 Hack IC firmware
Hack IC firmware
Hack IC firmware can be used for different purposes depending on the goal. Sometimes copying a profitable on-the-market product can give easy money. Larger manufacturers could consider stealing intellectual property (IP) from the device and mixing it with their own IP to disguise the theft.
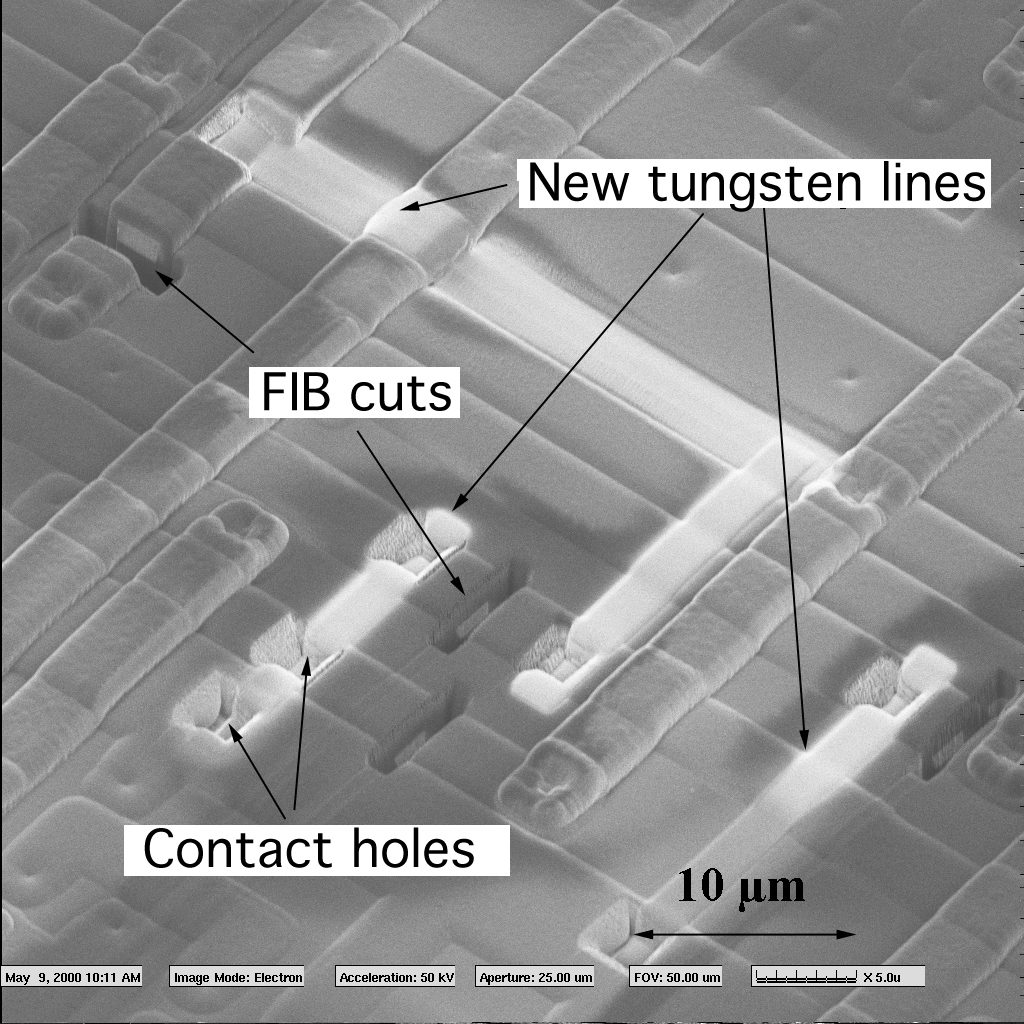
Others could try to steal secrets from the device either to produce a competitive product or to steal service. Product designers should first think about the possible motives for cracking microcontroller memory their devices and then concentrate on the protection mechanisms. The following MCU IC processsor Hacking scenarios should be considered during the system design.
Failure analysis involves testing and debugging silicon chips after fabrication. Very often the chip does not function in the required way, so the manufacturer wants to investigate the problem and fix it in the next revision of the die. When a new technological process or memory type is being developed, failure analysis techniques are used to measure all the parameters and make necessary alterations in further designs. Obviously such tools should provide the ability to observe signals at any point of the chip and, if necessary, make modifications to the silicon design. From the attacker’s point of view, a perfect failure analysis tool gives the ultimate
capability to circumvent security protection. It allows connection to any point on the chip die, and lets him disable the security protection by modifying the security circuit. Fortunately, with constant technological progress resulting in a significant reduction of the transistor feature
sizes, failure analysis becomes more and more complicated and expensive. It also forces the attackers to be more and more knowledgeable and experienced. Of course, not all failure analysis techniques are useful for breaking the security of chips. For example, an attacker is not interested in cross sectioning the chip, transistor sizes, thickness of the gate oxide or metallization.