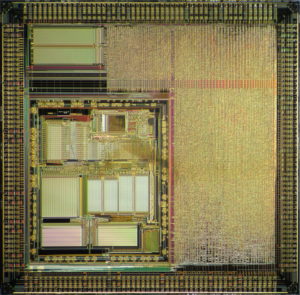
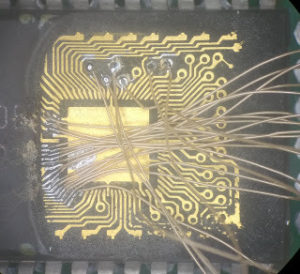
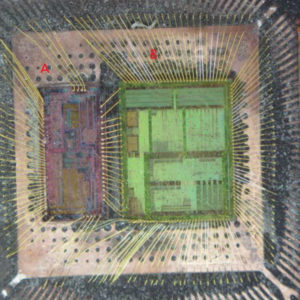
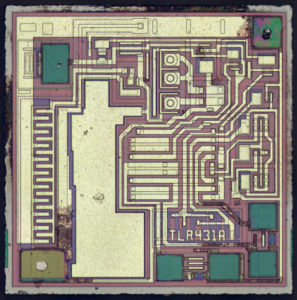
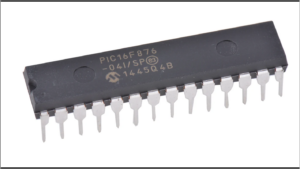
Break MCU PIC16F876 Flash
Break MCU PIC16F876 Flash
Breaking MCU PIC16F876 flash involves cracking the encrypted and secured firmware stored in its flash memory and EEPROM memory. This secured PIC16F876 microcontroller unit (MCU) is often used in embedded systems, where its firmware and software are protected to prevent unauthorized access. When attempting to break the protection, reverse engineering techniques are typically employed to decode or decrypt the encrypted PIC16F876 microprocessor’s locked binary and heximal data within the flash memory.

break MCU PIC16F876 lampu kilat melu retak perangkat kukuh ndhelik lan aman disimpen ing memori lampu kilat lan memori EEPROM. Unit mikrokontroler (MCU) PIC16F876 sing aman iki asring digunakake ing sistem sing dipasang, ing ngendi perangkat kukuh lan piranti lunak dilindhungi kanggo nyegah akses sing ora sah. Nalika nyoba ngrusak proteksi, teknik reverse engineering biasane digunakake kanggo decode utawa dekripsi data biner lan heksimal mikroprosesor PIC16F876 sing dikunci ing memori lampu kilat.
The process begins with analyzing the microprocessor’s architecture to identify and bypass the encryption protocols securing the firmware. Specialized tools are used to attack the encryption and unlock the flash memory, allowing access to the embedded program and source code. Once the protective measures are defeated, the firmware can be restored, cloned, or replicated for system diagnostics, repair, or further development.
Unlocking the PIC16F876 MCU’s flash memory allows for the recovery of critical software, which is particularly useful in situations where the original source code is lost, corrupted, or unavailable. Cloning the firmware ensures that the program can be duplicated for use in similar systems or to create backups for future use.
MCU PIC16F876 ఫ్లాష్ను విచ్ఛిన్నం చేయడంలో దాని ఫ్లాష్ మెమరీ మరియు EEPROM మెమరీలో నిల్వ చేయబడిన ఎన్క్రిప్టెడ్ మరియు సురక్షిత ఫర్మ్వేర్ను క్రాక్ చేయడం ఉంటుంది. ఈ సురక్షిత PIC16F876 మైక్రోకంట్రోలర్ యూనిట్ (MCU) తరచుగా ఎంబెడెడ్ సిస్టమ్లలో ఉపయోగించబడుతుంది, ఇక్కడ అనధికార ప్రాప్యతను నిరోధించడానికి దాని ఫర్మ్వేర్ మరియు సాఫ్ట్వేర్ రక్షించబడతాయి. రక్షణను విచ్ఛిన్నం చేయడానికి ప్రయత్నించినప్పుడు, ఫ్లాష్ మెమరీలో గుప్తీకరించిన PIC16F876 మైక్రోప్రాసెసర్ యొక్క లాక్ చేయబడిన బైనరీ మరియు హెక్సిమల్ డేటాను డీకోడ్ చేయడానికి లేదా డీక్రిప్ట్ చేయడానికి రివర్స్ ఇంజనీరింగ్ పద్ధతులు సాధారణంగా ఉపయోగించబడతాయి.
However, it is crucial to note that breaking the protection of an MCU like the PIC16F876 should be done within legal and ethical boundaries. Unauthorized decryption or cloning of the firmware could lead to intellectual property violations and legal consequences. As such, this process should be carried out responsibly, ensuring the preservation of both the software’s integrity and the rights of the original creators.
The STATUS register contains the arithmetic status of the ALU, the RESET status and the bank select bits for data memory. The STATUS register can be the destination for any instruction, as with any other register. If the STATUS register is the destination for an instruction that affects the Z, DC or C bits, then the write to these three bits is disabled.
These bits are set or cleared according to the device logic. Furthermore, the TO and PD bits are not writable, therefore, the result of an instruction with the STATUS register as destination may be different than intended for the purpose of Break IC SST89E58RD2A Software.
For example, CLRF STATUS will clear the upper three bits and set the Z bit. This leaves the STATUS register as 000u u1uu (where u = unchanged). It is recommended, therefore, that only BCF, BSF, SWAPF and MOVWF instructions are used to alter the STATUS register, because these instructions do not affect the Z, C or DC bits from the STATUS register.
For other instructions not affecting any status bits, see the “Instruction Set Summary.”
The OPTION_REG Register is a breakable and writable register, which contains various control bits to configure the TMR0 prescaler/WDT postscaler (single assignable register known also as the prescaler), the External INT Interrupt, TMR0 and the weak pull-ups on PORTB.

Um den Flash-Speicher des MCU PIC16F876 zu knacken, muss die verschlüsselte und gesicherte Firmware geknackt werden, die in seinem Flash-Speicher und EEPROM-Speicher gespeichert ist. Diese gesicherte Mikrocontrollereinheit (MCU) PIC16F876 wird häufig in eingebetteten Systemen verwendet, in denen die Firmware und Software vor unbefugtem Zugriff geschützt sind. Beim Versuch, den Schutz zu knacken, werden normalerweise Reverse-Engineering-Techniken eingesetzt, um die gesperrten binären und hexadezimalen Daten des verschlüsselten Mikroprozessors PIC16F876 im Flash-Speicher zu dekodieren oder zu entschlüsseln.
The program counter (PC) is 13-bits wide. The low byte comes from the PCL register, which is a breakable and writable register. The upper bits (PC<12:8>) are not breakable, but are indirectly writable through the PCLATH register to facilitate the process of Recover MCU DSPIC30F6013A30IP Firmware. On any RESET, the upper bits of the PC will be cleared. Figure 2-5 shows the two situations for the loading of the PC.
The upper example in the figure shows how the PC is loaded on a write to PCL (PCLATH<4:0> → PCH). The lower example in the figure shows how the PC is loaded during aCALL orGOTO instruction (PCLATH<4:3> → PCH). All PIC16F87X devices are capable of addressing a continuous 8K word block of program memory which is critical for Microcontroller Unlocking.
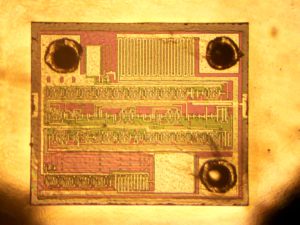
Break IC PIC16F876 Flash
The CALL and GOTO instructions provide only 11 bits of address to allow branching within any 2K program memory page. When doing aCALL or GOTO instruction, the upper 2 bits of the address are provided by PCLATH<4:3>. When doing a CALL or GOTO instruction, the user must ensure that the page select bits are programmed so that the desired program memory page is addressed before Break Mcu PIC16F876 Flash
If a return from a CALL instruction (or interrupt) is executed, the entire 13-bit PC is popped off the stack. Therefore, manipulation of the PCLATH<4:3> bits is not required for the return instructions (which POPs the address from the stack).
 Break IC PIC16F873 Software
Break IC PIC16F873 Software
Breaking IC PIC16F873 software involves a series of techniques aimed at decrypting or cracking the encrypted firmware stored in its flash memory and EEPROM memory. The PIC16F873 microcontroller (MCU) is designed with secured protections that make its software, including binary and heximal data, difficult to access without proper authorization. However, reverse engineering and decryption techniques can be employed to unlock the locked firmware, enabling the extraction of the embedded program or source code for legitimate purposes.

