Microcontroller Content Sensitive to External Power Supply Recovery
Microcontroller Content Sensitive to External Power Supply Recovery
Microcontroller Content Sensitive to External Power Supply Recovery has long been viewed as impossible to crack MCU with battery powered embedded SRAM was chosen – Vasco Digipass 270 – two-factor authentication token [11]. Although such devices do not have very high level of security protection like devices with tamper resistant enclosure, they offer adequate level of protection against all sorts of MCU attacks. The reason for that is because the embedded SRAM is sensitive to the fluctuations of external power supply. Any interruption of the supply will cause the loss of data. In this case the signing key. Moreover, even the hardware reset of the device will make it inoperable, resulting in all keys and the user PIN being wiped off.
The device is relatively easy to disassemble as the internal electronics is only covered with plastic sheets glued to its plastic case. The main component of the device is a specialised microcontroller which is bonded directly to the PCB and encapsulated with epoxy. Removing the battery for more than a few seconds results in the device going into internal test mode and no longer operational.
The same happens if the Reset line of the microcontroller is shorted to 0. The result of the successful partial decapsulation of the microcontroller is shown in below Figure. However, because the battery was removed for that process, the microcontroller had no useful information inside.
In order to verify the idea of live decapsulation, the PCB of the fully working token was first wrapped in an insulation tape, while the potted chip was covered with aluminium tape (below Figure). Then the whole setup was wrapped into aluminium tape before creating a cut in the tape where the decapsulation was desired.
 Secure Microcontroller Memory Recovery
Secure Microcontroller Memory Recovery
As a first target to demonstrate the affordable process of Secure Microcontroller Memory Recovery, an early 2000s smartcard was chosen. It is based on the Hitachi HD6483102 chip fabricated with 0.8μm process with 2 metal layers and has embedded Mask ROM and EEPROM.

