Archive for the ‘Recover Chip’ Category
 Microchip PIC18F44K20 Processor Flash Memory Program Restoration
Microchip PIC18F44K20 Processor Flash Memory Program Restoration
Microchip PIC18F44K20 Processor Flash Memory Program Restoration is a reverse engineering process through which the fuse bit of MCU pic18f44k20 will be located and cracked, then extract locked code from microcontroller memory;
Under these conditions, the file address of the instruction is not interpreted as the lower byte of an address (used with the BSR in direct addressing), or as an 8-bit address in the Access Bank. Instead, the value is interpreted as an offset value to an Address Pointer, specified by FSR2. The offset and the contents of FSR2 are added to obtain the target address of the operation.
Any of the core PIC18 instructions that can use direct addressing are potentially affected by the Indexed Literal Offset Addressing mode. This includes all byte-oriented and bit-oriented instructions, or almost one-half of the standard PIC18 instruction set. Instructions that only use Inherent or Literal Addressing modes are unaffected.

Il ripristino del programma di memoria flash del microprocessore crittografato PIC18F44K20 di Microchip è un processo di reverse engineering attraverso il quale il bit del fusibile dell’MCU PIC18F44K20 bloccato verrà individuato e violato, quindi verrà estratto il codice sorgente bloccato nel formato di dati binari o file esimale dalla flash incorporata e dall’eeprom del microcontroller PIC18F44K20 protetto. memoria firmware;
Additionally, byte-oriented and bit-oriented instructions are not affected if they do not use the Access Bank (Access RAM bit is ‘1’), or include a file address of 60h or above. Instructions meeting these criteria will continue to execute to faciliate the process of attacking mcu pic18f13k50 flash memory. A comparison of the different possible addressing modes when the extended instruction set is enabled.

