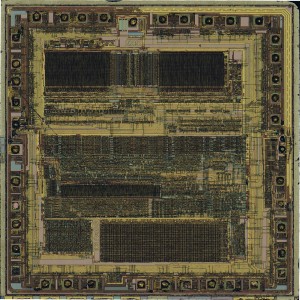
Archive for the ‘Recover MCU’ Category
 Attack IC MB90F598 Firmware
Attack IC MB90F598 Firmware
We can Break IC MB90F598 Firmware, please view the IC MB90F598 features below for your reference:
The MB90595/595G series with FULL-CAN*1 interface and FLASH ROM is especially designed for automotive and industrial applications. Its main features are two on board CAN Interfaces, which conform to V2.0 Part A and Part B, while supporting a very flexible message buffer scheme and so offering more functions than a normal full CAN approach when Attack IC.
The instruction set of F2MC-16LX CPU core inherits an AT architecture of the F2MC*2 family with additional instruction sets for high-level languages, extended addressing mode, enhanced multiplication/division instructions, and enhanced bit manipulation instructions. The microcontroller has a 32-bit accumulator for processing long word data after Attack IC.
The MB90595/595G series has peripheral resources of 8/10-bit A/D converters, UART (SCI), extended I/O serial interface, 8/16-bit PPG timer, I/O timer (input capture (ICU), output compare (OCU)) and stepping motor controller if Attack IC.
*1: Controller Area Network (CAN) – License of Robert Bosch GmbH
*2: F2MC stands for FUJITSU Flexible Microcontroller.
Clock
Embedded PLL clock multiplication circuit
Operating clock (PLL clock) can be selected from divided-by-2 of oscillation or one to four times the oscillation (at oscillation of 4 MHz, 4 MHz to 16 MHz) before Attack IC.
Minimum instruction execution time: 62.5 ns (operation at oscillation of 4 MHz, four times the oscillation clock, VCC of 5.0 V)
Instruction set to optimize controller applications
Rich data types (bit, byte, word, long word)
Rich addressing mode (23 types)
Enhanced signed multiplication/division instruction and RETI instruction functions after Attack IC
Enhanced precision calculation realized by the 32-bit accumulator
· Instruction set designed for high level language (C language) and multi-task operations
Adoption of system stack pointer
Enhanced pointer indirect instructions
Barrel shift instructions
· Program patch function (for two address pointers)
· Enhanced execution speed: 4-byte instruction queue
· Enhanced interrupt function: 8 levels, 34 factors when Attack IC
· Automatic data transmission function independent of CPU operation
Extended intelligent I/O service function (EI2OS): Up to 10 channels
· Embedded ROM size and types
Mask ROM: 128 Kbytes
Flash ROM: 128 Kbytes
Embedded RAM size: 4 Kbytes (MB90V595/595G : 6 Kbytes)
· Flash ROM
Supports automatic programming, Embedded Algorithm TM*
Write/Erase/Erase-Suspend/Resume commands after Attack IC
A flag indicating completion of the algorithm
Hard-wired reset vector available in order to point to a fixed boot sector
Erase can be performed on each block
Block protection with external programming voltage
· Low-power consumption (stand-by) mode
Sleep mode (mode in which CPU operating clock is stopped)
Stop mode (mode in which oscillation is stopped)
CPU intermittent operation mode
Hardware stand-by mode
· Process: 0.5 µm CMOS technology
· I/O port
General-purpose I/O ports: 78 ports
Push-pull output and Schmitt trigger input.
Programmable on each bit as I/O or signal for peripherals for Attack IC.
· Timer
Watchdog timer: 1 channel
8/16-bit PPG timer: 8/16-bit × 6 channels
16-bit re-load timer: 2 channels
· 16-bit I/O timer
Input capture: 4 channels
Output compare: 4 channels
· Extended I/O serial interface: 1 channel
· UART0
With full-duplex double buffer (8-bit length)
Clock asynchronized or clock synchronized (with start/stop bit) transmission can be selectively used.