Secure Microcontroller Memory Recovery
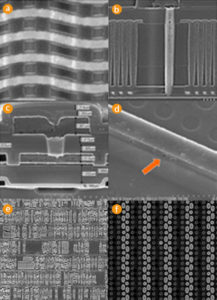
The Mask ROM is protected against optical MCU reading with doping encoding. The Von-Newmann RISC 16-bit CPU with H8/300 architecture of this chip allows access to all resources in the linear address space and has a relatively simple instruction set [10]. The interesting property of this instruction set is if the most significant bit equals to 1 then the CPU will always execute single-cycle instructions without any branches. This can be achieved with a laser cutter [2] and the result is shown in Fig. 3.
In order to microprobe the data bus only opening in the passivation layer is required (Fig. 4). This cavity will help in holding the tip of the needle in place during the microprobing process.
Once the CPU is forced into execution of simple instructions it will access the whole memory by fetching all the addresses sequentially. This way the memory contents can be extracted by placing a microprobing needle over each bit of the data bus one at a time and recording the information on a digital storage oscilloscope. After that all the acquisitions could be synchronised with the Reset signal.
 Microcontroller Breaking Directions
Microcontroller Breaking Directions
The outcome of ignorance in understanding the Microcontroller Breaking directions could be devastating to many modern devices going online or wireless as part of the Internet-of-Things (IoT) initiative. Modern semiconductors which have wireless connectivity could be cracked in many ways through software vulnerabilities and backdoors.
Sometime the research could even lead to impossible achievements. This happens when someone senior tells that certain things are not possible, but the research proves them wrong. This could result in a large outcry in the media like it was in the case of NAND mirroring attack on iPhone 5C [9]. There are some impossible challenges faced by Forensic Analysis engineers, for example, MCU data extraction from electrically damaged (Fig. 1) and mechanically damaged (Fig.2).
Although the contents of the on-chip non-volatile memory was fully preserved, conventional Failure Analysis methods are not only very expensive but would also require weeks or months of tedious work. However, it is very likely that Hardware Security would be able to come up with feasible and affordable solutions in the nearest future.
As a contribution to the wide list of already known MCU memory breaking this paper introduces two new attacks. One is about efficient microprobing of an old smartcard chip, another is about decapsulation of a microcontroller with battery-backed on-chip SRAM.
 Secured Microcontroller Hardware Security
Secured Microcontroller Hardware Security
When the existence of a backdoor in highly secure Microcontrollers was discovered in the form of secret test/debug interface capable of overriding chip security policy, it raised a lot of questions about Secured Microcontroller Hardware Security of modern ICs.
Recently demonstrated method for the direct imaging of EEPROM and Flash memory contents using easily accessible Scanning Electron Microscopes (SEM) challenges the security of embedded storage. This is because non-volatile memory was always considered as being highly secure against most invasive MCU crack due to very small electrical charge accumulated beneath very thin barrier that cannot survive de-processing. Now the obvious question is: What could be the next in ground IC breaking and disturbing attack on hardware security?
In many cases new MCU attacks were far from being something absolutely new. For example, structural analysis for impurities using chemical methods were known for decades and actively used in Failure Analysis. The fact that switching of each individual transistor contributes to the overall power consumption of the circuit was not new and was actively used by semiconductors development tools to predict power consumption and overheating. Even the photon emission was known, but was too expensive as common attack technology.
The fact that photons can interact with transistors was known since the development of transistors and was even used for communication. The ability of electron beam to detect buried charge was also known, but only with the development of more sensitive microscopes became practical to use. The main message of this paper is if the vast majority of IC code extraction are based on already known facts, there must be a way to predict such attacks and develop mitigation techniques well ahead of the active use by attackers.
 PIC18F4523 Microcontroller Embedded Memory Breaking
PIC18F4523 Microcontroller Embedded Memory Breaking
Many PIC18 control instructions do not need any argument at all by Break IC STM32F101C4T6TR Binary; they either perform an operation that globally affects the device or they operate implicitly on one register after PIC18F4523 Microcontroller Embedded Memory Breaking. This addressing mode is known as Inherent Addressing. Examples include SLEEP, RESET and DAW.

quebrar o bit de fusível do microcontrolador protegido MICROCHIP PIC18F4523 para restaurar o código-fonte protetor MCU PIC18F4523 da memória flash do programa e da memória eeprom de dados, copiar o código-fonte no formato de arquivo binário ou software heximal para o novo microprocessador MICROCHIP PIC18F4523;
Other instructions work in a similar way but require an additional explicit argument in the opcode to Break Chip SAF-C164CI-8EM Firmware. This is known as Literal Addressing mode because they require some literal value as an argument. Examples include ADDLW and MOVLW, which respectively, add or move a literal value to the W register. Other examples include CALL and GOTO, which include a 20-bit program memory address.
cracker le bit de fusible du microcontrôleur sécurisé MICROCHIP PIC18F4523 pour restaurer le code source de protection du MCU PIC18F4523 à partir de la mémoire flash du programme et de la mémoire eeprom de données, copier le code source au format de fichier binaire ou de logiciel heximal vers le nouveau microprocesseur MICROCHIP PIC18F4523 ;
Direct Addressing mode specifies all or part of the source and/or destination address of the operation within the opcode itself. The options are specified by the arguments accompanying the instruction.
In the core PIC18 instruction set, bit-oriented and byte- oriented instructions use some version of Direct Addressing by default to better support Break Microcontroller PIC12F629 Program. All of these instructions include some 8-bit literal address as their Least Significant Byte when PIC18F4523 Microcontroller Embedded Memory Breaking. This address specifies either a register address in one of the banks of data RAM through Crack MCU memory.
The Access RAM bit ‘a’ determines how the address is interpreted. When ‘a’ is ‘1’, the contents of the BSR (Section 5.3.1 “Bank Select Register (BSR)”) are used with the address to determine the complete 12-bit address of the register. When ‘a’ is ‘0’, the address is interpreted as being a register in the Access Bank to facilitate the process of Break MCU dsPIC30F4011 Heximal. Addressing that uses the Access RAM is sometimes also known as Direct Forced Addressing mode.

