़र्मवेयर को डुप्लिकेट कर सकते हैं, जिससे क्लाइंट बैकअप कॉपी बना सकते हैं, सुरक्षित प्रोग्राम को क्लोन कर सकते हैं या इसे किसी अन्य संगत डिवाइस में स्थानांतरित कर सकते हैं।
16 special function hardware registers can help to IC program crack
Special Microcontroller Features (cont’d)
8-level deep hardware stack
Direct, Indirect and Relative addressing modes
Programmable code protection against Extract IC program
Power saving SLEEP mode
Peripheral Features:
· 13 I/O pins with individual direction control
· High current sink/source for direct LED drive Selectable oscillator options Serial in-circuit programming (via two pins) Four user programmable ID locations
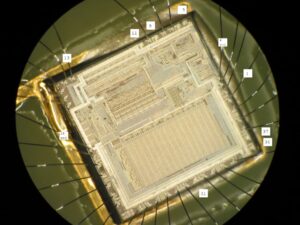
Firmware-Extraktion – Mithilfe spezieller Hard- und Softwaretools kopieren und entschlüsseln wir den gesperrten Flash- und EEPROM-Speicher des Mikrocontrollers und stellen so die vollständige Wiederherstellung des darin gespeicherten Binär- oder Hexadezimalprogramms sicher.
Binäranalyse und -disassemblierung – Nach der Extraktion wird die Firmware-Binärdatei sorgfältig analysiert, in Assemblersprache disassembliert und in ein besser lesbares Format konvertiert. Dieser Schritt hilft uns, den verschlüsselten Befehlssatz zu entschlüsseln und die Quellcodestruktur zu rekonstruieren.
Dekompilierung und Code-Rekonstruktion – Durch den Einsatz fortschrittlicher Dekompilierungstechniken stellen wir das geschützte Programm in ein C-ähnliches Quellcodeformat wieder her. Dies erleichtert die Änderung, Optimierung oder das Klonen der eingebetteten Software für neue Hardwareplattformen.
Neuprogrammierung und -duplizierung – Nach dem Reverse Engineering können wir die Mikrocontroller-Firmware duplizieren, sodass Kunden Sicherungskopien erstellen, das gesicherte Programm klonen oder auf ein anderes kompatibles Gerät übertragen können.
· Timer0: 8-bit timer/counter with 8-bit programmable prescaler
Special Microcontroller Features:
· Power-on Reset (POR)
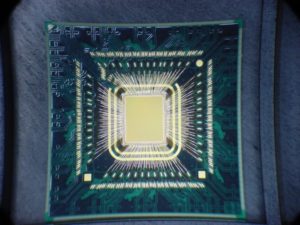
Reverse Engineering Microcontroller PIC16C554 Software
· Power-up Timer (PWRT) and Oscillator Start-up Timer (OST)
· Watchdog Timer (WDT) with its own on-chip RC oscillator for reliable operation
CMOS Technology:
· Low-power, high-speed CMOS EPROM technology
· Fully static design
· Wide operating voltage range
– 2.5V to 5.5V PIC16C55X
– 3.0 to 5.5V PIC16C55XA
· Commercial, industrial and extended temperature range
· Low power consumption
– < 2.0 mA @ 5.0V, 4.0 MHz
– 15 µA typical @ 3.0V, 32 kHz
– < 1.0 µA typical standby current @ 3.0V
Circuit Engineering Company Limited continues to be recognized as the Southern China Leader in Services for IC Read, MCU Crack, Chip Reverse engineering, Microcontroller Unlock service. With the advancement of today’s modern circuit board technology, it is more important than ever to have specialists available to help you at a moment’s notice. Our engineering and commercial teams collectively have a vast amount of electronic experience covering field include Consumer Electronics, Industrial Automation Electronics, Wireless Communication Electronics., etc. For more information please contact us through email.

펌웨어 추출 – 특수 하드웨어 및 소프트웨어 도구를 사용하여 마이크로컨트롤러에서 잠긴 플래시 및 EEPROM 메모리를 복사하고 해독하여 내부에 저장된 바이너리 또는 16진수 프로그램을 완전히 검색합니다.
바이너리 분석 및 분해 – 추출된 펌웨어 바이너리는 신중하게 분석되고 어셈블리 언어로 분해되어 더 읽기 쉬운 형식으로 변환됩니다. 이 단계는 암호화된 명령어 세트를 디코딩하고 소스 코드 구조를 재구성하는 데 도움이 됩니다.