UART1 (SCI)
With full-duplex double buffer (8-bit length)
Clock asynchronized or clock synchronized serial transmission (I/O extended transmission) can be selectively used if Attack IC.
· Stepping motor controller (4 channels)
· External interrupt circuit (8 channels)
A module for starting an extended intelligent I/O service (EI2OS) and generating an external interrupt which is triggered by an external input.
· Delayed interrupt generation module: Generates an interrupt request for switching tasks.
· 8/10-bit A/D converter (8 channels)
8/10-bit resolution can be selectively used.
Starting by an external trigger input.
· FULL-CAN interface: 1 channel
Conforming to Version 2.0 Part A and Part B
Flexible message buffering (mailbox and FIFO buffering can be mixed) after Attack IC
· 18-bit Time-base counter
· External bus interface: Maximum address space 16 Mbytes
*: Embedded Algorithm is a trademark of Advanced Micro Devices Inc.
 Attack Chip ATmega8A Binary
Attack Chip ATmega8A Binary
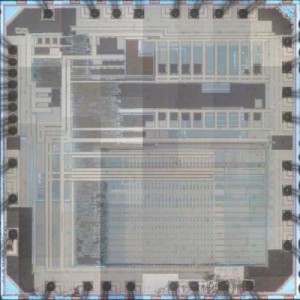
Attack Chip ATmega8A secured system, unlock microcontroller ATmega8A flash and eeprom memory, extract binary from both of the memories in the format of heximal which can be used for microcontroller copying
Attack Chip ATmega8A secured system, unlock microcontroller ATmega8A flash and eeprom memory, extract binary from both of the memories in the format of heximal which can be used for microcontroller copying;
Features
· High-performance, Low-power AVR® 8-bit Microcontroller
· Advanced RISC Architecture
– 130 Powerful Instructions – Most Single-clock Cycle Execution
– 32 x 8 General Purpose Working Registers when Chip PIC16F84A binary copying
– Fully Static Operation
– Up to 16 MIPS Throughput at 16 MHz
– On-chip 2-cycle Multiplier
High Endurance Non-volatile Memory segments
– 8K Bytes of In-System Self-programmable Flash program memory
– 512 Bytes EEPROM
– 1K Byte Internal SRAM
– Write/Erase Cycles: 10,000 Flash/100,000 EEPROM
– Data retention: 20 years at 85°C/100 years at 25°C(1)
– Optional Boot Code Section with Independent Lock Bits
· In-System Programming by On-chip Boot Program
· True Read-While-Write Operation
8-bit with 8K Bytes In-System Programmable
– Programming Lock for Software Security
Peripheral Features
– Two 8-bit Timer/Counters with Separate Prescaler, one Compare Mode
– One 16-bit Timer/Counter with Separate Prescaler, Compare Mode, and Capture Mode
– Real Time Counter with Separate Oscillator after IC C8051F530 Firmware attacking
– Three PWM Channels
– 8-channel ADC in TQFP and QFN/MLF package
· Eight Channels 10-bit Accuracy
– 6-channel ADC in PDIP package
· Six Channels 10-bit Accuracy
– Byte-oriented Two-wire Serial Interface
– Programmable Serial USART
– Master/Slave SPI Serial Interface
– Programmable Watchdog Timer with Separate On-chip Oscillator
– On-chip Analog Comparator
Special Microcontroller Features
– Power-on Reset and Programmable Brown-out Detection
– Internal Calibrated RC Oscillator
– External and Internal Interrupt Sources
– Five Sleep Modes: Idle, ADC Noise Reduction, Power-save, Power-down, and Standby
I/O and Packages
– 23 Programmable I/O Lines
– 28-lead PDIP, 32-lead TQFP, and 32-pad QFN/MLF
Operating Voltages
– 2.7 – 5.5V for ATmega8A
Speed Grades
– 0 – 16 MHz for ATmega8A
Power Consumption at 4 Mhz, 3V, 25°C
Flash ATmega8A
– Active: 3.6 mA
– Idle Mode: 1.0 mA