złamanie zabezpieczonego bezpiecznika mikrokontrolera MICROCHIP PIC18F4523 w celu przywrócenia ochronnego kodu źródłowego MCU PIC18F4523 z pamięci flash programu i pamięci eeprom danych, skopiowanie kodu źródłowego w formacie pliku binarnego lub oprogramowania szesnastkowego do nowego mikroprocesora MICROCHIP PIC18F4523;
 Microprocessor PIC18F4520 Program Memory Data Retrieving
Microprocessor PIC18F4520 Program Memory Data Retrieving
The STATUS register, shown in Register 5-2, contains the arithmetic status of the ALU to provide the purpose of Microprocessor PIC18F4520 Program Memory Data Retrieving. As with any other SFR, it can be the operand for any instruction.
защитена микропроцесорна програма за флаш памет PIC18F4520 и извличане на данни от паметта на eeprom трябва да декапсулира силиконов пакет на заключен бит на предпазителя на микроконтролера PIC18F4520, да разбие MCU PIC18F4520 система за устойчивост на фалшифициране и да копира вградения фърмуер във формат двоичен или шестнадесетичен;
If the STATUS register is the destination for an instruc- tion that affects the Z, DC, C, OV or N bits, the results of the instruction are not written; instead, the STATUS register is updated according to the instruction performed by Recover MCU P89LPC925FDH Heximal. Therefore, the result of an instruction with the STATUS register as its destination may be different than intended when Crack MCU eeprom. As an example, CLRF STATUS will set the Z bit and leave the remaining Status bits unchanged (‘000u u1uu’).
It is recommended that only BCF, BSF, SWAPF, MOVFF and MOVWF instructions are used to alter the STATUS register, because these instructions do not affect the Z, C, DC, OV or N bits in the STATUS register.

zabezpieczony program pamięci flash mikroprocesora PIC18F4520 i pobieranie danych z pamięci eeprom wymaga dekapsulacji pakietu krzemowego zablokowanego bitu bezpiecznika mikrokontrolera PIC18F4520, złamania układu odporności na manipulacje MCU PIC18F4520 i skopiowania wbudowanego oprogramowania w formacie binarnym lub szesnastkowym;
While the program memory can be addressed in only one way – through the program counter – information in the data memory space can be addressed in several ways and Copy Chip SAF-XC888CM-8FFI Binary is one of them. For most instructions, the addressing mode is fixed. Other instructions may use up to three modes, depending on which operands are used by Copy Microcontroller AT89C51RE2 Binary and whether or not the extended instruction set is enabled.

يحتاج برنامج ذاكرة فلاش المعالج الدقيق PIC18F4520 واسترداد بيانات ذاكرة eeprom إلى فك حزمة السيليكون الخاصة بوحدة التحكم الدقيقة المقفلة PIC18F4520، وكسر نظام مقاومة العبث MCU PIC18F4520 ونسخ البرامج الثابتة المضمنة بتنسيق ثنائي أو سداسي؛
The addressing modes are:
- Inherent
- Literal
- Direct
- Indirect
An additional addressing mode, Indexed Literal Offset, is available when the extended instruction set is enabled (XINST Configuration bit = 1).
 Microchip PIC18F4515 Embedded Firmware Restoration
Microchip PIC18F4515 Embedded Firmware Restoration
Microchip PIC18F4515 Embedded Firmware Restoration is a process to extract the embedded heximal from PIC18F4515 after crack microcontroller PIC18F4515 protection system;
The instruction is forced to use the Access Bank address map; the current value of the BSR is ignored entirely due to the process of Attack Microcontroller W77E058A40DL Flash. Using this “forced” addressing allows the instruction to operate on a data address in a single cycle which will facilitate Microchip PIC18F4515 Embedded Firmware Restoration, without updating the BSR first. For 8-bit addresses of 80h and above, this means that users can evaluate and operate on SFRs more efficiently.