Przywracanie programu zaszyfrowanej pamięci flash mikroprocesora PIC18F44K20 to proces inżynierii odwrotnej, podczas którego bit bezpiecznika zablokowanego MCU PIC18F44K20 zostanie zlokalizowany i złamany, a następnie wyodrębniony zostanie zablokowany kod źródłowy w formacie danych binarnych lub pliku szesnastkowego z chronionej wbudowanej pamięci flash i eeprom mikrokontrolera PIC18F44K20 pamięć oprogramowania;
Those who desire to use byte-oriented or bit-oriented instructions in the Indexed Literal Offset mode should note the changes to assembler syntax for this mode. This is described in more detail in Section 24.2.1“Extended Instruction Syntax”.
 Recover MCU Layout Design Infringement
Recover MCU Layout Design Infringement
Recover MCU Layout Design without the consent of the right holder constitutes an infringement. There are two main types of microcontroller copying here, one is full replication, the other is partial replication.
The illegal copying of other people’s mcu layout designs will infringe on the continuous development of the integrated circuit industry and thus harm the public’s interests. A semiconductor manufacturer may have to spend millions of dollars to develop semiconductor chips, but a pirate company may need to spend hundreds of thousands of dollars to clone IC, so the pirate company can sell it at a lower price. Such chips have caused huge losses to manufacturers who develop chips.
This kind of illegal competition is extremely harmful to the sustainable development of the semiconductor industry. Therefore, it is necessary to crack down on this behavior, but the premise is that it can correctly identify such plagiarism and copying behavior in practice.
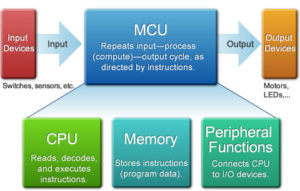
 MCU Reverse Engineering Process
MCU Reverse Engineering Process
In the development of the integrated circuit industry, MCU reverse engineering plays a huge role in promoting the faster design of MCU products with the same basic functions but better performance, smaller size and lower cost.
Integrated circuit technology is one of the fastest growing and most dynamic technologies in the world. With the continuous improvement of the performance of integrated circuits, the functions are continuously enhanced, and the application surface is expanding. The integrated circuit industry has become a pillar industry of the national economy and has become a driving force. One of the main factors in the world of today’s information society.
Experience has shown that it takes three years or longer time to completely develop a new microcontroller independently, and it takes one years or more to redesign MCU from the circuitry pattern which has been obtained from MCU reverse engineering process;
If it is MCU copied directly, It only takes three to five months. It can be seen that the application of MCU source code reverse engineering to develop Microcontrollers still requires considerable investment, so it does not deviate from the principle of fair competition.
It is precisely because of MCU reverse engineering:
1st of all, the basic principles of this technique isn’t excessively violate the fair competition. Secondly, the development of the integrated circuit industry will be vigorously promoted. Therefore, countries generally recognize MCU reverse engineering in the legislation of integrated circuits.
However, the reverse engineering is to crack MCU‘s key technology of others’ design. On the basis of this, the layout design obtained will inevitably contain the imitation and copying of the prior microcontroller layout design, so it is easy to generate infringement disputes. In the event of an infringement dispute, the accused infringer must be defended on the grounds of reverse engineering, and a series of more complicated problems will be highlighted.
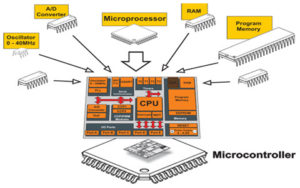
 Microcontroller with Wide Data Bus Memory Content Extraction
Microcontroller with Wide Data Bus Memory Content Extraction
The microprobing experiments showed how easily a Microcontroller with Wide Data Bus Memory Content Extraction can accomplished. The fact that only a single bit in the instruction set could defeat branch instructions could pose some security implications. Also, the presence of a weak pull-up in the data bus results in the cut bus lines to stuck at logic.
However, if a memory encryption was used this would require more sophisticated approach, for example, by injecting random data and observing the response from the CPU [12]. Nevertheless, high orthogonality of instruction sets in most RISC CPUs could help the attacker in finding the right combination to influence the MCU code execution.
Live Microcontroller decapsulation experiments proved the possibility of opening up battery powered devices without interrupting their constant power supply. This might have some consequences for highly secure applications where such devices are used. This could be medical devices or hardware security modules (HSM) used in banking or industrial applications.
Once the surface of the chip with battery-backed SRAM is accessed, the contents of the memory could be microprobed either by microprobing exposed data bus lines [12] or by exploiting test points. Both approaches though would require the use of a laser cutter to cut through passivation layer [2]. For devices fabricated with deep submicron process a Focused Ion Beam (FIB) machine will be required to establish a connection with internal data bus. However, such machines are available in many places for rent at a price below $100 per hour.
 Microcontroller Content Sensitive to External Power Supply Recovery
Microcontroller Content Sensitive to External Power Supply Recovery
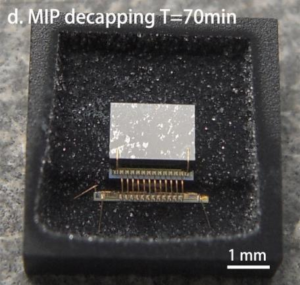
Microcontroller Content Sensitive to External Power Supply Recovery has long been viewed as impossible to crack MCU with battery powered embedded SRAM was chosen – Vasco Digipass 270 – two-factor authentication token [11]. Although such devices do not have very high level of security protection like devices with tamper resistant enclosure, they offer adequate level of protection against all sorts of MCU attacks. The reason for that is because the embedded SRAM is sensitive to the fluctuations of external power supply. Any interruption of the supply will cause the loss of data. In this case the signing key. Moreover, even the hardware reset of the device will make it inoperable, resulting in all keys and the user PIN being wiped off.
The device is relatively easy to disassemble as the internal electronics is only covered with plastic sheets glued to its plastic case. The main component of the device is a specialised microcontroller which is bonded directly to the PCB and encapsulated with epoxy. Removing the battery for more than a few seconds results in the device going into internal test mode and no longer operational.
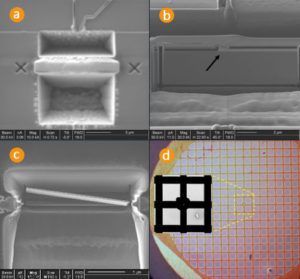
The same happens if the Reset line of the microcontroller is shorted to 0. The result of the successful partial decapsulation of the microcontroller is shown in below Figure. However, because the battery was removed for that process, the microcontroller had no useful information inside.
In order to verify the idea of live decapsulation, the PCB of the fully working token was first wrapped in an insulation tape, while the potted chip was covered with aluminium tape (below Figure). Then the whole setup was wrapped into aluminium tape before creating a cut in the tape where the decapsulation was desired.
 Secure Microcontroller Memory Recovery
Secure Microcontroller Memory Recovery
As a first target to demonstrate the affordable process of Secure Microcontroller Memory Recovery, an early 2000s smartcard was chosen. It is based on the Hitachi HD6483102 chip fabricated with 0.8μm process with 2 metal layers and has embedded Mask ROM and EEPROM.