– Power-down Mode: 0.5 µA
 Attack Microcontroller PIC16C63A Heximal
Attack Microcontroller PIC16C63A Heximal
Attack Microcontroller PIC16C63A protective memory and readout heximal of MCU PIC16C63A flash memory, microprocessor PIC16C63A unlocking process will normally start from chip surface decapsulation;

Attack Microcontroller PIC16C63A protective memory and readout heximal of MCU PIC16C63A flash memory, microprocessor PIC16C63A unlocking process will normally start from chip surface decapsulation
Devices included in this data sheet:
PIC16C7X Peripheral Features:
· Timer0: 8-bit timer/counter with 8-bit prescaler
· Timer1: 16-bit timer/counter with prescaler can be incremented during SLEEP via external
PIC16CXX Microcontroller Core Features:
· High performance RISC CPU
· Only 35 single word instructions to learn
· All single cycle instructions except for program branches which are two cycle
· Operating speed: DC – 20 MHz clock input
DC – 200 ns instruction cycle
· 4 K x 14 words of Program Memory,
192 x 8 bytes of Data Memory (RAM)
· Interrupt capability
· Eight-level deep hardware stack
· Direct, indirect and relative addressing modes
· Power-on Reset (POR)
· Power-up Timer (PWRT) and Oscillator Start-up Timer (OST)
· Watchdog Timer (WDT) with its own on-chip RC oscillator for reliable operation
· Programmable code protection
· Power-saving SLEEP mode crystal/clock
· Timer2: 8-bit timer/counter with 8-bit period register, prescaler and postscaler
· Capture, Compare, PWM modules
– Capture is 16-bit, max. resolution is 200 ns
– Compare is 16-bit, max. resolution is 200 ns
– PWM max. resolution is 10-bit
· 8-bit multichannel Analog-to-Digital converter
· Synchronous Serial Port (SSP) with SPITM and I2CTM
· Universal Synchronous Asynchronous Receiver Transmitter (USART/SCI)
· Parallel Slave Port (PSP), 8-bits wide with external RD, WR and CS controls when Attack Microcontroller
· Brown-out detection circuitry for Brown-out Reset (BOR) Pin Diagram: PDIP, Windowed CERDIP
· Selectable oscillator options
· Low power, high speed CMOS EPROM technology
· Wide operating voltage range: 2.5V to 5.5V
· High Sink/Source Current 25/25 mA
· Commercial, Industrial and Automotive temperature ranges
· Low power consumption:
– < 5 mA @ 5V, 4 MHz
– 23 mA typical @ 3V, 32 kHz
– < 1.2 mA typical standby current
 Attack MCU PIC16CE625 Program
Attack MCU PIC16CE625 Program
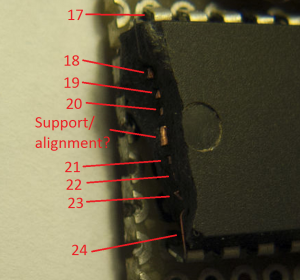
Attack MCU PIC16CE625 locked memory and extract program from Microcontroller PIC16CE625 flash memory, disable the security fuse bit after crack Microprocessor PIC16CE625 so the microprobes will be able to get access to the internal memory
Attack MCU PIC16CE625 locked memory and extract program from Microcontroller PIC16CE625 flash memory, disable the security fuse bit after crack Microprocessor PIC16CE625 so the microprobes will be able to get access to the internal memory;
Interrupt capability 16 special function hardware registers
8-level deep hardware stack
Direct, Indirect and Relative addressing modes
Peripheral Features:
· 13 I/O pins with individual direction control
· High current sink/source for direct LED drive
· Analog comparator module with:
– Two analog comparators
– Programmable on-chip voltage reference (VREF) module
– Programmable input multiplexing from device inputs and internal voltage reference
– Comparator outputs can be output signals