IC PIC16F873 yazılımını kırmak, flaş belleğinde ve EEPROM belleğinde saklanan şifreli aygıt yazılımını şifresini çözmeyi veya kırmayı amaçlayan bir dizi tekniği içerir. Güvenli PIC16F873 mikrodenetleyicisi (MCU), ikili ve onaltılık veriler de dahil olmak üzere yazılımına uygun yetkilendirme olmadan erişilmesini zorlaştıran güvenli korumalarla tasarlanmıştır. Ancak, kilitli mikroişlemci PIC16F873 tersine mühendislik ve şifre çözme teknikleri, kilitli aygıt yazılımını kilidini açmak için kullanılabilir ve gömülü programın veya kaynak kodunun meşru amaçlar için çıkarılmasını sağlar.
To begin the process, an attacker must first analyze the microprocessor’s architecture to understand how the protective mechanisms work. This may include studying the microcomputer’s memory layout, security features, and encryption algorithms. Once the firmware is identified, specialized tools and methods are used to break or crack the encryption, allowing the software to be decoded and recovered.
The goal of breaking the IC PIC16F873 software is often to restore functionality or replicate the program for backup purposes. In some cases, the source code is extracted to troubleshoot issues or enhance the program’s performance. Additionally, when cloning the software for use in other devices, the goal is to duplicate the program exactly as it exists in the original system.
However, it is crucial to note that breaking the software of an MCU like the PIC16F873 must be done within legal and ethical boundaries. Unauthorized access to locked firmware or decryption of encrypted data can violate intellectual property laws and lead to legal consequences.

การทำลายซอฟต์แวร์ IC PIC16F873 เกี่ยวข้องกับเทคนิคชุดหนึ่งที่มุ่งเป้าไปที่การถอดรหัสหรือแคร็กเฟิร์มแวร์ที่เข้ารหัสซึ่งเก็บไว้ในหน่วยความจำแฟลชและหน่วยความจำ EEPROM ไมโครคอนโทรลเลอร์ (MCU) PIC16F873 ที่ปลอดภัยได้รับการออกแบบด้วยการป้องกันที่ปลอดภัยซึ่งทำให้ซอฟต์แวร์ซึ่งรวมถึงข้อมูลไบนารีและเลขฐานสิบหกเข้าถึงได้ยากหากไม่ได้รับอนุญาตอย่างเหมาะสม อย่างไรก็ตาม สามารถใช้เทคนิควิศวกรรมย้อนกลับและการถอดรหัสของไมโครโปรเซสเซอร์ PIC16F873 เพื่อปลดล็อกเฟิร์มแวร์ที่ถูกล็อค ทำให้สามารถแยกโปรแกรมที่ฝังไว้หรือโค้ดต้นฉบับเพื่อวัตถุประสงค์ที่ถูกต้องได้
In summary, breaking the IC PIC16F873 software involves cracking encryption, decoding binary data, and reverse engineering the firmware to access or restore critical software, while always adhering to ethical and legal standards.
We can Break IC PIC16F873 Software, please view the IC PIC16F873 features for your reference:
· High performance RISC CPU
· Only 35 single word instructions to learn
· All single cycle instructions except for program branches which are two cycle
· Operating speed: DC – 20 MHz clock input DC – 200 ns instruction cycle
· Up to 8K x 14 words of FLASH Program Memory, Up to 368 x 8 bytes of Data Memory (RAM) Up to 256 x 8 bytes of EEPROM Data Memory after the process of Break Microcontroller PIC16F767 Firmware
· Pinout compatible to the PIC16C73B/74B/76/77
· Interrupt capability (up to 14 sources)
· Eight level deep hardware stack
· Direct, indirect and relative addressing modes
· Power-on Reset (POR)
· Power-up Timer (PWRT) and Oscillator Start-up Timer (OST)
· Watchdog Timer (WDT) with its own on-chip RC oscillator for reliable operation
· Programmable code protection
· Power saving SLEEP mode

