 Extract DSP CPLD Encrypted Software
Extract DSP CPLD Encrypted Software
Extract DSP CPLD Encrypted Software from memory start from disable the tamper resistance, by using MCU invasive cracking will help to disclose the internal structure of CPLD chip;
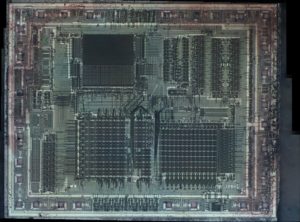
Extract DSP CPLD Encrypted Software from memory start from disable the tamper resistance, by using MCU invasive cracking will help to disclose the internal structure of CPLD chip
When it comes to reverse engineering smartcards and microcontrollers, both structural and program-code reverse engineering are required to understand how the device works. First, the security protection needs to be understood by partial reverse engineering of the chip area associated with it. Thus if memory bus encryption was used, the hardware responsible for this should be reverse engineered. Then, finally, the internal memory contents have to be extracted and disassembled to understand device functions.