· Timer0: 8-bit timer/counter with 8-bit programmable prescaler
Special Microcontroller Features:
· In-Circuit Serial Programming (ICSP™) (via two pins)
· Power-on Reset (POR)
· Power-up Timer (PWRT) and Oscillator Start-up Timer (OST)
· Brown-out Reset
· Watchdog Timer (WDT) with its own on-chip RC oscillator for reliable operation
Special Microcontroller Features (cont’d)
· 1,000,000 erase/write cycle EEPROM data memory
· EEPROM data retention > 40 years
· Programmable code protection
· Power saving SLEEP mode
· Selectable oscillator options
· Four user programmable ID locations
CMOS Technology:
· Low-power, high-speed CMOS EPROM/EEPROM technology
· Fully static design
· Wide operating voltage range – 2.5V to 5.5V
· Commercial, industrial and extended temperature range
· Low power consumption
– < 2.0 mA @ 5.0V, 4.0 MHz
– 15 mA typical @ 3.0V, 32 kHz
– < 1.0 mA typical standby current @ 3.0V
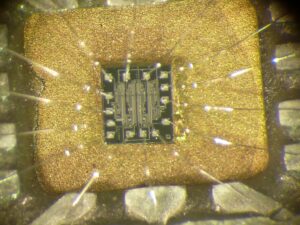
 Attack Microcontroller ST62T15C6 firmware
Attack Microcontroller ST62T15C6 firmware
The ST62T15C6 is an 8-bit microcontroller from STMicroelectronics, commonly used in embedded systems. Security researchers and hardware hackers often attempt to attack, crack, or reverse engineer its firmware for analysis, recovery, or cloning purposes. This article explores various techniques used to extract, decode, or dump the firmware from the ST62T15C6 microcontroller.
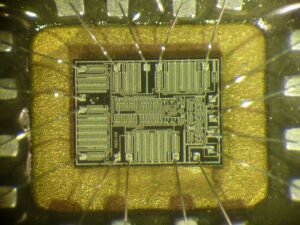
O ST62T15C6 é um microcontrolador de 8 bits da STMicroelectronics, comumente usado em sistemas embarcados. Pesquisadores de segurança e hackers de hardware frequentemente tentam atacar, crackear ou fazer engenharia reversa em seu firmware para fins de análise, recuperação ou clonagem. Este artigo explora várias técnicas usadas para extrair, decodificar ou despejar o firmware do microcontrolador ST62T15C6.
1. Firmware Extraction Methods
Dumping Flash Memory
The primary method to attack the ST62T15C6 involves dumping the contents of its flash memory or EEPROM memory. Since the firmware is stored in non-volatile memory, attackers use hardware tools like:
- Programmers/JTAG interfaces – If debug ports are accessible, firmware can be read directly.
- Logic analyzers & bus sniffers – Monitoring communication between the MCU and external memory (if any).
- Voltage glitching – Disrupting power or clock signals to bypass read protections.
Decapsulation & Microprobing
If security fuses are enabled, attackers may resort to decapsulating the chip to access the silicon die. Using microprobing, they can directly read the binary code from the memory cells. This method is expensive and requires advanced equipment.
ST62T15C6 — это 8-битный микроконтроллер от STMicroelectronics, обычно используемый во встраиваемых системах. Исследователи безопасности и хакеры оборудования часто пытаются атаковать, взломать или провести обратную разработку его прошивки для анализа, восстановления или клонирования. В этой статье рассматриваются различные методы, используемые для извлечения, декодирования или дампа прошивки из микроконтроллера ST62T15C6.
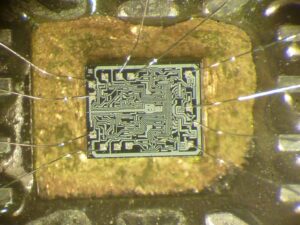
2. Reverse Engineering the Firmware
Once the heximal data or binary code is extracted, the next step is decoding or disassembling it. Common techniques include:
- Static analysis – Using disassemblers like Ghidra or IDA Pro to convert machine code into assembly.