Phá vỡ phần mềm IC PIC16F873 liên quan đến một loạt các kỹ thuật nhằm giải mã hoặc bẻ khóa phần mềm được mã hóa được lưu trữ trong bộ nhớ flash và bộ nhớ EEPROM của nó. Bộ vi điều khiển (MCU) PIC16F873 được bảo mật được thiết kế với các biện pháp bảo vệ an toàn khiến phần mềm của nó, bao gồm dữ liệu nhị phân và thập lục phân, khó có thể truy cập nếu không có sự cho phép thích hợp. Tuy nhiên, kỹ thuật giải mã và kỹ thuật đảo ngược bộ vi xử lý PIC16F873 bị khóa có thể được sử dụng để mở khóa phần mềm bị khóa, cho phép trích xuất chương trình nhúng hoặc mã nguồn cho các mục đích hợp pháp.
· Selectable oscillator options
· Low power, high speed CMOS FLASH/EEPROM technology
· Fully static design
· In-Circuit Serial Programming (ICSP) via two pins
· Single 5V In-Circuit Serial Programming capability
· In-Circuit Debugging via two pins
· Processor break/write access to program memory by Break Chip PIC16F720 Firmware
· Wide operating voltage range: 2.0V to 5.5V
· High Sink/Source Current: 25 mA
· Commercial, Industrial and Extended temperature ranges
· Low-power consumption:
– < 0.6 mA typical @ 3V, 4 MHz
– 20 µA typical @ 3V, 32 kHz
– < 1 µA typical standby current
Peripheral Features:
· Timer0: 8-bit timer/counter with 8-bit prescaler
· Timer1: 16-bit timer/counter with prescaler, can be incremented during SLEEP via external crystal/clock
· Timer2: 8-bit timer/counter with 8-bit period register, prescaler and postscaler
· Two Capture, Compare, PWM modules
– Capture is 16-bit, max. resolution is 12.5 ns
– Compare is 16-bit, max. resolution is 200 ns
– PWM max. resolution is 10-bit
· 10-bit multi-channel Analog-to-Digital converter can provide a critical part for Microcontroller Unlock
· Synchronous Serial Port (SSP) with SPI (Master mode) and I2C (Master/Slave)
· Universal Synchronous Asynchronous Receiver Transmitter (USART/SCI) with 9-bit address detection
· Parallel Slave Port (PSP) 8-bits wide, with external RD, WR and CS controls (40/44-pin only)
· Brown-out detection circuitry for Brown-out Reset (BOR)
 Break MCU PIC16F527 Heximal
Break MCU PIC16F527 Heximal
Breaking MCU PIC16F527 heximal involves advanced reverse engineering techniques to decode and decrypt the encrypted firmware and data stored in its secured flash memory and EEPROM memory. This microcontroller (MCU) is a critical component in many systems, with its locked and protective design intended to prevent unauthorized access to its binary and heximal source code. However, in situations where system restoration or data recovery is essential, methods to crack and attack its security layers can be employed responsibly.
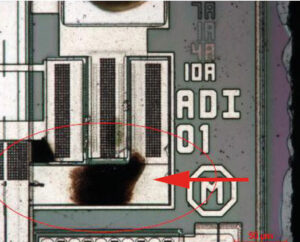
La décryption du microcontrôleur PIC16F527 hexadécimal implique des techniques avancées d’ingénierie inverse pour décoder et décrypter le micrologiciel et les données cryptés stockés dans la mémoire flash sécurisée et la mémoire EEPROM du microprocesseur PIC16F527. Ce microcontrôleur PIC16F527 (MCU) est un composant essentiel dans de nombreux systèmes, avec sa conception verrouillée et protectrice destinée à empêcher tout accès non autorisé à son code source binaire et hexadécimal. Cependant, dans les situations où la restauration du système ou la récupération des données est essentielle, des méthodes pour décrypter et attaquer ses couches de sécurité peuvent être utilisées de manière responsable.
The process begins by analyzing the MCU’s architecture to identify security protocols and vulnerabilities. Tools are then used to decrypt the protective firmware and extract the program, binary files, and source code stored within the flash memory and EEPROM memory. Such an approach enables engineers to restore or recreate essential functionalities for systems that rely on this specific microprocessor.
Breaking the locked PIC16F527 heximal data may also be necessary for replicating older or discontinued microcomputers. By restoring the firmware and software, it is possible to recreate or clone the original device, ensuring continuity in applications that use hard-to-find components.
While breaking or decoding an MCU like the PIC16F527 has practical applications, it is crucial to perform these tasks ethically and legally, respecting intellectual property and adhering to applicable regulations.
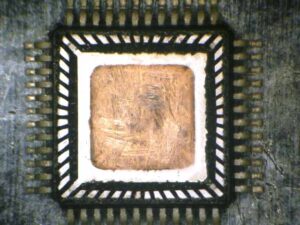
MCU PIC16F527 हेक्सिमल को तोड़ने के लिए माइक्रोप्रोसेसर PIC16F527 सुरक्षित फ्लैश मेमोरी और EEPROM मेमोरी में संग्रहीत एन्क्रिप्टेड फ़र्मवेयर और डेटा को डिकोड और डिक्रिप्ट करने के लिए उन्नत रिवर्स इंजीनियरिंग तकनीकों की आवश्यकता होती है। यह PIC16F527 माइक्रोकंट्रोलर (MCU) कई प्रणालियों में एक महत्वपूर्ण घटक है, जिसका लॉक और सुरक्षात्मक डिज़ाइन इसके बाइनरी और हेक्सिमल स्रोत कोड तक अनधिकृत पहुँच को रोकने के लिए है। हालाँकि, ऐसी स्थितियों में जहाँ सिस्टम बहाली या डेटा रिकवरी आवश्यक है, इसकी सुरक्षा परतों को तोड़ने और उन पर हमला करने के तरीकों को जिम्मेदारी से नियोजित किया जा सकता है।
The PIC16F526 device from Micromcu Technology is low-cost, high-performance, 8-bit, fully-static, Flash-based CMOS microcontrollers. It employs a RISC architecture with only 33 single-word/single-cycle instructions. All instructions are single cycle (200 ms) except for program branches, which take two cycles.
The PIC16F526 device delivers performance an order of magnitude higher than their competitors in the same price category. The 12-bit wide instructions are highly symmetrical, resulting in a typical 2:1 code compression over other 8-bit microcontrollers in its class only after the completion of Microcontroller Unlocking.
The easy-to-use and easy to remember instruction set reduces development time significantly. The PIC16F526 product is equipped with special features that reduce system cost and power requirements which has the similar process of Break IC PIC16C771 Firmware. The Power-on Reset (POR) and Device Reset Timer (DRT) eliminate the need for external Reset circuitry.
There are four oscillator configurations to choose from, including INTRC Internal Oscillator mode and the power-saving LP (Low-Power) Oscillator mode. Power-Saving Sleep mode, Watchdog Timer and code protection features improve system cost, power and reliability.
The PIC16F526 device is available in the cost-effective Flash programmable version, which is suitable for production in any volume. The customer can take full advantage of Micromcu’s price leadership in Flash programmable microcontrollers, while benefiting from the Flash programmable flexibility.
The PIC16F526 product is supported by a full-featured macro assembler, a software simulator, an in-circuit emulator, a ‘C’ compiler, a low-cost development programmer and a full featured programmer. All the tools are supported on IBM® PC and compatible machines to facilitate the process of Read Chip PIC16C770 Eeprom.
The PIC16F526 device fits in applications ranging from personal care appliances and security systems to low-power remote transmitters/receivers. The Flash technology makes customizing application programs (transmitter codes, appliance settings, receiver frequencies, etc.) extremely fast and convenient.
The small footprint packages, for through hole or surface mounting, make these microcontrollers perfect for applications with space limitations in order to Reverse Engineering Microcontroller PIC16C717 Program. Low cost, low power, high performance, ease of use and I/O flexibility make the PIC16F526 device very versatile even in areas where no microcontroller use has been considered before (e.g., timer functions, logic and PLDs in larger systems and coprocessor applications).
Взлом MCU PIC16F527 heximal включает в себя передовые методы обратного проектирования для декодирования и расшифровки зашифрованной прошивки и данных, хранящихся в защищенной флэш-памяти и памяти EEPROM микропроцессора PIC16F527. Этот микроконтроллер PIC16F527 (MCU) является критически важным компонентом во многих системах, его заблокированная и защищенная конструкция предназначена для предотвращения несанкционированного доступа к его двоичному и шестнадцатеричному исходному коду. Однако в ситуациях, когда восстановление системы или данных имеет важное значение, методы взлома и атаки на его уровни безопасности могут быть использованы ответственно.
 Reverse Engineering Microcontroller PIC16F526 Binary
Reverse Engineering Microcontroller PIC16F526 Binary
Reverse engineering the binary of a microcontroller, such as the PIC16F526, is a process used to break down or crack the firmware and software embedded within the device. This technique is often applied in a variety of fields, from security analysis to legacy system restoration. In this article, we will explore how reverse engineering works on the PIC16F526 microcontroller and the key steps involved in recovering protected or encrypted software.
What is Reverse Engineering a PIC16F526?
Reverse engineering a microcontroller like the PIC16F526 involves extracting and decoding the firmware stored in the device’s flash memory or EEPROM memory. The main goal is to recover or restore the source code that controls the microcontroller’s behavior. Often, this binary is encrypted or locked to prevent unauthorized access, making it challenging to directly access the program or heximal data.
Breaking the Protection
One of the key challenges when reverse engineering the PIC16F526 binary is dealing with protected firmware. Manufacturers often encrypt the software or firmware to prevent attackers from gaining access to proprietary code or system secrets. To decrypt the firmware, attackers might use various techniques, such as attacking the microcontroller’s security features, exploiting hardware vulnerabilities, or using software-based tools that can bypass security measures.