Secure Microcontroller Memory Recovery
The Mask ROM is protected against optical MCU reading with doping encoding. The Von-Newmann RISC 16-bit CPU with H8/300 architecture of this chip allows access to all resources in the linear address space and has a relatively simple instruction set [10]. The interesting property of this instruction set is if the most significant bit equals to 1 then the CPU will always execute single-cycle instructions without any branches. This can be achieved with a laser cutter [2] and the result is shown in Fig. 3.
In order to microprobe the data bus only opening in the passivation layer is required (Fig. 4). This cavity will help in holding the tip of the needle in place during the microprobing process.
Once the CPU is forced into execution of simple instructions it will access the whole memory by fetching all the addresses sequentially. This way the memory contents can be extracted by placing a microprobing needle over each bit of the data bus one at a time and recording the information on a digital storage oscilloscope. After that all the acquisitions could be synchronised with the Reset signal.
 Microprocessor PIC18F4520 Program Memory Data Retrieving
Microprocessor PIC18F4520 Program Memory Data Retrieving
The STATUS register, shown in Register 5-2, contains the arithmetic status of the ALU to provide the purpose of Microprocessor PIC18F4520 Program Memory Data Retrieving. As with any other SFR, it can be the operand for any instruction.
защитена микропроцесорна програма за флаш памет PIC18F4520 и извличане на данни от паметта на eeprom трябва да декапсулира силиконов пакет на заключен бит на предпазителя на микроконтролера PIC18F4520, да разбие MCU PIC18F4520 система за устойчивост на фалшифициране и да копира вградения фърмуер във формат двоичен или шестнадесетичен;
If the STATUS register is the destination for an instruc- tion that affects the Z, DC, C, OV or N bits, the results of the instruction are not written; instead, the STATUS register is updated according to the instruction performed by Recover MCU P89LPC925FDH Heximal. Therefore, the result of an instruction with the STATUS register as its destination may be different than intended when Crack MCU eeprom. As an example, CLRF STATUS will set the Z bit and leave the remaining Status bits unchanged (‘000u u1uu’).
It is recommended that only BCF, BSF, SWAPF, MOVFF and MOVWF instructions are used to alter the STATUS register, because these instructions do not affect the Z, C, DC, OV or N bits in the STATUS register.

zabezpieczony program pamięci flash mikroprocesora PIC18F4520 i pobieranie danych z pamięci eeprom wymaga dekapsulacji pakietu krzemowego zablokowanego bitu bezpiecznika mikrokontrolera PIC18F4520, złamania układu odporności na manipulacje MCU PIC18F4520 i skopiowania wbudowanego oprogramowania w formacie binarnym lub szesnastkowym;
While the program memory can be addressed in only one way – through the program counter – information in the data memory space can be addressed in several ways and Copy Chip SAF-XC888CM-8FFI Binary is one of them. For most instructions, the addressing mode is fixed. Other instructions may use up to three modes, depending on which operands are used by Copy Microcontroller AT89C51RE2 Binary and whether or not the extended instruction set is enabled.

يحتاج برنامج ذاكرة فلاش المعالج الدقيق PIC18F4520 واسترداد بيانات ذاكرة eeprom إلى فك حزمة السيليكون الخاصة بوحدة التحكم الدقيقة المقفلة PIC18F4520، وكسر نظام مقاومة العبث MCU PIC18F4520 ونسخ البرامج الثابتة المضمنة بتنسيق ثنائي أو سداسي؛
The addressing modes are:
- Inherent
- Literal
- Direct
- Indirect
An additional addressing mode, Indexed Literal Offset, is available when the extended instruction set is enabled (XINST Configuration bit = 1).
 Microchip PIC18F4515 Embedded Firmware Restoration
Microchip PIC18F4515 Embedded Firmware Restoration
Microchip PIC18F4515 Embedded Firmware Restoration is a process to extract the embedded heximal from PIC18F4515 after crack microcontroller PIC18F4515 protection system;
The instruction is forced to use the Access Bank address map; the current value of the BSR is ignored entirely due to the process of Attack Microcontroller W77E058A40DL Flash. Using this “forced” addressing allows the instruction to operate on a data address in a single cycle which will facilitate Microchip PIC18F4515 Embedded Firmware Restoration, without updating the BSR first. For 8-bit addresses of 80h and above, this means that users can evaluate and operate on SFRs more efficiently.