디컴파일 및 코드 재구성 – 고급 디컴파일 기술을 적용하여 보호된 프로그램을 C와 유사한 소스 코드 형식으로 복원하여 새로운 하드웨어 플랫폼에 대한 임베디드 소프트웨어를 수정, 최적화 또는 복제하는 것을 더 쉽게 만듭니다.
재프로그래밍 및 복제 – 리버스 엔지니어링 후 마이크로컨트롤러 펌웨어를 복제하여 클라이언트가 백업 사본을 만들거나 보안된 프로그램을 복제하거나 다른 호환 장치로 전송할 수 있습니다.
 Recover MCU PIC16CR84 Code
Recover MCU PIC16CR84 Code
We can Recover MCU PIC16CR84 Code, please view the MCU PIC16CR84 features for your reference:
A variety of frequency ranges and packaging options are available. Depending on application and production requirements the proper device option can be selected using the information in this section.
When placing orders, please use the “PIC16F8X Product Identification System” at the back of this data sheet to specify the correct part number.
There are four device “types” as indicated in the device number.
1. F, as in PIC16F84. These devices have Flash program memory and operate over the standard voltage range after Attack MCU firmware.
2. LF, as in PIC16LF84. These devices have Flash program memory and operate over an extended voltage range.
3. CR, as in PIC16CR83. These devices have ROM program memory and operate over the standard voltage range.
4. LCR, as in PIC16LCR84. These devices have ROM program memory and operate over an extended voltage range.
When discussing memory maps and other architectural features, the use of F and CR also implies the LF and LCR versions.
2.1 Flash Devices
These devices are offered in the lower cost plastic package, even though the device can be erased and reprogrammed. This allows the same device to be used for prototype development and pilot programs as well as production after Recover MCU.
A further advantage of the electrically-erasable Flash version is that it can be erased and reprogrammed in-circuit, or by device programmers, such as Microchip’s PICSTART® Plus or PRO MATE® II programmers.
2.2 Quick-Turnaround-Production (QTP) Devices
Microchip offers a QTP Programming Service for factory production orders. This service is made available for users who choose not to program a medium to high quantity of units and whose code patterns have stabilized.
The devices have all Flash locations and configuration options already programmed by the factory. Certain code and prototype verification procedures do apply before production shipments are available.
2.3 Serialized Quick-Turnaround-Production (SQTP SM ) Devices
Microchip offers the unique programming service where a few user-defined locations in each device are programmed with different serial numbers. The serial numbers may be random, pseudo-random or sequential if Copy MCU Firmware.
Serial programming allows each device to have a unique number which can serve as an entry-code, password or ID number.
Some of Microchip’s devices have a corresponding device where the program memory is a ROM. These devices give a cost savings over Microchip’s traditional user programmed devices (EPROM, EEPROM).
ROM devices (PIC16CR8X) do not allow serialization information in the program memory space. The user may program this information into the Data EEPROM when Recover MCU PIC16CR84 Code.
The high performance of the PIC16CXX family can be attributed to a number of architectural features commonly found in RISC microprocessors. To begin with, the PIC16CXX uses a Harvard architecture.
This architecture has the program and data accessed from separate memories. So the device has a program memory bus and a data memory bus. This improves bandwidth over traditional von Neumann architecture where program and data are fetched from the same memory (accesses over the same bus).
Separating program and data memory further allows instructions to be sized differently than the 8-bit wide data word. PIC16CXX opcodes are 14-bits wide, enabling single word instructions to Crack MCU.
The full 14-bit wide program memory bus fetches a 14-bit instruction in a single cycle. A two-stage pipeline overlaps fetch and execution of instructions (see below picture).
Consequently, all instructions execute in a single cycle except for program branches.
The PIC16F83 and PIC16CR83 address 512 x 14 of program memory, and the PIC16F84 and PIC16CR84 address 1K x 14 program memory. All program memory is internal.
 Reverse Engineering Microcontroller PIC16CR83 Heximal
Reverse Engineering Microcontroller PIC16CR83 Heximal
We can Reverse Engineering Microcontroller PIC16CR83 Heximal, please view the Microcontroller PIC16CR83 features for your refernece:
A variety of frequency ranges and packaging options are available. Depending on application and production requirements the proper device option can be selected using the information in this section. When placing orders, please use the “PIC16F8X Product Identification System” at the back of this data sheet to specify the correct part number.