- Dynamic analysis – Running the firmware in an emulator (e.g., QEMU) to observe behavior.
- Pattern recognition – Searching for known opcode sequences to identify functions.
Since the ST62T15C6 uses a proprietary architecture, custom tools may be needed to decrypt the program file fully.
3. Cloning & Firmware Modification
After successful extraction, attackers may:
- Copy the firmware to another ST62T15C6 chip.
- Modify the source code (if decompiled) to remove security checks.
- Restore corrupted firmware for device recovery.
4. Protection & Countermeasures
To prevent such attacks, manufacturers implement:
- Read-out protection bits – Locking firmware access.
- Encrypted firmware updates – Preventing easy decoding.
- Secure boot mechanisms – Blocking unauthorized code execution.
Conclusion
يُعد ST62T15C6 متحكمًا دقيقًا ثماني البتات من شركة STMicroelectronics، ويُستخدم عادةً في الأنظمة المدمجة. غالبًا ما يحاول باحثو الأمن ومخترقو الأجهزة مهاجمة أو اختراق أو عكس هندسة البرنامج الثابت الخاص به لأغراض التحليل أو الاستعادة أو الاستنساخ. تستكشف هذه المقالة التقنيات المختلفة المستخدمة لاستخراج أو فك تشفير أو تفريغ البرنامج الثابت من المتحكم الدقيق ST62T15C6
Attacking the ST62T15C6 microcontroller firmware requires a mix of hardware and software techniques, from dumping flash memory to reverse engineering binary code. While these methods can be used for legitimate recovery or research, they also pose security risks if exploited maliciously. Developers must implement strong protections to safeguard their firmware from unauthorized cloning or decryption.

Attack Microcontroller ST62T15C6 protective system and extract firmware from MCU ST62T15 memory, the whole tamper resistance system will be disable by Microprocessor unlocking technique
Attack Microcontroller ST62T15C6 protective system and extract firmware from MCU ST62T15 memory, the whole tamper resistance system will be disable by Microprocessor unlocking technique;
Memories
– 2K or 4K bytes Program memory (OTP, EPROM, FASTROM or ROM) with read-out protection
– 64 bytes RAM
Clock, Reset and Supply Management
– Enhanced reset system
– Low Voltage Detector (LVD) for Safe Reset
– Clock sources: crystal/ceramic resonator or RC network, external clock, backup oscillator (LFAO)
– Oscillator Safeguard (OSG)
– 2 Power Saving Modes: Wait and Stop
Interrupt Management
– 4 interrupt vectors plus NMI and RESET
– 20 external interrupt lines (on 2 vectors)
– 1 external non-interrupt line
– 20 multifunctional bidirectional I/O lines
– 16 alternate function lines
– 4 high sink outputs (20mA)
– Configurable watchdog timer
– 8-bit timer/counter with a 7-bit prescaler
Analog Peripheral
– 8-bit ADC with 16 input channels
Instruction Set
– 8-bit data manipulation
– 40 basic instructions
– 9 addressing modes
– Bit manipulation
The ST6215C, 25C devices are low cost members mable option bytes of the OTP/EPROM versions of the ST62xx 8-bit family of microcontrol-in the ROM option list applications. All ST62xx devices are based on a building block approach: a common core is surrounded by a number of on-chip peripherals for the purpose of IC program hacking.
Circuit Engineering Company Limited continues to be recognized as the Southern China Leader in Services for IC Break, MCU attack, Chip Recover, Microcontroller Copy service. With the advancement of today’s modern circuit board technology, it is more important than ever to have specialists available to help you at a moment’s notice. Our engineering and commercial teams collectively have a vast amount of electronic experience covering field include Consumer Electronics, Industrial Automation Electronics, Wireless Communication Electronics., etc. For more information please contact us through email.