فك تشفير فلاش المعالج الدقيق PIC18F4515 هو عملية لإزالة آلية مقاومة العبث لذاكرة فلاش PIC18F4515 المؤمنة وذاكرة eeprom، ونسخ البرامج الثابتة المضمنة لوحدة التحكم الدقيقة PIC18F4515 المقفلة للبرنامج الثنائي أو البيانات السداسية إلى نسخة أخرى من MCU PIC18F4515 والتي ستوفر نفس وظائف الإصدار الأصلي
The Access RAM below 80h is a good place for data values that the user might need to access rapidly, such as immediate computational results or common program variables by Attack MCU ATMEGA162 Flash. Access RAM also allows for faster and more code efficient context saving and switching of variables.
The mapping of the Access Bank is slightly different when the extended instruction set is enabled (XINST Configuration bit = 1). This is discussed in more detail in Section 5.5.3 “Mapping the Access Bank in Indexed Literal Offset Mode”.
PIC18F4515 devices may have banked memory in the GPR area. This is data RAM which is available for use by all instructions. GPRs start at the bottom of Bank 0 (address 000h) and grow downwards towards the bottom of the SFR area. GPRs are not initialized by a Power-on Reset and are unchanged on all other Resets.
The Special Function Registers (SFRs) are registers used by the CPU and peripheral modules for controlling the desired operation of the device when Microchip PIC18F4515 Embedded Firmware Restoration. These registers are implemented as static RAM. SFRs start at the top of data memory (FFFh) and extend downward to occupy the top half of Bank 15 (F80h to FFFh).

Dekodowanie flash mikroprocesora PIC18F4515 to proces mający na celu usunięcie mechanizmu zabezpieczającego przed manipulacją zabezpieczonej pamięci flash mikrochipu PIC18F4515 i pamięci eeprom, kopiowanie zablokowanego oprogramowania układowego mikrokontrolera PIC18F4515 wbudowanego programu binarnego lub danych szesnastkowych do innego klona MCU PIC18F4515, który zapewni te same funkcje co wersja oryginalna
The SFRs can be classified into two sets: those associated with the “core” device functionality (ALU, Resets and interrupts) and those related to the peripheral functions obtained from Copy MCU AT89C55WD Binary. The Reset and Interrupt registers are described in their respective chapters, while the ALU’s STATUS register is described later in this section.
Registers related to the operation of a peripheral feature are described in the chapter for that peripheral. The SFRs are typically distributed among the peripherals whose functions they control. Unused SFR locations are unimplemented and read as ‘0’s to Crack MCU.

Флаш декодирането на микропроцесор PIC18F4515 на микрочип е процес за премахване на механизма за защита срещу фалшифициране на защитен микрочип PIC18F4515 флаш памет и eeprom памет, копиране на заключен микроконтролер PIC18F4515, вграден фърмуер на двоична програма или шестнадесетични данни в друг клонинг MCU PIC18F4515, който ще осигури същите функции като оригиналната версия
 Recover Microprocessor PIC18F4458 Firmware Data
Recover Microprocessor PIC18F4458 Firmware Data
Recover microprocessor PIC18F4458 firmware data is a process to crack microchip microcontroller PIC18F4458 read-out protection and decrypt tamper resistance system, copy binary program and heximal file from encrypted MCU PIC18F4458’s flash memory and eeprom memory;

Recuperar datos de firmware del microprocesador PIC18F4458 es un proceso para descifrar la protección de lectura del microcontrolador PIC18F4458 y descifrar el sistema de resistencia a manipulaciones, copiar programas binarios y archivos heximal desde la memoria flash y la memoria eeprom del MCU PIC18F4458 cifrado;
Device Resets on stack overflow and stack underflow conditions are enabled by setting the STVREN bit in Configuration Register 4L. When STVREN is set, a full or underflow will set the appropriate STKFUL or STKUNF bit and then cause a device Reset when Recover Microprocessor PIC18F4458 Firmware Data.
When STVREN is cleared, a full or underflow condition will set the appropriate STKFUL or STKUNF bit but not cause a device Reset after Recover MCU PIC18F2520 Binary. The STKFUL or STKUNF bits are cleared by the user software or a Power-on Reset.

Recover Microprocessor PIC18F4458 Firmware Data
A fast register stack is provided for the STATUS, WREG and BSR registers, to provide a “fast return” option for interrupts to Crack MCU. The stack for each register is only one level deep and is neither readable nor writable after Recover IC AT89C4051 Heximal. It is loaded with the current value of the corresponding register when the processor vectors for an interrupt.