Обратное проектирование двоичного кода микроконтроллера, такого как PIC16F526, представляет собой процесс, используемый для взлома встроенного в устройство программного обеспечения и прошивки. Этот метод часто применяется в различных областях: от анализа безопасности до восстановления устаревших систем. В этой статье мы рассмотрим, как работает обратное проектирование на микроконтроллере PIC16F526, а также основные этапы восстановления защищенного или зашифрованного программного обеспечения.
Extracting the Binary
Once the protection is bypassed, the next step is to extract the binary code stored in the flash memory. Specialized tools can read the heximal data from the microcontroller’s memory and output it in a usable format. At this point, the binary may need to be decoded to understand its structure, as it could include encrypted or obfuscated data. Software such as disassemblers or decompilers may be used to decode the binary into an intermediate assembly code or even reconstruct the source code in higher-level languages.
Recovering and Modifying the Program
In cases where the goal is to restore or update the program, engineers may modify the source code after reverse engineering the microcontroller. This is common in situations where legacy systems need upgrading or customization, and the original source code is no longer available. Once modifications are made, the new firmware can be reflashed back into the microcontroller, restoring the updated functionality.
مهندسی معکوس باینری یک میکروکنترلر، مانند PIC16F526، فرآیندی است که برای خراب کردن یا شکستن سفتافزار و نرمافزار تعبیهشده در دستگاه استفاده میشود. این تکنیک اغلب در زمینه های مختلفی از تجزیه و تحلیل امنیتی گرفته تا بازیابی سیستم قدیمی استفاده می شود. در این مقاله، نحوه عملکرد مهندسی معکوس بر روی میکروکنترلر PIC16F526 و مراحل کلیدی مربوط به بازیابی نرم افزارهای محافظت شده یا رمزگذاری شده را بررسی خواهیم کرد.
Applications of Reverse Engineering PIC16F526
Reverse engineering the PIC16F526 binary can serve multiple purposes. It’s often used to analyze system vulnerabilities, recover lost or inaccessible firmware, and enhance system performance. In some cases, this process is also crucial in understanding how a device works, for example, in cracking a proprietary algorithm or unlocking hidden features.
Conclusion
Reverse engineering the binary of a microcontroller like the PIC16F526 is a powerful tool for developers, security analysts, and engineers. By using techniques to break protections, decrypt encrypted data, and recover the original source code, the process enables greater flexibility in working with hardware. However, the ethical and legal considerations surrounding reverse engineering should always be taken into account, as unauthorized cracking or modifying of software can have legal ramifications.
We can Reverse engineering Microcontroller PIC16F526 Binary, please view the Microcontroller PIC16F526 features for your reference:
High-Performance RISC CPU:
· Only 33 Single-Word Instructions
· All Single-Cycle Instructions except for Program Branches which are Two-Cycle
· Two-Level Deep Hardware Stack
· Direct, Indirect and Relative Addressing modes for Data and Instructions
· Operating Speed:
– DC – 20 MHz crystal oscillator
– DC – 200 ns instruction cycle
· On-chip Flash Program Memory:
– 1024 x 12
· General Purpose Registers (SRAM):
– 67 x 8
· Flash Data Memory:
– 64 x 8
Special Microcontroller Features:
· 8 MHz Precision Internal Oscillator when Break IC PIC16F610 Binary
– Factory calibrated to ±1%
· In-Circuit Serial Programming™ (ICSP™)
· In-Circuit Debugging (ICD) Support
· Power-On Reset (POR)
· Device Reset Timer (DRT)
· Watchdog Timer (WDT) with Dedicated On-Chip RC Oscillator for Reliable Operation
· Programmable Code Protection
· Multiplexed MCLR Input Pin
· Internal Weak Pull-ups on I/O Pins
· Power-Saving Sleep mode
· Wake-Up from Sleep on Pin Change
· Selectable Oscillator Options:
– INTRC: 4 MHz or 8 MHz precision Internal RC oscillator
– EXTRC: External low-cost RC oscillator
– XT: Standard crystal/resonator
– HS: High-speed crystal/resonator
– LP: Power-saving, low-frequency crystal
– EC: High-speed external clock input
Reverse Engineering Microcontroller PIC16F526 Binary
Low-Power Features/CMOS Technology:
· Standby current:
– 100 nA @ 2.0V, typical
· Operating current:
– 11 mA @ 32 kHz, 2.0V, typical
– 175 mA @ 4 MHz, 2.0V, typical
· Watchdog Timer current:
– 1 mA @ 2.0V, typical
– 7 mA @ 5.0V, typical
· High Endurance Program and Flash Data Memory cells:
– 100,000 write Program Memory endurance to Recover MCU 12F508 Code
– 1,000,000 write Flash Data Memory endurance
– Program and Flash Data retention: >40 years
· Fully Static Design
· Wide Operating Voltage Range: 2.0V to 5.5V:
– Wide temperature range
– Industrial: -40°C to +85°C
– Extended: -40°C to +125°C
Peripheral Features:
· 12 I/O Pins:
– 11 I/O pins with individual direction control
– 1 input-only pin
– High current sink/source for direct LED drive
– Wake-up on change
– Weak pull-ups
· 8-bit Real-time Clock/Counter (TMR0) with 8-bit Programmable Prescaler

การวิศวกรรมย้อนกลับไบนารีของไมโครคอนโทรลเลอร์ เช่น PIC16F526 เป็นกระบวนการที่ใช้ในการทำลายหรือแคร็กเฟิร์มแวร์และซอฟต์แวร์ที่ฝังอยู่ในอุปกรณ์ เทคนิคนี้มักใช้ในหลากหลายสาขา ตั้งแต่การวิเคราะห์ความปลอดภัยไปจนถึงการกู้คืนระบบเก่า ในบทความนี้ เราจะสำรวจวิธีการทำงานของวิศวกรรมย้อนกลับบนไมโครคอนโทรลเลอร์ PIC16F526 และขั้นตอนสำคัญที่เกี่ยวข้องกับการกู้คืนซอฟต์แวร์ที่ได้รับการป้องกันหรือเข้ารหัส
· Two Analog Comparators:
– Comparator inputs and output accessible externally
– One comparator with 0.6V fixed on-chip absolute voltage reference (VREF) by Unlock Microcontroller
– One comparator with programmable on-chip voltage reference (VREF)
· Analog-to-Digital (A/D) Converter:
– 8-bit resolution
– 3-channel external programmable inputs
– 1-channel internal input to internal absolute 0.6 voltage reference
 Recover Microcontroller PIC16C641 Eeprom
Recover Microcontroller PIC16C641 Eeprom
In the world of embedded systems, microcontrollers like the PIC16C641 often store critical data in their EEPROM or flash memory, protected by secured or encrypted mechanisms. However, there are scenarios where recovering this data becomes essential, such as firmware extraction, reverse engineering, or replicating legacy systems. This is where professional MCU crack services come into play.

Les microcontrôleurs comme le PIC16C641 stockent souvent des données critiques dans leur EEPROM ou leur mémoire flash, protégées par des mécanismes sécurisés ou cryptés. Cependant, il existe des scénarios où la récupération de ces données devient essentielle, comme l’extraction de micrologiciels, la rétro-ingénierie ou la réplication de systèmes hérités. C’est là que les services professionnels de crackage de MCU entrent en jeu.
Using advanced techniques, experts can crack, unlock, or bypass the protected memory of microcontrollers like the PIC16C641. Whether the goal is to decrypt firmware, decode source code, or dump binary files, these services employ methods such as reverse engineering, memory attacks, or even hardware-based exploits to break through secured layers. By extracting data from EEPROM or flash memory, they can recover valuable program files, archives, or other critical information.

고급 기술을 사용하여 전문가는 PIC16C641과 같은 마이크로컨트롤러의 보호된 메모리를 크랙, 잠금 해제 또는 우회할 수 있습니다. 펌웨어를 해독하거나, 소스 코드를 디코딩하거나, 바이너리 파일을 덤프하는 것이 목표이든, 이러한 서비스는 리버스 엔지니어링, 메모리 공격 또는 하드웨어 기반 익스플로잇과 같은 방법을 사용하여 보안 계층을 돌파합니다. EEPROM 또는 플래시 메모리에서 데이터를 추출하여 귀중한 프로그램 파일, 아카이브 또는 기타 중요한 정보를 복구할 수 있습니다.
For those looking to replicate or clone a microcontroller, these services can also extract and replicate the entire memory content, ensuring compatibility with new or replacement chips. While ethical considerations are paramount, such capabilities are invaluable for debugging, legacy system restoration, or forensic analysis.
In summary, MCU crack services provide the tools and expertise to recover, decode, and replicate data from secured microcontrollers, unlocking the potential of even the most protected chips.
We can Recover Microcontroller PIC16C641 Eeprom, please view the Microcontroller PIC16C641 features for your reference:
High Performance RISC CPU:
· Only 35 instructions to learn
· All single-cycle instructions (200 ns), except for program branches which are two-cycle when Recover Microcontroller
· Operating speed:
– DC – 20 MHz clock input
– DC – 200 ns instruction cycle
· Interrupt capability
· 8-level deep hardware stack
· Direct, Indirect and Relative addressing modes can help to Break IC PIC12F609 Heximal
Peripheral Features:
· Up to 33 I/O pins with individual direction control
· High current sink/source for direct LED drive
· Analog comparator module with:
– Two analog comparators
– Programmable on-chip voltage reference (VREF) module
– Programmable input multiplexing from device inputs and internal voltage reference
– Comparator outputs can be output signals
· Timer0: 8-bit timer/counter with 8-bit programmable prescaler
Special Microcontroller Features:
· Power-on Reset (POR)