فك تشفير فلاش المعالج الدقيق PIC18F4515 هو عملية لإزالة آلية مقاومة العبث لذاكرة فلاش PIC18F4515 المؤمنة وذاكرة eeprom، ونسخ البرامج الثابتة المضمنة لوحدة التحكم الدقيقة PIC18F4515 المقفلة للبرنامج الثنائي أو البيانات السداسية إلى نسخة أخرى من MCU PIC18F4515 والتي ستوفر نفس وظائف الإصدار الأصلي
The Access RAM below 80h is a good place for data values that the user might need to access rapidly, such as immediate computational results or common program variables by Attack MCU ATMEGA162 Flash. Access RAM also allows for faster and more code efficient context saving and switching of variables.
The mapping of the Access Bank is slightly different when the extended instruction set is enabled (XINST Configuration bit = 1). This is discussed in more detail in Section 5.5.3 “Mapping the Access Bank in Indexed Literal Offset Mode”.
PIC18F4515 devices may have banked memory in the GPR area. This is data RAM which is available for use by all instructions. GPRs start at the bottom of Bank 0 (address 000h) and grow downwards towards the bottom of the SFR area. GPRs are not initialized by a Power-on Reset and are unchanged on all other Resets.
The Special Function Registers (SFRs) are registers used by the CPU and peripheral modules for controlling the desired operation of the device when Microchip PIC18F4515 Embedded Firmware Restoration. These registers are implemented as static RAM. SFRs start at the top of data memory (FFFh) and extend downward to occupy the top half of Bank 15 (F80h to FFFh).

Dekodowanie flash mikroprocesora PIC18F4515 to proces mający na celu usunięcie mechanizmu zabezpieczającego przed manipulacją zabezpieczonej pamięci flash mikrochipu PIC18F4515 i pamięci eeprom, kopiowanie zablokowanego oprogramowania układowego mikrokontrolera PIC18F4515 wbudowanego programu binarnego lub danych szesnastkowych do innego klona MCU PIC18F4515, który zapewni te same funkcje co wersja oryginalna
The SFRs can be classified into two sets: those associated with the “core” device functionality (ALU, Resets and interrupts) and those related to the peripheral functions obtained from Copy MCU AT89C55WD Binary. The Reset and Interrupt registers are described in their respective chapters, while the ALU’s STATUS register is described later in this section.
Registers related to the operation of a peripheral feature are described in the chapter for that peripheral. The SFRs are typically distributed among the peripherals whose functions they control. Unused SFR locations are unimplemented and read as ‘0’s to Crack MCU.

Флаш декодирането на микропроцесор PIC18F4515 на микрочип е процес за премахване на механизма за защита срещу фалшифициране на защитен микрочип PIC18F4515 флаш памет и eeprom памет, копиране на заключен микроконтролер PIC18F4515, вграден фърмуер на двоична програма или шестнадесетични данни в друг клонинг MCU PIC18F4515, който ще осигури същите функции като оригиналната версия
 Microprocessor PIC18F4510 Eeprom Memory Breaking
Microprocessor PIC18F4510 Eeprom Memory Breaking
Protective microprocessor PIC18F4510 eeprom data memory and flash program memory breaking needs to crack secured MICROCHIP MCU PIC18F4510 fuse bit, unlock microcontroller PIC18F4510 and readout embedded firmware in the format of binary file or heximal data;
While the use of the BSR with an embedded 8-bit address allows users to address the entire range of data memory which can facilitate Microprocessor PIC18F4510 Eeprom Memory Breaking, it also means that the user must always ensure that the correct bank is selected. Otherwise, data may be read from or written to the wrong location.