 Reverse Engineering IC Embedded Memory
Reverse Engineering IC Embedded Memory
Reverse Engineering IC Embedded Memory need to experience a series of complicate process, and there are a lot of methods to reverse engineering IC embedded memory, and faulty injection technology can be used to analyze the IC, because this technology can help to locate the security fuse.
Although through this reverse engineering IC technology can’t locate the exact locations of security fuse, especially when using the flash light to inject the faulty, but it is no necessary to find out its exact locations, because security fuse can be shielded after the vulnerability point being found.
The facility is very similar to the laser scanning, the only different point is the facility is flash lamp instead of laser, de-capsulate the IC and places it on the test socket of electrical automatic platform.
Expose part of IC under the flash lamp, and then test the security fuse status, and then the location of photo-sensitivity can be found, in where the security fuse can be found too. Not only the security fuse, include all of the control circuit can be sensible to the faulty injection when reverse engineering IC embedded memory which could be more difficult to locate the security fuse.
But from the perspective, it has nothing to do about it, the security evaluation can be instructed by using the same procedures from the vulnerable IC point on the channel, if then each point on the surface of IC can be used to locate the security fuse and confirm if it can be shielded under the exposure of flash lamp within a short period of time.
Through the two time scanning on the PIC16F84 microcontroller IC from microchip, the result of comparison when reverse engineering IC can find the transistors embedded in the security fuse. Although the result can be obtained within a short period of time, but there is one point need to illustrate, it has smaller effect on the small features IC and modern microcontroller IC with multilayer top metal layers. One of the optional method is through backside laser scanning which need more precise and more expensive facilities since there are more noises in the Microcontroller reverse engineering.
 Decrypt Microchip PIC18F2321 MCU Heximal File
Decrypt Microchip PIC18F2321 MCU Heximal File
Decrypt Microchip PIC18F2321 MCU Heximal File
Inter-peripheral communication and signalling with minimum latency CPU and DMA independent operation which can affect the Decrypt Microchip PIC18F2321 MCU Heximal File
8 Event Channels allows for up to 8 signals to be routed at the same time
Events can be generated by
– Timer/Counters (TCxn)
– Real Time Counter (RTC)
– Analog to Digital Converters (ADCx)
– Analog Comparators (ACx)
– Ports (PORTx)
– System Clock (ClkSYS)
– Software (CPU)
Events can be used by secured MCU mcu reading out
– Timer/Counters (TCxn)
– Analog to Digital Converters (ADCx)
– Digital to Analog Converters (DACx)
– Ports (PORTx)
– DMA Controller (DMAC)
– IR Communication Module (IRCOM)
The same event can be used by multiple peripherals for synchronized timing
Advanced Features
– Manual Event Generation from software (CPU)
– Quadrature Decoding
– Digital Filtering
Functions in Active and Idle mode
The Event System is a set of features for inter-peripheral communication. It enables the possibility for a change of state in one peripheral to automatically trigger actions in one or more peripherals. What changes in a peripheral that will trigger actions in other peripherals are configurable by software. It is a simple, but powerful system as it allows for autonomous control of peripherals without any use of interrupts, CPU or DMA resources when MCU CRACK.
The indication of a change in a peripheral is referred to as an event, and is usually the same as the interrupt conditions for that peripheral. Events are passed between peripherals using a dedicated routing network called the Event Routing Network. Figure 9-1 on page 17 shows a basic block diagram of the Event System with the Event Routing Network and the peripherals to which it is connected.
This highly flexible system can be used for simple routing of signals, pin functions or for sequencing of events. The maximum latency is two CPU clock cycles from when an event is generated in one peripheral, until the actions are triggered in one or more other peripherals. The Event System is functional in both Active and Idle modes.