माइक्रोकंट्रोलर की नकल या क्लोनिंग करने वालों के लिए, ये सेवाएँ संपूर्ण मेमोरी सामग्री को निकाल और दोहरा सकती हैं, जिससे नए या प्रतिस्थापन चिप्स के साथ संगतता सुनिश्चित होती है। जबकि नैतिक विचार सर्वोपरि हैं, ऐसी क्षमताएँ डिबगिंग, विरासत प्रणाली बहाली या फोरेंसिक विश्लेषण के लिए अमूल्य हैं।
संक्षेप में, MCU क्रैक सेवाएँ सुरक्षित माइक्रोकंट्रोलर से डेटा को पुनर्प्राप्त करने, डिकोड करने और दोहराने के लिए उपकरण और विशेषज्ञता प्रदान करती हैं, यहाँ तक कि सबसे सुरक्षित चिप्स की क्षमता को भी अनलॉक करती हैं।
· Power-up Timer (PWRT) and Oscillator Start-up Timer (OST)
· Brown-out Reset
· Watchdog Timer (WDT) with its own on-chip RC oscillator for reliable operation
· Programmable code protection will tamper the resistance of Break IC PIC12F615 Software
· Power saving SLEEP mode
· Serial in-circuit programming (via two pins)
· Four user programmable ID locations
· Program Memory Parity Error checking circuitry with Parity Error Reset (PER) to Crack MCU
· CMOS Technology:
· Low-power, high-speed CMOS EPROM technology
· Fully static design
· Wide operating voltage range: 3.0V to 6.0V
· Commercial, Industrial and Automotive temperature ranges
· Low power consumption
– < 2.0 mA @ 5.0V, 4.0 MHz
– 15 µA typical @ 3.0V, 32 kHz
– < 1.0 µA typical standby current @ 3.0V
 Recover MCU PIC12CR509A Flash
Recover MCU PIC12CR509A Flash
the PIC12CR509A microcontroller is widely used for its efficiency and compact design. However, many of these MCUs come with secured or locked firmware, making it challenging to access their flash memory or EEPROM data. This is where professional MCU crack services come into play, offering solutions to recover, decrypt, and extract critical information from protected chips.

Le microcontrôleur PIC12CR509A est largement utilisé pour son efficacité et sa conception compacte. Cependant, bon nombre de ces microcontrôleurs sont livrés avec un micrologiciel sécurisé ou verrouillé, ce qui rend difficile l’accès à leur mémoire flash ou à leurs données EEPROM. C’est là qu’interviennent les services professionnels de crackage de microcontrôleurs, proposant des solutions pour récupérer, décrypter et extraire des informations critiques à partir de puces protégées.
Using advanced techniques such as reverse engineering and binary analysis, experts can unlock the encrypted firmware of the PIC12CR509A. Whether the goal is to decode the source code, dump the flash memory, or replicate the program for further development, these services provide a pathway to bypass the secured barriers. By employing non-invasive methods, the original chip remains intact while the protected data is extracted.
역엔지니어링 및 바이너리 분석과 같은 고급 기술을 사용하여 전문가는 PIC12CR509A의 암호화된 펌웨어를 잠금 해제할 수 있습니다. 소스 코드를 디코딩하거나, 플래시 메모리를 덤프하거나, 추가 개발을 위해 프로그램을 복제하는 것이 목표이든, 이러한 서비스는 보안 장벽을 우회하는 경로를 제공합니다. 비침습적 방법을 사용함으로써 보호된 데이터가 추출되는 동안 원래 칩은 그대로 유지됩니다.
For those looking to hack or break into a locked MCU, specialized tools and software are used to attack the encryption algorithms. This process often involves decoding the binary files, analyzing the memory structure, and reconstructing the original firmware archive. Such services are invaluable for recovering lost data, cloning microcontrollers, or understanding the functionality of a protected microprocessor.

लॉक किए गए MCU को हैक करने या उसमें सेंध लगाने की चाहत रखने वालों के लिए, एन्क्रिप्शन एल्गोरिदम पर हमला करने के लिए विशेष उपकरण और सॉफ़्टवेयर का उपयोग किया जाता है। इस प्रक्रिया में अक्सर बाइनरी फ़ाइलों को डिकोड करना, मेमोरी संरचना का विश्लेषण करना और मूल फ़र्मवेयर संग्रह का पुनर्निर्माण करना शामिल होता है। ऐसी सेवाएँ खोए हुए डेटा को पुनर्प्राप्त करने, माइक्रोकंट्रोलर को क्लोन करने या संरक्षित माइक्रोप्रोसेसर की कार्यक्षमता को समझने के लिए अमूल्य हैं।
However, it’s important to note that MCU crack services should only be used for legitimate purposes, such as recovering data from a damaged chip or reverse engineering for compatibility improvements. With the right expertise, even the most secured PIC12CR509A flash memory can be unlocked, providing access to its hidden treasures.
We can Recover MCU PIC12CR509A Flash, please view the MCU PIC12CR509A features for your reference:
The PICCR509A each have 16 bytes of EEPROM data memory. The EEPROM memory has an endurance of 1,000,000 erase/write cycles and a data retention of greater than 40 years. The EEPROM data memory supports a bi-directional 2-wire bus and data transmission protocol.
These two-wires are serial data (SDA) and serial clock (SCL), that are mapped to bit6 and bit7, respectively, of the GPIO register (SFR 06h). Unlike the GP0-GP5 that are connected to the I/O pins, SDA and SCL are only connected to the internal EEPROM peripheral in order to Break IC PIC12F639 Heximal. For most applications, all that is required is calls to the following functions:
The code for these functions is available on our website www.microchip.com. The code will be accessed by either including the source code FL51XINC.ASM or by linking FLASH5IX.ASM. It is very important to check the return codes when using these calls, and retry the operation if unsuccessful.
Unsuccessful return codes occur when the EE data memory is busy with the previous write, which can take up to 4 mS. SDA is a bi-directional pin used to transfer addresses and data into and data out of the device before Recover MCU.
For normal data transfer SDA is allowed to change only during SCL low. Changes during SCL high are reserved for indicating the START and STOP conditions. The EEPROM interface is a 2-wire bus protocol consisting of data (SDA) and a clock (SCL) when Recover MCU PIC12CR509A Flash.
Although these lines are mapped into the GPIO register, they are not accessible as external pins; only to the i internal EEPROM peripheral. SDA and SCL operation is also slightly different than GPO-GP5 as listed below. Namely, to avoid code overhead in modifying the TRIS register to complete the process of Break IC PIC12F615 Software, both SDA and SCL are always outputs.
To read data from the EEPROM peripheral requires outputting a ‘1’ on SDA placing it in high-Z state, where only the internal 100K pull-up is active on the SDA line. SDA:
Built-in 100K (typical) pull-up to VDD Open-drain (pull-down only)
Always an output
Outputs a ‘1’ on reset
SCL:
Full CMOS output
Always an output
Outputs a ‘1’ on reset
The following example requires:
· Code Space: 77 words
· RAM Space: 5 bytes (4 are overlayable)
· Stack Levels:1 (The call to the function itself. The functions do not call any lower level functions.)
· Timing:
– WRITE_BYTE takes 328 cycles
– READ_CURRENT takes 212 cycles
– READ_RANDOM takes 416 cycles.
· IO Pins: 0 (No external IO pins are used)
This code must reside in the lower half of a page. The code achieves it’s small size without additional calls through the use of a sequencing table to Crack MCU. The table is a list of procedures that must be called in order. The table uses an ADDWF PCL,F instruction, effectively a computed goto, to sequence to the next procedure. However the ADDWF PCL,F instruction yields an 8 bit address, forcing the code to reside in the first 256 addresses of a page.
 Break IC PIC12CE519 Flash
Break IC PIC12CE519 Flash
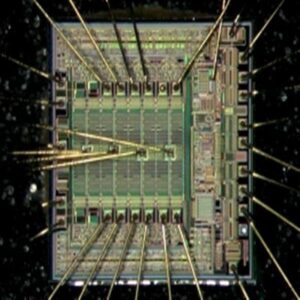
The IC PIC12CE519 Flash memory, commonly used in embedded systems, plays a crucial role in storing firmware and other system data. However, for various reasons—such as debugging, security audits, or customization—accessing and modifying the data within this memory can be a challenge. At [Your Company Name], we offer specialized services to break the IC PIC12CE519 Flash, allowing you to unlock and modify the firmware to suit your needs.