There are four device “types” as indicated in the device number.
1. F, as in PIC16F84. These devices have Flash program memory and operate over the standard voltage range.
2. LF, as in PIC16LF84. These devices have Flash;
3. CR, as in PIC16CR83. These devices have ROM program memory and operate over the standard voltage range.
LCR, as in PIC16LCR84. These devices have ROM program memory and operate over an extended voltage range.
When discussing memory maps and other architectural features, the use of F and CR also implies the LF and LCR versions.
These devices are offered in the lower cost plastic package, even though the device can be erased and reprogrammed to ease the process of EPROM advantage when MCU Code Decryption. This allows the same device to be used for prototype development and pilot programs as well as production.

Reverse Engineering Microcontroller PIC16CR83 Heximal
A further advantage of the electrically-erasable Flash version is that it can be erased and reprogrammed in-circuit, or by device programmers, such as Microchip’s PICSTART® Plus or PRO MATE® II programmers.
2.2 Quick-Turnaround-Production (QTP) Devices
Microchip offers a QTP Programming Service for factory production orders. This service is made available for users who choose not to program a medium to high quantity of units and whose code patterns have stabilized. The devices have all Flash locations and configuration options already programmed by the factory. Certain code and prototype verification procedures do apply to IC Code Break’s intermediate approach before production shipments are available.
Microchip offers the unique programming service where a few user-defined locations in each device are programmed with different serial numbers. The serial numbers may be random, pseudo-random or sequential.
Serial programming allows each device to have a unique number which can serve as an entry-code, password or ID number when Crack MCU. Device where the program memory is a ROM. These Some of Microchip’s devices have a corresponding devices give a cost savings over Microchip’s traditional user programmed devices (EPROM, EEPROM). ROM devices (PIC16CR8X) do not allow serialization information in the program memory space. The user may program this information into the Data EEPROM.
 Break IC PIC16F84 Code
Break IC PIC16F84 Code
All PICmicro™ microcontrollers employ an advanced RISC architecture. PIC16F8X devices have enhanced core features, eight-level deep stack, and multiple internal and external interrupt sources which can be applied for Break IC PIC16F84 Code. The separate instruction and data buses of the Harvard architecture allow a 14-bit wide instruction word with a separate 8-bit wide data bus. The two stage instruction pipeline allows all instructions to execute in a single cycle, except for program branches (which require two cycles).
A total of 35 instructions (reduced instruction set) are available. Additionally, a large register set is used to achieve a very high performance level. PIC16F8X microcontrollers typically achieve a 2:1 code compression and up to a 4:1 speed improvement (at 20 MHz) over other 8-bit microcontrollers in their class.
The PIC16F8X has up to 68 bytes of RAM, 64 bytes of Data EEPROM memory, and 13 I/O pins. A timer/counter is also available.
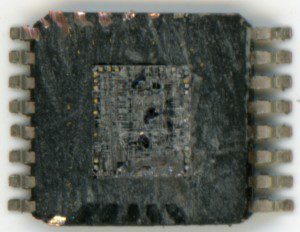
Break IC PIC16F84 Code
The PIC16CXX family has special features to reduce external components, thus reducing cost, enhancing system reliability and reducing power consumption when Break IC PIC16F84 Code.
There are four oscillator options, of which the single pin RC oscillator provides a low-cost solution, the LP oscillator minimizes power consumption, XT is a standard crystal, and the HS is for High Speed crystals when Copy IC PIC16LF877 Program. The SLEEP (power-down) mode offers power saving. The user can wake the chip from sleep through several external and internal interrupts and resets.
A highly reliable Watchdog Timer with its own on-chip RC oscillator provides protection against software lock-up. The devices with Flash program memory allow the same device package to be used for prototyping and production.
In-circuit reprogrammability allows the code to be updated without the device being removed from the end application.
This is useful in the development of many applications where the device may not be easily accessible, but the prototypes may require code updates. This is also useful for remote applications where the code may need to be updated (such as rate information).
The PIC16F8X fits perfectly in applications ranging from high speed automotive and appliance motor control to low-power remote sensors, electronic locks, security devices and smart cards. The Flash/EEPROM technology makes customization of application programs in order to Recover MCU PIC18F452 Program (transmitter codes, motor speeds, receiver frequencies, security codes, etc.) extremely fast and convenient.