 Microchip PIC18F2410 CPU Software Extraction
Microchip PIC18F2410 CPU Software Extraction
Microchip PIC18F2410 CPU Software Extraction
When using the DAC in S/H mode, ensure that none of the channels is running at maximum conversion rate, or ensure that the conversion rate of both channels is high enough to not require refresh. BOD will be enabled after any reset if the Microchip PIC18F2410 CPU Software Extraction can be completely properly.
If any reset source goes active, the BOD will be enabled and keep the device in reset if the VCC voltage is below the programmed BOD level. During Power-On Reset, reset will not be released until VCC is above the programmed BOD level even if the BOD is disabled.
Problem fix/Workaround
Do not set the BOD level higher than VCC even if the BOD is not used.
Both DFLLs and both oscillators has to be enabled for one to work
In order to use the automatic runtime calibration for the 2 MHz or the 32MHz internal oscillators, the DFLL for both oscillators and both oscillators has to be enabled for one to work.
Problem fix/Workaround
Enabled both the DFLLs and both oscillators when using automtics runtime calibartion for one of the internal oscillators.
Operating Frequancy and Voltage Limitation
To ensure correct operation, there is a limit on operating frequnecy and voltage. Figure 36-2 on page 95 shows the safe operating area on Microchip PIC18F2410 CPU Software Extraction.
Bandgap voltage input for the ACs cannot be changed when used for both ACs simultaneously
ADC gain stage output range is limited to 2.4V
Sampled BOD in Active mode will cause noise when bandgap is used as reference
Bandgap measurement with the ADC is non-functional when VCC is below 2.7V
BOD will be enabled after any reset
Writing EEPROM or Flash while reading any of them will not work after the ADC has increased INL error for some operating conditions DAC has increased INL or noise for some operating conditions VCC voltage scaler for AC is non-linear Maximum operating frequency below 1.76V is 8 MHz.
 Decrypt PIC18F2420 MCU Encrypted Program
Decrypt PIC18F2420 MCU Encrypted Program
Decrypt PIC18F2420 MCU Encrypted Program
Sampled BOD in Active mode will cause noise when bandgap is used as reference
Bandgap measurement with the ADC is non-functional when VCC is below 2.7V otherwise the procedures of Decrypt PIC18F2420 MCU encrypted Program will be paused.
BOD will be enabled after any reset
Writing EEPROM or locked while unlocking any of them will not work
ADC has increased INL error for some operating conditions
DAC has increased INL or noise for some operating conditions
VCC voltage scaler for AC is non-linear
Maximum operating frequency below 1.76V is 8 MHz
Bandgap voltage input for the ACs cannot be changed when used for both ACs simultaneously
If the bandgap voltage is selected as input for one Analog Comparator (AC) and then selected/deselected as input for the another AC, the first comparator will be affected for up to 1 us and could potentially give a wrong comparison result after the locked of chip being unlocked.
Problem fix/Workaround
If the Bandgap is required for both ACs simultaneously, configure the input selection for both ACs before enabling any of them.
ADC gain stage output range is limited to 2.4 V
The amplified output of the ADC gain stage will never go above 2.4 V, hence the differential input will only give correct output when below 2.4 V/gain. For the available gain settings, this gives a differential input range of:
Problem fix/Workaround
Keep the amplified voltage output from the ADC gain stage below 2.4 V in order to get a correct result, or keep ADC voltage reference below 2.4 V.
Sampled BOD in Active mode will cause noise when bandgap is used as reference
Using the BOD in sampled mode when the device is running in Active or Idle mode will add noise on the bandgap reference for ADC, DAC and Analog Comparator after the chip’s locked can be unlocked.
Problem fix/Workaround
If the bandgap is used as reference for either the ADC, DAC and Analog Comparator, the BOD must not be set in sampled mode.
Bandgap measurement with the ADC is non-functional when VCC is below 2.7V
The ADC cannot be used to do bandgap measurements when VCC is below 2.7V.
Problem fix/Workaround
If internal voltages must be measured when VCC is below 2.7V, measure the internal 1.00V reference instead of the bandgap.