PIC12CE519 Memoria flash, folosită în mod obișnuit în sistemele încorporate, joacă un rol crucial în stocarea firmware-ului și a altor date de sistem. Cu toate acestea, din diverse motive, cum ar fi depanare, audituri de securitate sau personalizare, accesarea și modificarea datelor din această memorie poate fi o provocare. La CECL, oferim servicii specializate pentru a sparge IC PIC12CE519 Flash, permițându-vă să deblocați și să modificați firmware-ul pentru a se potrivi nevoilor dumneavoastră.
Our expert team uses advanced techniques to extract, disassemble, and analyze the data stored in the PIC12CE519 Flash. By employing specialized tools and custom scripts, we can access the firmware’s internal structure, providing you with a deeper understanding of its operation. Whether you need to identify vulnerabilities, reverse-engineer proprietary code, or recover lost data, we have the experience and tools to get the job done.
Our services are tailored to meet the unique needs of each client, ensuring precision, efficiency, and confidentiality. With our help, you’ll be able to unlock the full potential of your embedded systems and make informed decisions about security, optimization, or customization.
Unser Expertenteam verwendet fortschrittliche Techniken, um die im PIC12CE519-Flash gespeicherten Daten zu extrahieren, zu zerlegen und zu analysieren. Durch den Einsatz spezieller Tools und benutzerdefinierter Skripte können wir auf die interne Struktur der Firmware zugreifen und Ihnen so ein tieferes Verständnis ihrer Funktionsweise vermitteln. Ob Sie Schwachstellen identifizieren, proprietären Code zurückentwickeln oder verlorene Daten wiederherstellen müssen, wir haben die Erfahrung und die Tools, um die Arbeit zu erledigen.
Contact us today to learn more about how we can help you break the IC PIC12CE519 Flash and gain control of your embedded systems.
As with any other register, the I/O register can be written and read under program control when Break IC PIC12CE519 Flash. However, read instructions (e.g., MOVF GPIO,W) always read the I/O pins independent of the pin’s input/output modes. On RESET, all I/O ports are defined as input (inputs are at hi-impedance) since the I/O control registers are all set. See Section 7.0 for SCL and SDA description for PIC12CE5XX.

Serviciile noastre sunt adaptate pentru a răspunde nevoilor unice ale fiecărui client, asigurând precizie, eficiență și confidențialitate. Cu ajutorul nostru, veți putea debloca întregul potențial al sistemelor dvs. încorporate și veți putea lua decizii informate cu privire la securitate, optimizare sau personalizare.
GPIO is an 8-bit I/O register. Only the low order 6 bits are used (GP5:GP0). Bits 7 and 6 are unimplemented and read as ’0′s. Please note that GP3 is an input only pin. The configuration word can set several I/O’s to alternate functions. When acting as alternate functions the pins will read as ‘0’ during port read. Pins GP0, GP1, and GP3 can be configured with weak pull-ups and also with wake-up on change.
The wake-up on change and weak pull-up functions are not pin selectable. If pin 4 is configured as MCLR, weak pull-up is always on and wake-up on change for this pin is not enabled after Break Chip PIC12CE518 Binary.
The output driver control register is loaded with the contents of the W register by executing the TRIS instruction. A ’1′ from a TRIS register bit puts the corresponding output driver in a hi-impedance mode.
A ’0′ puts the contents of the output data latch on the selected pins, enabling the output buffer. The exceptions are GP3 which is input only and GP2 which may be controlled by Copy Chip PIC16F87 Code, The equivalent circuit for an I/O port pin is shown in below Figure.
All port pins, except GP3 which is input only, may be used for both input and output operations.
For input operations these ports are non-latching. Any input must be present until read by an input instruction (e.g., MOVF GPIO,W). The outputs are latched and remain unchanged until the output latch is rewritten. To use a port pin as output, the corresponding direction control bit in TRIS must be cleared (= 0). For use as an input, the corresponding TRIS bit must be set.
Any I/O pin (except GP3) can be programmed individually as input or output. Some instructions operate internally as read followed by write operations. The BCF and BSF instructions, for example, read the entire port into the CPU, execute the bit operation and re-write the result in order to Recover Microcontroller PIC16F71 Binary. Caution must be used when these instructions are applied to a port where one or more pins are used as input/outputs.
For example, a BSF operation on bit5 of GPIO will cause all eight bits of GPIO to be read into the CPU, bit5 to be set and the GPIO value to be written to the output latches. If another bit of GPIO is used as a bi- directional I/O pin (say bit0) and it is defined as an input at this time, the input signal present on the pin itself would be read into the CPU and rewritten to the data latch of this particular pin, overwriting the previous content.
As long as the pin stays in the input mode, no problem occurs. However, if bit0 is switched into output mode later on, the content of the data latch to facilitate the process of Crack MCU. The actual write to an I/O port happens at the end of may now be unknown.
 Recover Chip PIC12CE518 Binary
Recover Chip PIC12CE518 Binary
The PIC12CE518 microcontroller, widely used in embedded systems, stores critical firmware in its internal memory. Sometimes, due to corruption, loss of access, or the need for system modifications, there may be a need to recover or restore the chip’s binary. At [Your Company Name], we specialize in recovering the PIC12CE518 binary using advanced techniques to decode, decrypt, and reverse engineer the firmware, providing you with full access to your system’s data.
![Der Mikrocontroller PIC12CE518, der in eingebetteten Systemen weit verbreitet ist, speichert kritische Firmware in seinem internen Speicher. Manchmal kann es aufgrund von Beschädigungen, Zugriffsverlusten oder der Notwendigkeit von Systemänderungen erforderlich sein, die Binärdatei des Chips wiederherzustellen oder wiederherzustellen. Bei [Name Ihres Unternehmens] sind wir auf die Wiederherstellung der Binärdatei des PIC12CE518 spezialisiert und verwenden fortschrittliche Techniken zum Dekodieren, Entschlüsseln und Reverse Engineering der Firmware, sodass Sie vollen Zugriff auf die Daten Ihres Systems erhalten.](https://www.ic-crack.com/wp-content/uploads/2015/04/dscf4968_cropped-296x300.jpg)
Der Mikrocontroller PIC12CE518, der in eingebetteten Systemen weit verbreitet ist, speichert kritische Firmware in seinem internen Speicher. Manchmal kann es aufgrund von Beschädigungen, Zugriffsverlusten oder der Notwendigkeit von Systemänderungen erforderlich sein, die Binärdatei des Chips wiederherzustellen oder wiederherzustellen. Bei [Name Ihres Unternehmens] sind wir auf die Wiederherstellung der Binärdatei des PIC12CE518 spezialisiert und verwenden fortschrittliche Techniken zum Dekodieren, Entschlüsseln und Reverse Engineering der Firmware, sodass Sie vollen Zugriff auf die Daten Ihres Systems erhalten.
Our team of experts uses a series of sophisticated tools and methods to crack the chip’s security and break any obfuscation techniques protecting the firmware. We can reverse engineer the binary code from the PIC12CE518, even if the data has been intentionally encrypted or encoded. This process enables us to uncover valuable insights into how the system functions, detect potential vulnerabilities, and assist with debugging or customizing the firmware for your specific needs.