la memoria dati eeprom del microprocessore protettivo PIC18F4510 e la rottura della memoria del programma flash necessitano di crack protetti, bit fusibile MICROCHIP MCU PIC18F4510, sblocco del microcontrollore PIC18F4510 e lettura del firmware incorporato nel formato di file binario o dati essimali;
This can be disastrous if a GPR is the intended target of an operation, but an SFR is written to instead. Verifying and/or changing the BSR for each read or write to data memory can become very inefficient.
To streamline access for the most commonly used data memory locations, the data memory is configured with an Access Bank, which allows users to access a mapped block of memory without specifying a BSR. The Access Bank consists of the first 128 bytes of memory (00h-7Fh) in Bank 0 and the last 128 bytes of memory (80h-FFh) in Block 15.

Microprocessor PIC18F4510 Eeprom Memory Breaking
The lower half is known as the “Access RAM” and is composed of GPRs. This upper half is also where the device’s SFRs are mapped. These two areas are mapped contiguously in the Access Bank and can be addressed in a linear fashion by an 8-bit address.

koruyucu mikroişlemci PIC18F4510 eeprom veri belleği ve flash program belleği kırma, güvenli MICROCHIP MCU PIC18F4510 sigorta bitini kırmalı, mikrodenetleyici PIC18F4510’un kilidini açmalı ve yerleşik bellenimi ikili dosya veya onaltılı veri formatında okumalıdır;
The Access Bank is used by core PIC18F4510 instructions that include the Access RAM bit (the ‘a’ parameter in the instruction). When ‘a’ is equal to ‘1’, the instruction uses the BSR and the 8-bit address included in the opcode for the data memory address. When ‘a’ is ‘0’,
 PIC18F4480 Microcontroller Memory Data Recovering
PIC18F4480 Microcontroller Memory Data Recovering
PIC18F4480 secured microcontroller memory data recovering can help engineer to extract embedded firmware of binary code or heximal file from locked microprocessor PIC18F4480 after crack MCU’s tamper resistance system and copy flash memory content with eeprom memory data

Il recupero sicuro dei dati della memoria del microcontroller PIC18F4480 può aiutare l’ingegnere a estrarre il firmware incorporato del codice binario o del file esimale dal microprocessore bloccato PIC18F4480 dopo il crack del sistema di resistenza alla manomissione dell’MCU e a copiare il contenuto della memoria flash con i dati della memoria eeprom
Large areas of data memory require an efficient addressing scheme to make rapid access to any address possible which can provide great benefit for PIC18F4480 Microcontroller Memory Data Recovering. Ideally, this means that an entire address does not need to be provided for each read or write operation. For PIC18 devices, this is accom- plished with a RAM banking scheme.
PIC18F4480 Microcontroller Memory Data Recovering
This divides the memory space into 16 contiguous banks of 256 bytes. Depending on the instruction, each location can be addressed directly by its full 12-bit address, or an 8-bit low-order address and a 4-bit Bank Pointer.
Most instructions in the PIC18F4480 instruction set make use of the Bank Pointer, known as the Bank Select Register (BSR). This SFR holds the 4 Most Significant bits of a location’s address; the instruction itself includes the 8 Least Significant bits.
Only the four lower bits of the BSR are implemented (BSR3:BSR0). The upper four bits are unused; they will always read ‘0’ and cannot be written to. The BSR can be loaded directly by using the MOVLB instruction.