The small footprint packages make this microcontroller series perfect for all applications with space limitations. Low-cost, low-power, high performance, ease-of-use and I/O flexibility make the PIC16F8X very versatile even in areas where no microcontroller use has been considered before (e.g., timer functions; serial communication; capture, compare and PWM functions; and co-processor applications). The serial in-system programming feature (via two pins) offers flexibility of customizing the product after complete assembly and testing for the process of Microcontroller Unlocking. This feature can be used to serialize a product, store calibration data, or program the device with the current firmware before shipping.
 Recover MCU PIC16C712 Binary
Recover MCU PIC16C712 Binary
We can Recover MCU PIC16C712 Binary, please view the MCU PIC16C712 features for your reference:
Microcontroller Core Features:
· High-performance RISC CPU
· Only 35 single word instructions to learn
· All single cycle instructions except for program branches which are two cycle
· Operating speed: DC – 20 MHz clock input DC – 200 ns instruction cycle
· Interrupt capability (up to 7 internal/external interrupt sources) which can be applied for Microcontroller Unlocking
· Eight level deep hardware stack
· Direct, indirect and relative addressing modes
· Power-on Reset (POR)
· Power-up Timer (PWRT) and Oscillator Start-up Timer (OST)
· Watchdog Timer (WDT) with its own on-chip RC oscillator for reliable operation
· Brown-out detection circuitry for Brown-out Reset (BOR)
· Programmable code-protection against Break Microcontroller PIC16F886 Software
· Power saving SLEEP mode
· Selectable oscillator options
· Low-power, high-speed CMOS EPROM technology
· Fully static design
· In-Circuit Serial Programming (ICSP)
· Wide operating voltage range: 2.5V to 5.5V
· High Sink/Source Current 25/25 mA
· Commercial, Industrial and Extended temperature ranges
· Low-power consumption:
– < 2 mA @ 5V, 4 MHz
– 22.5 µA typical @ 3V, 32 kHz
– < 1 µA typical standby current
Peripheral Features:
· Timer0: 8-bit timer/counter with 8-bit prescaler
· Timer1: 16-bit timer/counter with prescaler can be incremented during sleep via external crystal/clock
· Timer2: 8-bit timer/counter with 8-bit period register, prescaler and postscaler after Recover IC PIC16C73B Firmware
· Capture, Compare, PWM module
· Capture is 16-bit, max. resolution is 12.5 ns, Compare is 16-bit, max. resolution is 200 ns, PWM maximum resolution is 10-bit
· 8-bit multi-channel Analog-to-Digital converter
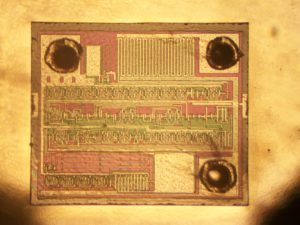
Recover MCU PIC16C712 Binary
This document contains device-specific information. Additional information may be found in the PICmicro™ Mid-Range Reference Manual, (DS33023), which may be obtained from your local Microchip Sales Representative or downloaded from the Microchip website. The Reference Manual should be considered a complementary document to this datasheet, and is highly recommended reading for a better understanding of the device architecture and operation of the peripheral modules.
 Break IC PIC16C771 Firmware
Break IC PIC16C771 Firmware
The Special Function Registers are registers used by the CPU and Peripheral Modules for controlling the desired operation of the device to facilitate the process of Break IC PIC16C771 Firmware. These registers are implemented as static RAM, core (CPU) and peripheral. Those registers associated with the core functions are described in detail in this section. Those related to the operation of the peripheral features are described in detail in that peripheral feature section. For example, CLRF STATUS will clear the upper-three;
The STATUS register, shown in Register 2-1, contains the arithmetic status of the ALU, the RESET status and the bank select bits for data memory.
The STATUS register can be the destination for any instruction, as with any other register. If the STATUS register is the destination for an instruction that affects the Z, DC or C bits, then the write to these three bits is disabled.
These bits are set or cleared according to the device logic. Furthermore, the TO and PD bits are not writable. Therefore, the result of an instruction with the STATUS register as destination may be different than intended.
It is recommended, therefore, that only BCF, BSF, SWAPF and MOVWF instructions are used to alter the STATUS register, because these instructions do not affect the Z, C or DC bits from the STATUS register. For other instructions not affecting any status bits, see the ”Instruction Set Summary.