Нашият екип от експерти използва серия от усъвършенствани инструменти и методи, за да пробие сигурността на чипа и да разбие всички техники за обфускация, защитаващи фърмуера. Можем да проектираме обратно двоичния код от PIC12CE518, дори ако данните са умишлено криптирани или кодирани. Този процес ни позволява да разкрием ценна информация за това как функционира системата, да открием потенциални уязвимости и да помогнем при отстраняване на грешки или персонализиране на фърмуера за вашите специфични нужди.
Whether you need to attack a particular piece of firmware to extract sensitive information, hack into a locked system, or restore lost data, our services are tailored to handle complex challenges. We employ state-of-the-art methods to decrypt any protection schemes, ensuring a secure, efficient recovery process.
With our knowledge in embedded systems and microcontroller architectures, we can assist with various tasks, from decoding encrypted firmware to extracting the binary for modifications or audits. We understand the importance of confidentiality, security, and precision in these delicate processes.

Cho dù bạn cần tấn công một phần chương trình cơ sở cụ thể để trích xuất thông tin nhạy cảm, hack vào hệ thống bị khóa hoặc khôi phục dữ liệu đã mất, các dịch vụ của chúng tôi đều được thiết kế riêng để xử lý các thách thức phức tạp. Chúng tôi sử dụng các phương pháp tiên tiến nhất để giải mã mọi chương trình bảo vệ, đảm bảo quy trình khôi phục an toàn và hiệu quả.
Với kiến thức về hệ thống nhúng và kiến trúc vi điều khiển, chúng tôi có thể hỗ trợ nhiều nhiệm vụ khác nhau, từ giải mã chương trình cơ sở được mã hóa đến trích xuất nhị phân để sửa đổi hoặc kiểm tra. Chúng tôi hiểu tầm quan trọng của tính bảo mật, an ninh và độ chính xác trong các quy trình tinh vi này.
As a program instruction is executed, the Program Counter (PC) will contain the address of the next program instruction to be executed by Recover Chip PIC12CE518 Binary. The PC value is increased by one every instruction cycle, unless an instruction changes the PC. For a GOTO instruction, bits 8:0 of the PC are provided by the GOTO instruction word. The PC Latch (PCL) is mapped to PC<7:0>. Bit 5 of the STATUS register provides page information to bit 9 of the PC (Figure 4- 8).
For a CALL instruction, or any instruction where the PCL is the destination, bits 7:0 of the PC again are provided by the instruction word. However, PC<8> does not come from the instruction word, but is always cleared.
Instructions where the PCL is the destination, or Modify PCL instructions, include MOVWF PC, ADDWF PC, and BSF PC,5.
The Program Counter is set upon a RESET, which means that the PC addresses the last location in the last page i.e., the oscillator calibration instruction. After executing MOVLW XX, the PC will roll over to location 00h, and begin executing user code.
The STATUS register page preselect bits are cleared upon a RESET, which means that page 0 is pre-selected.
Therefore, upon a RESET, a GOTO instruction will automatically cause the program to jump to page 0 until the value of the page bits is altered. PIC12C5XX devices have a 12-bit wide L.I.F.O. hardware push/pop stack to Attack IC PIC16C74B Binary.
A CALL instruction will push the current value of stack 1 into stack 2 and then push the current program counter value, incremented by one, into stack level 1. If more than two sequential CALL’s are executed, only the most recent two return addresses are stored when Recover Chip PIC12CE518 Binary.
ARETLW instruction will pop the contents of stack level 1 into the program counter and then copy stack level contents into level 1. If more than two sequential RETLW’s are executed, the stack will be filled with the address previously stored in level 2. Note that the W register will be loaded with the literal value specified in the instruction. This is particularly useful for the implementation of data look-up tables within the program memory when MCU Cracking.
Upon any reset, the contents of the stack remain unchanged, however the program counter (PCL) will also be reset.
 Reverse Engineering Microcontroller PIC12C509A Binary
Reverse Engineering Microcontroller PIC12C509A Binary
The PIC12C509A is commonly used in embedded systems, from consumer electronics to automotive applications. However, many of these systems are designed with protective measures to prevent unauthorized access. Our service allows you to break through these security layers and retrieve the underlying source code from the binary or heximal firmware files.
Whether your goal is to clone, duplicate, or copy the firmware, our team employs advanced reverse engineering techniques to attack the secured binary data. This process often involves disassembling the firmware, analyzing the program logic, and extracting meaningful data that can be re-engineered for further use. We can help unlock the hidden secrets within the firmware to make necessary adjustments, fix bugs, enhance functionality, or perform security audits.

Der PIC12C509A wird häufig in eingebetteten Systemen verwendet, von der Unterhaltungselektronik bis hin zu Automobilanwendungen. Viele dieser Systeme sind jedoch mit Schutzmaßnahmen ausgestattet, um unbefugten Zugriff zu verhindern. Unser Service ermöglicht es Ihnen, diese Sicherheitsebenen zu durchbrechen und den zugrunde liegenden Quellcode aus den binären oder hexadezimalen Firmwaredateien abzurufen.
Ganz gleich, ob Ihr Ziel darin besteht, die Firmware zu klonen, zu duplizieren oder zu kopieren, unser Team verwendet fortschrittliche Reverse-Engineering-Techniken, um die gesicherten Binärdaten anzugreifen. Dieser Prozess umfasst häufig das Zerlegen der Firmware, das Analysieren der Programmlogik und das Extrahieren aussagekräftiger Daten, die für die weitere Verwendung neu entwickelt werden können. Wir können Ihnen helfen, die verborgenen Geheimnisse der Firmware zu entschlüsseln, um notwendige Anpassungen vorzunehmen, Fehler zu beheben, die Funktionalität zu verbessern oder Sicherheitsprüfungen durchzuführen.
Our Expertise in Handling Secured Data
Our reverse engineering service for the PIC12C509A binary involves using the latest tools and methods to open locked firmware, decrypt protected data, and extract the source code. By doing so, we provide a reliable solution to ensure you can make informed decisions about your embedded system, whether it’s for customization, repair, or vulnerability testing.

Нашата услуга за обратно инженерство за двоичния PIC12C509A включва използването на най-новите инструменти и методи за отваряне на заключен фърмуер, дешифриране на защитени данни и извличане на изходния код. Правейки това, ние предоставяме надеждно решение, за да гарантираме, че можете да вземате информирани решения относно вашата вградена система, независимо дали става въпрос за персонализиране, поправка или тестване на уязвимости.
Conclusion
If you’re struggling with locked or encrypted PIC12C509A firmware, our team is here to help. We can reverse engineer your microcontroller’s binary to restore functionality, break protective layers, and give you the tools to control and modify your embedded system. Contact us today to discuss your reverse engineering needs.