استعادة بيانات البرامج الثابتة للمعالج الدقيق PIC18F4458 هي عملية لكسر حماية قراءة وحدة التحكم الدقيقة PIC18F4458 وفك تشفير نظام مقاومة العبث، ونسخ البرنامج الثنائي والملف السداسي من ذاكرة فلاش MCU PIC18F4458 المشفرة وذاكرة eeprom؛
All interrupt sources will push values into the stack registers. The values in the registers are then loaded back into their associated registers if the RETFIE, FAST instruction is used to return from the interrupt after Copy Microcontroller P87C51X2BBD Binary.
If both low and high priority interrupts are enabled, the stack registers cannot be used reliably to return from low priority interrupts. If a high priority interrupt occurs while servicing a low priority interrupt, the stack register values stored by the low priority interrupt will be overwritten for the purpose of Copy MCU Atmega32A Software. In these cases, users must save the key registers in software during a low priority interrupt.

Восстановление данных прошивки микропроцессора PIC18F4458 — это процесс взлома защиты от считывания микроконтроллера PIC18F4458 и расшифровки системы защиты от несанкционированного доступа, копирования двоичной программы и шестнадцатеричного файла из зашифрованной флэш-памяти MCU PIC18F4458 и памяти EEPROM;
 Microchip PIC18F4455 Flash Memory Software Restoration
Microchip PIC18F4455 Flash Memory Software Restoration
Microchip PIC18F4455 flash memory software restoration is a process to reverse engineering secured microcontroller PIC18F4455 tamper resistance system, unlock protective microprocessor PIC18F4455 flash memory program and eeprom memory data to copy embedded firmware in the format of binary file or heximal code;
The action of Microchip PIC18F4455 Flash Memory Software Restoration that takes place when the stack becomes full depends on the state of the STVREN (Stack Over- flow Reset Enable) Configuration bit. (Refer to Section 23.1 “Configuration Bits” for a description of the device Configuration bits.) If STVREN is set (default), the 31st push will push the (PC + 2) value onto the stack when Attack Chip Atmega8A Binary, set the STKFUL bit and reset the device. The STKFUL bit will remain set and the Stack Pointer will be set to zero.

استعادة برنامج ذاكرة فلاش PIC18F4455 Microchip هي عملية لعكس نظام مقاومة العبث لوحدة التحكم الدقيقة المؤمنة PIC18F4455، وفتح برنامج ذاكرة فلاش PIC18F4455 للمعالج الدقيق الوقائي وبيانات ذاكرة eeprom لنسخ البرامج الثابتة المضمنة بتنسيق ملف ثنائي أو رمز سداسي؛
If STVREN is cleared, the STKFUL bit will be set on the 31st push and the Stack Pointer will increment to 31. Any additional pushes will not overwrite the 31st push and STKPTR will remain at 31. When the stack has been popped enough times to unload the stack by Attack Microcontroller PIC16C63A Heximal, the next pop will return a value of zero to the PC and sets the STKUNF bit, while the Stack Pointer remains at zero. The STKUNF bit will remain set until cleared by software or until a POR occurs.
Returning a value of zero to the PC on an underflow has the effect of vectoring the program to the Reset vector, where the stack conditions can be verified and appropriate actions can be taken to Attack MCU PIC16CE625 Program. This is not the same as a Reset, as the contents of the SFRs are not affected.
Since the Top-of-Stack is readable and writable, the ability to push values onto the stack and pull values off the stack without disturbing normal program execution is a desirable feature. The PIC18 instruction set includes two instructions, PUSH and POP, that permit the TOS to be manipulated under software control. TOSU, TOSH and TOSL can be modified to place data or a return address on the stack to Crack MCU Eeprom.
Программное восстановление флэш-памяти микрочипа PIC18F4455 — это процесс обратного проектирования защищенной системы защиты от несанкционированного доступа микроконтроллера PIC18F4455, разблокировки защитной программы флэш-памяти микропроцессора PIC18F4455 и данных памяти EEPROM для копирования встроенной прошивки в формате двоичного файла или шестнадцатеричного кода;
The PUSH instruction places the current PC value onto the stack. This increments the Stack Pointer and loads the current PC value onto the stack. The POP instruction discards the current TOS by decrementing the Stack Pointer when Break Microcontroller PIC18F8722 Flash. The previous value pushed onto the stack then becomes the TOS value.

La restauración del software de la memoria flash Microchip PIC18F4455 es un proceso para realizar ingeniería inversa en el sistema de resistencia a manipulaciones del microcontrolador PIC18F4455, desbloquear el programa de memoria flash PIC18F4455 del microprocesador protector y los datos de la memoria eeprom para copiar el firmware integrado en formato de archivo binario o código heximal;