The program counter (PC) specifies the address of the instruction to fetch for execution. The PC is 13 bits wide. The low byte is called the PCL register. This register is readable and writable in order to Break IC PIC16C771 Firmware. The high byte is called the PCH register. This register contains the PC<12:8> bits and is not directly readable or writable. All updates to the PCH register occur through the PCLATH register.
PIC16C717/770/771 devices are capable of addressing a continuous 8K word block of program memory. The CALL and GOTO instructions provide only 11 bits of address to allow branching within any 2K program memory page. When doing aCALL or GOTO instruction, the upper 2 bits of the address are provided by PCLATH<4:3>. When doing a CALL or GOTO instruction, the user must ensure that the page select bits are programmed so that the desired program memory page is addressed.
A return instruction pops a PC address off the stack onto the PC register. Therefore, manipulation of the PCLATH<4:3> bits are not required for the return instructions (which POPs the address from the stack).

Break IC PIC16C771 Firmware
The stack allows a combination of up to 8 program calls and interrupts to occur. The stack contains the return address from this branch in program execution. Mid-range devices have an 8-level deep x 13-bit wide hardware stack. The stack space is not part of either program or data space and the stack pointer is not readable or writable which is not easy for Recover Chip PIC16F689 Flash. The PC is PUSHed onto the stack when a CALL instruction is executed or an interrupt causes a branch. The stack is POPed in the event of RETURN, RETLW or a RETFIE instruction execution. PCLATH is not modified when the stack is PUSHed or POPed.
After the stack has been PUSHed eight times, the ninth push overwrites the value that was stored from the first push. The tenth push overwrites the second push (and so on).
The INDF register is not a physical register. Addressing INDF actually addresses the register whose address is contained in the FSR register (FSR is a pointer). This is indirect addressing before Microcontroller Unlock.
Reading INDF itself indirectly (FSR = 0) will produce 00h. Writing to the INDF register indirectly results in a no-operation (although STATUS bits may be affected). A simple program to clear RAM locations 20h-2Fh using indirect addressing is shown in Example 2-1 Some pins for these I/O ports are multiplexed with an alternate function for the peripheral features on the device by PIC16F84A Microcontroller Chip Attack. In general, when a peripheral is enabled, that pin may not be used as a general purpose I/O pin.
Additional information on I/O ports may be found in the PICmicro™ Mid-Range Reference Manual, (DS33023).
PORTA is a 8-bit wide bi-directional port. The corre-analog mode of the corresponding pins. sponding data direction register is TRISA. Setting a TRISA bit (=1) will make the corresponding PORTA pin an input, i.e., put the corresponding output driver in a hi-impedance mode. Clearing a TRISA bit (=0) will make the corresponding PORTA pin an output, i.e., put the contents of the output latch on the selected pin.
 Read Chip PIC16C770 Eeprom
Read Chip PIC16C770 Eeprom
This document contains device-specific information and necessary info for Read Chip PIC16C770 Eeprom. Additional information may be found in the PICmicroTM Mid-Range Reference Manual, (DS33023), which may be obtained from your local Microchip Sales Representative or downloaded from the Microchip website.
The Reference Manual should be considered a complementary document to this data sheet, and is highly recommended reading for a better understanding of the device architecture and operation of the peripheral modules.
There are two memory blocks in each of these PICmicro ® microcontrollers. Each block (Program Memory and Data Memory) has its own bus, so that concurrent access can occur. Additional information on device memory may be found in the PICmicro Mid-Range Reference Manual, (DS33023).
The PIC16C770 devices have a 13-bit program counter capable of addressing an 8K x 14 program memory space. The PIC16C717 and the PIC16C770 have 2K x 14 words of program memory by Break IC PIC16F685 Code. The PIC16C771 has 4K x 14 words of program memory. Accessing a location above the physically implemented address will cause a wraparound.
The reset vector is at 0000h and the interrupt vector is at 0004h. Each bank extends up to 7Fh (128 bytes). The lower locations of each bank are reserved for the Special Function Registers. Above the Special Function Registers are General Purpose Registers, implemented as static RAM when Unlock Microcontroller.
All implemented banks contain special function registers. Some frequently used special function registers from one bank are mirrored in another bank for code reduction and quicker access in order to Attack IC PIC12F510 Program. The Special Function Registers are registers used by the CPU and Peripheral Modules for controlling the desired operation of the device. These registers are implemented as static RAM.
The special function registers can be classified into two sets; core (CPU) and peripheral. Those registers associated with the core functions are described in detail in this section. Those related to the operation of the peripheral features are described in detail in that peripheral feature section.