PIC18F4480 güvenli mikrodenetleyici bellek verilerinin kurtarılması, mühendisin, MCU’nun kurcalamaya karşı koruma sistemini kırdıktan ve eeprom bellek verileriyle flash bellek içeriğini kopyaladıktan sonra kilitli mikroişlemci PIC18F4480’den gömülü ikili kod veya onaltılık dosya yazılımını çıkarmasına yardımcı olabilir
The value of the BSR indicates the bank in data memory; the 8 bits in the instruction show the location in the bank and can be thought of as an offset from the bank’s lower boundary. The relationship between the BSR’s value and the bank division in data memory is shown in below Figure.
Since up to 16 registers may share the same low-order address, the user must always be careful to ensure that the proper bank is selected before performing a data read or write. For example, writing what should be program data to an 8-bit address of F9h while the BSR is 0Fh will end up resetting the program counter.
While any bank can be selected, only those banks that are actually implemented can be read or written to. Writes to unimplemented banks are ignored, while reads from unimplemented banks will return ‘0’s. Even so, the STATUS register will still be affected as if the operation was successful. The data memory map in Figure 5-5 indicates which banks are implemented.

A PIC18F4480 védett mikrokontroller memóriaadatainak helyreállítása segíthet a mérnöknek a bináris kód vagy heximális fájl beágyazott firmware-jének kinyerésében a zárolt PIC18F4480 mikroprocesszorból az MCU szabotázsellenállási rendszerének feltörését követően, és a flash memória tartalmát az eeprom memóriaadatokkal másolhatja.
 Recover Microprocessor PIC18F4458 Firmware Data
Recover Microprocessor PIC18F4458 Firmware Data
Recover microprocessor PIC18F4458 firmware data is a process to crack microchip microcontroller PIC18F4458 read-out protection and decrypt tamper resistance system, copy binary program and heximal file from encrypted MCU PIC18F4458’s flash memory and eeprom memory;

Recuperar datos de firmware del microprocesador PIC18F4458 es un proceso para descifrar la protección de lectura del microcontrolador PIC18F4458 y descifrar el sistema de resistencia a manipulaciones, copiar programas binarios y archivos heximal desde la memoria flash y la memoria eeprom del MCU PIC18F4458 cifrado;
Device Resets on stack overflow and stack underflow conditions are enabled by setting the STVREN bit in Configuration Register 4L. When STVREN is set, a full or underflow will set the appropriate STKFUL or STKUNF bit and then cause a device Reset when Recover Microprocessor PIC18F4458 Firmware Data.
When STVREN is cleared, a full or underflow condition will set the appropriate STKFUL or STKUNF bit but not cause a device Reset after Recover MCU PIC18F2520 Binary. The STKFUL or STKUNF bits are cleared by the user software or a Power-on Reset.

Recover Microprocessor PIC18F4458 Firmware Data
A fast register stack is provided for the STATUS, WREG and BSR registers, to provide a “fast return” option for interrupts to Crack MCU. The stack for each register is only one level deep and is neither readable nor writable after Recover IC AT89C4051 Heximal. It is loaded with the current value of the corresponding register when the processor vectors for an interrupt.

استعادة بيانات البرامج الثابتة للمعالج الدقيق PIC18F4458 هي عملية لكسر حماية قراءة وحدة التحكم الدقيقة PIC18F4458 وفك تشفير نظام مقاومة العبث، ونسخ البرنامج الثنائي والملف السداسي من ذاكرة فلاش MCU PIC18F4458 المشفرة وذاكرة eeprom؛
All interrupt sources will push values into the stack registers. The values in the registers are then loaded back into their associated registers if the RETFIE, FAST instruction is used to return from the interrupt after Copy Microcontroller P87C51X2BBD Binary.
If both low and high priority interrupts are enabled, the stack registers cannot be used reliably to return from low priority interrupts. If a high priority interrupt occurs while servicing a low priority interrupt, the stack register values stored by the low priority interrupt will be overwritten for the purpose of Copy MCU Atmega32A Software. In these cases, users must save the key registers in software during a low priority interrupt.

Восстановление данных прошивки микропроцессора PIC18F4458 — это процесс взлома защиты от считывания микроконтроллера PIC18F4458 и расшифровки системы защиты от несанкционированного доступа, копирования двоичной программы и шестнадцатеричного файла из зашифрованной флэш-памяти MCU PIC18F4458 и памяти EEPROM;