Nếu bạn đang gặp khó khăn với chương trình cơ sở PIC12C509A bị khóa hoặc mã hóa, nhóm của chúng tôi ở đây để giúp bạn. Chúng tôi có thể đảo ngược kỹ thuật nhị phân của bộ vi điều khiển của bạn để khôi phục chức năng, phá vỡ các lớp bảo vệ và cung cấp cho bạn các công cụ để kiểm soát và sửa đổi hệ thống nhúng của bạn. Liên hệ với chúng tôi ngay hôm nay để thảo luận về nhu cầu kỹ thuật đảo ngược của bạn.
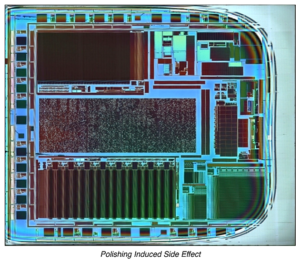
PIC12C5XX memory is organized into program memory and data memory to facilitate the process of Reverse Engineering Microcontroller PIC12C509A Binary. For devices with more than 512 bytes of program memory, a paging scheme is used.
Program memory pages are accessed using one STATUS register bit. For the PIC12C509, PIC12C509A, PICCR509A and PIC12CE519 with a data memory register file of more than 32 registers, a banking scheme is used. Data memory banks are accessed using the File Select Register (FSR) for the purpose of Recover Chip PIC16F83 Eeprom.
The PIC12C5XX devices have a 12-bit Program Counter (PC) capable of addressing a 2K x 12 program memory space. Only the first 512 x 12 (0000h-01FFh) for the PIC12C509A and 1K x 12 (0000h-03FFh) for the PIC12C509, PIC12C509A, PIC12CR509A, and PIC12CE519 are physically implemented.
Refer to Figure 4-1. Accessing a location above these boundaries will cause a wrap around within the first 512 x 12 space (PIC12C509A) or 1K x 12 space (PIC12C509A) if Reverse engineering Microcontroller. The effective reset vector is at 000h, (see Figure 4-1). Location 01FFh (PIC12C508, PIC12C508A and PIC12CE518) or location 03FFh (PIC12C509, PIC12C509A, PIC12CR509A and PIC12CE519) contains the internal clock oscillator calibration value. This value should never be overwritten when Reverse Engineering Microcontroller PIC16C717 Program.
As a program instruction is executed, the Program Counter (PC) will contain the address of the next program instruction to be executed. The PC value is increased by one every instruction cycle, unless an instruction changes the PC.
For a GOTO instruction, bits 8:0 of the PC are provided by the GOTO instruction word. The PC Latch (PCL) is mapped to PC<7:0>. Bit 5 of the STATUS register provides page information to bit 9 of the PC (Figure 4- 8).For a CALL instruction, or any instruction where the PCL is the destination, bits 7:0 of the PC again are provided by the instruction word. However, PC<8> does not come from the instruction word, but is always cleared.
Reverse Engineering Microcontroller PIC12C509A Binary
Instructions where the PCL is the destination, or Modify PCL instructions, include MOVWF PC, ADDWF PC, and BSF PC,5. The Program Counter is set upon a RESET, which means that the PC addresses the last location in the last page i.e., the oscillator calibration instruction. After executing MOVLW XX, the PC will roll over to location 00h, and begin executing user code through Break IC PIC16C711 Program.
The STATUS register page preselect bits are cleared upon a RESET, which means that page 0 is pre-selected. Therefore, upon a RESET, a GOTO instruction will automatically cause the program to jump to page 0 until the value of the page bits is altered by Crack MCU.
 Break IC PIC12C508A Flash
Break IC PIC12C508A Flash
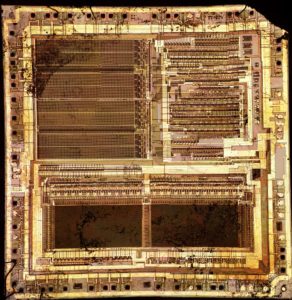
The PIC12C508A microcontroller, widely used in embedded systems, features protected Flash memory to secure firmware and prevent unauthorized access. However, in many cases—such as system recovery, reverse engineering, or software debugging—accessing this locked data becomes essential. At Circuit engineering co.,ltd, we specialize in breaking IC PIC12C508A Flash to extract, decode, and clone firmware, ensuring that our clients can regain control of their embedded systems.
![A beágyazott rendszerekben széles körben használt PIC12C508A mikrokontroller védett Flash memóriával rendelkezik a firmware védelme és az illetéktelen hozzáférés megakadályozása érdekében. Sok esetben azonban – például a rendszer-helyreállítás, a visszafejtés vagy a szoftverhibakeresés során – a zárolt adatokhoz való hozzáférés elengedhetetlen. A [Your Company Name] cégnél a PIC12C508A Flash IC feltörésére specializálódtunk a firmware kinyerése, dekódolása és klónozása érdekében, ezzel biztosítva, hogy ügyfeleink visszaszerezhessék az irányítást beágyazott rendszereik felett.](https://www.ic-crack.com/wp-content/uploads/2015/04/0-b289ae77-1600-CIRC.-INTEGRATO-PIC12C508A-04-P-DIL-8-MICROCHIP-PIC12C508-300x225.jpg)
A beágyazott rendszerekben széles körben használt PIC12C508A mikrokontroller védett Flash memóriával rendelkezik a firmware védelme és az illetéktelen hozzáférés megakadályozása érdekében. Sok esetben azonban – például a rendszer-helyreállítás, a visszafejtés vagy a szoftverhibakeresés során – a zárolt adatokhoz való hozzáférés elengedhetetlen. A [Your Company Name] cégnél a PIC12C508A Flash IC feltörésére specializálódtunk a firmware kinyerése, dekódolása és klónozása érdekében, ezzel biztosítva, hogy ügyfeleink visszaszerezhessék az irányítást beágyazott rendszereik felett.
Our Expertise in IC PIC12C508A Flash Extraction
Our team of professionals employs cutting-edge techniques to decrypt and unlock the protected memory inside the PIC12C508A. By leveraging advanced hardware and software tools, we can restore, copy, and duplicate firmware from Flash, EEPROM, and other secured memory archives.
Whether you need to reverse-engineer a locked binary, extract encrypted EEPROM data, or clone embedded programs, we provide efficient and precise solutions.
Наша команда профессионалов использует передовые методы для расшифровки и разблокировки защищенной памяти внутри PIC12C508A. Используя передовые аппаратные и программные инструменты, мы можем восстанавливать, копировать и дублировать прошивку из Flash, EEPROM и других защищенных архивов памяти.
Если вам нужно выполнить обратную разработку заблокированного двоичного файла, извлечь зашифрованные данные EEPROM или клонировать встроенные программы, мы предлагаем эффективные и точные решения.
Why Choose Our IC Flash Unlocking Service?
- Advanced Techniques: We utilize specialized equipment to crack protected firmware and decrypt embedded heximal files without damaging the microcontroller.
- Secure and Confidential: We ensure that all extracted memory archives and binary programs are handled securely.
- Comprehensive Analysis: Our experts can analyze, decode, and reconstruct source code from encrypted or obfuscated firmware.
If you need to break IC PIC12C508A Flash, recover lost firmware files, or clone locked data, contact us today. We provide reliable solutions to help you unlock embedded memory and gain full access to your secured programs.
A variety of packaging options are available which the engineer should pay attention when Break IC PIC12C508A Flash. Depending on application and production requirements, the proper device option can be selected using the information in this section. When placing orders, please use the PIC12C5XX Product Identification System at the back of this data sheet to specify the correct part number.

Se hai bisogno di rompere IC PIC12C508A Flash, recuperare file firmware persi o clonare dati bloccati, contattaci oggi stesso. Forniamo soluzioni affidabili per aiutarti a sbloccare la memoria incorporata e ottenere l’accesso completo ai tuoi programmi protetti.
Sono disponibili diverse opzioni di confezionamento a cui l’ingegnere dovrebbe prestare attenzione quando si rompe IC PIC12C508A Flash. A seconda dell’applicazione e dei requisiti di produzione, è possibile selezionare l’opzione dispositivo appropriata utilizzando le informazioni in questa sezione. Quando si effettuano ordini, utilizzare il sistema di identificazione del prodotto PIC12C5XX sul retro di questa scheda tecnica per specificare il numero di parte corretto.
The UV erasable version, offered in ceramic side brazed package, is optimal for prototype development and pilot programs.
Break IC PIC12C508A Flash
The UV erasable version can be erased and reprogrammed to any of the configuration modes.
Microchip’s PICSTART® PLUS and PRO MATE® programmers all support programming of the PIC12C5XX.
Third party programmers also are available; refer to the Microchip Third Party Guide for a list of sources. The availability of OTP devices is especially useful for customers who need the flexibility for frequent code updates or small volume applications, if not, we can see Recover Microcontroller TMS320F2812PGFA Firmware as a feasible solution for it.
The OTP devices, packaged in plastic packages permit the user to program them once. In addition to the program memory, the configuration bits must also be programmed.
Microchip offers a QTP Programming Service for factory production orders. This service is made available for users who choose not to program a medium to high quantity of units and whose code patterns have stabilized.
The devices are identical to the OTP devices but with all EPROM locations and fuse options albreaky programmed by the factory after Crack MCU. Certain code and prototype verification procedures do apply before production shipments are available. Please contact your local Microchip Technology sales office for more details.
Microchip offers a unique programming service where a few user-defined locations in each device are programmed with different serial numbers. The serial numbers may be random, pseudo-random or sequential. Serial programming allows each device to have a unique number which can serve as an entry-code, password or ID number in the process of Break MCU AT89C5131A Binary. Microchip offers masked ROM to give the customer a low cost option for high volume, mature products.