BOD will be enabled after any reset from Decrypt PIC18F2420 MCU encrypted Program
If any reset source goes active, the BOD will be enabled and keep the device in reset if the VCC voltage is below the programmed BOD level. During Power-On Reset, reset will not be released until VCC is above the programmed BOD level even if the BOD is disabled before unlock chip data.
Problem fix/Workaround
Do not set the BOD level higher than VCC even if the BOD is not used.
 Readout DSP Chip TMS320LF2406APZAR Program
Readout DSP Chip TMS320LF2406APZAR Program
Readout DSP Chip TMS320LF2406APZAR Program
Before we will be able to Readout DSP Chip TMS320LF2406APZAR Program, it is necessary to know this CMOS chip structure:
High-Performance Static CMOS Technology
− 25-ns Instruction Cycle Time (40 MHz)
− 40-MIPS Performance
− Low-Power 3.3-V Design
D Based on TMS320C2xx DSP CPU Core
− Code-Compatible With F243/F241/C242
− Instruction Set and Module Compatible
With F240
D Flash (LF) and ROM (LC) Device Options
− LF240xA: LF2407A, LF2406A,
LF2403A, LF2402A
− LC240xA: LC2406A, LC2404A,
LC2403A, LC2402A
D On-Chip Memory
− Up to 32K Words x 16 Bits of Flash
EEPROM (4 Sectors) or ROM
− Programmable “Code-Security” Feature for the On-Chip Flash/ROM
− Up to 2.5K Words x 16 Bits of
Data/Program RAM
− 544 Words of Dual-Access RAM
− Up to 2K Words of Single-Access RAM
D Boot ROM (LF240xA Devices)
− SCI/SPI Bootloader
D Up to Two Event-Manager (EV) Modules (EVA and EVB), Each Includes:
− Two 16-Bit General-Purpose Timers
− Eight 16-Bit Pulse-Width Modulation (PWM) Channels Which Enable:
− Three-Phase Inverter Control
− Center- or Edge-Alignment of PWM Channels
− Emergency PWM Channel Shutdown With External PDPINTx Pin
− Programmable Deadband (Deadtime) Prevents Shoot-Through Faults
− Three Capture Units for Time-Stamping of External Events
− Input Qualifier for Select Pins
− On-Chip Position Encoder Interface Circuitry
− Synchronized A-to-D Conversion
− Designed for AC Induction, BLDC,
Switched Reluctance, and Stepper Motor Control
− Applicable for Multiple Motor and/or Converter Control
D External Memory Interface (LF2407A)
− 192K Words x 16 Bits of Total Memory:
64K Program, 64K Data, 64K I/O
D Watchdog (WD) Timer Module
D 10-Bit Analog-to-Digital Converter (ADC)
− 8 or 16 Multiplexed Input Channels
− 500-ns MIN Conversion Time
− Selectable Twin 8-State Sequencers
Triggered by Two Event Managers
D Controller Area Network (CAN) 2.0B Module (LF2407A, 2406A, 2403A)
D Serial Communications Interface (SCI)
D 16-Bit Serial Peripheral Interface (SPI)
(LF2407A, 2406A, LC2404A, 2403A)
D Phase-Locked-Loop (PLL)-Based Clock Generation
D Up to 40 Individually Programmable,
Multiplexed General-Purpose Input / Output (GPIO) Pins
D Up to Five External Interrupts (Power Drive Protection, Reset, Two Maskable Interrupts)
D Power Management:
− Three Power-Down Modes
− Ability to Power Down Each Peripheral Independently
D Real-Time JTAG-Compliant Scan-Based Emulation, IEEE Standard 1149.1† (JTAG)
D Development Tools Include:
− Texas Instruments (TI) ANSI C Compiler,
Assembler/ Linker, and Code Composer
Studio Debugger
− Evaluation Modules
− Scan-Based Self-Emulation (XDS510)
− Broad Third-Party Digital Motor Control Support D Package Options