Archive for the ‘Break IC’ Category
 Duplicate DSP TMS320F28055PNT Microcontroller Binary
Duplicate DSP TMS320F28055PNT Microcontroller Binary
Duplicate DSP TMS320F28055PNT Microcontroller Binary from embedded flash memory, crack tamper resistance system of mcu tms320f28055 security fuse bit, copy the firmware from tms320f28055 flash memory to new MCU;
To designate the stages in the product development cycle, TI assigns prefixes to the part numbers of all TMS320™ MCU devices and support tools. Each TMS320 MCU commercial family member has one of three prefixes: TMX, TMP, or TMS (for example, TMS320F28069).
Texas Instruments recommends two of three possible prefix designators for its support tools: TMDX and TMDS. These prefixes represent evolutionary stages of product development from engineering prototypes (with TMX for devices and TMDX for tools) to fully qualified production devices/tools (with TMS for devices and TMDS for tools).
Device development evolutionary flow:
TMX Experimental device that is not necessarily representative of the final device’s electrical specifications when break tms320f28063 microcontroller flash memory protection;
TMP Final silicon die that conforms to the device’s electrical specifications but has not completed quality and reliability verification
TMS Fully qualified production device Support tool development evolutionary flow:
TMDX Development-support product that has not yet completed Texas Instruments internal qualification testing in order to restore dsp tms320f28067 microcontroller locked program;
TMDS Fully qualified development-support product
 Decode ST CPU ST72F321R9 Processor Locked Memory File
Decode ST CPU ST72F321R9 Processor Locked Memory File
Decode ST CPU ST72F321R9 Processor Locked Memory File needs to use laser cutting to remove the security fuse bit of microcontroller, and then copy embedded flash firmware from mcu st72f321r9;

The Flash memory is organised in sectors and can be used for both code and data storage.
Depending on the overall Flash memory size in the micro-controller device, there are up to three user sectors (see below Table). Each of these sectors can be erased independently to avoid unnecessary erasing of the whole Flash memory when only a partial erasing is required after breaking st72f32ak1 mcu flash memory protection.
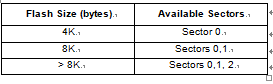
The first two sectors have a fixed size of 4 Kbytes (see below Figure). They are mapped in the upper part of the ST7 addressing space so the reset and in- terrupt vectors are located in Sector 0 (F000h- FFFFh).
3.5.1 Power supply schemes
- VDD = 2.4 to 3.6 V: external power supply for I/Os and the internal regulator. Provided externally through VDD pins.
- VDDA = from VDD to 3.6 V: external analog power supply for ADC, Reset blocks, RCs and PLL. The VDDA voltage level must be always greater or equal to the VDD voltage level and must be provided first.
 Decrypt ST72F321BK MCU Flash Memory Program
Decrypt ST72F321BK MCU Flash Memory Program
Decrypt ST72F321BK MCU Flash Memory Program is a process to pull the embedded firmware from st72f321bk mcu flash memory and then copy the heximal to new microcontroller;
The ST7 dual voltage High Density Flash (HDFlash) is a non-volatile memory that can be electrically erased as a single block or by individu- al sectors and programmed on a Byte-by-Byte ba- sis using an external VPP supply.
The HDFlash devices can be programmed and erased off-board (plugged in a programming tool) or on-board using ICP (In-Circuit Programming) or IAP (In-Application Programming) which can be applied for breaking mcu st72f321j9 flash memory.
The array matrix organisation allows each sector to be erased and reprogrammed without affecting other sectors.
- Three Flash programming modes:
- Insertion in a programming tool. In this mode, all sectors including option bytes can be pro- grammed or erased.
- ICP (In-Circuit Programming). In this mode, all sectors including option bytes can be pro- grammed or erased without removing the de- vice from the application board.
- IAP (In-Application Programming) In this mode, all sectors except Sector 0, can be pro- grammed or erased without removing the de- vice from the application board and while the application is running.
- ICT (In-Circuit Testing) for downloading and executing user application test patterns in RAM when attacking st72f321ar mcu protected flash memory
- Read-out protection
- Register Access Security System (RASS) to prevent accidental programming or erasing
 Attack STMicro ST72F321AR IC Chip Secured Memory
Attack STMicro ST72F321AR IC Chip Secured Memory
Attack STMicro ST72F321AR IC Chip Secured Memory and extract embedded MCU heximal file from flash memory, the firmware can be rewrite to new microprocessor st72f321ar for cloning;
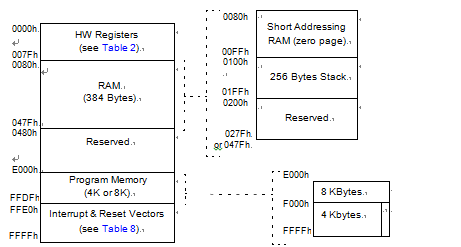
the MCU is capable of ad- dressing 64K bytes of memories and I/O registers.
The available memory locations consist of 128 bytes of register locations, up to 384 bytes of RAM and up to 8 Kbytes of user program memory. The RAM space includes up to 256 bytes for the stack from 0100h to 01FFh by reversing microcontroller st72f32aj1 microcontroller flash memory binary.
The highest address bytes contain the user reset and interrupt vectors.
IMPORTANT: Memory locations marked as “Re- served” must never be accessed. Accessing a re- served area can have unpredictable effects on the devices.
The contents of the I/O port DR registers are readable only in output configuration. In input configuration, the values of the I/O pins are returned instead of the DR register contents after breaking st72f321aj mcu flash memory fuse bit.
The bits associated with unavailable pins must always keep their reset value.
 Break ST72F321J9 Microcontroller Flash/ROM Memory
Break ST72F321J9 Microcontroller Flash/ROM Memory
Break ST72F321J9 Microcontroller Flash/ROM Memory and extract embedded data from secured flash controlled by microprocessor ST72F321J9, and then crack secured mcu st72f321j9 security fuse bit;
PIN DESCRIPTION (Cont’d)
For external pin connection guidelines, refer to See “ELECTRICAL CHARACTERISTICS” on page 113.
Legend / Abbreviations for Table 1:
Type: I = input, O = output, S = supply
Input level: A = Dedicated analog input In/Output level: C = CMOS 0.3VDD/0.7VDD
CT= CMOS 0.3VDD/0.7VDD with input trigger Output level:
HS = 20mA high sink (on N-buffer only)
Port and control configuration:
- Input:
- float = floating, wpu = weak pull-up, int = interrupt 1), ana = analog ports
- Output: OD = open drain 2), PP = push-pull
Refer to “I/O PORTS” on page 42 for more details on the software configuration of the I/O ports.
The RESET configuration of each pin is shown in bold. This configuration is valid as long as the device is in reset state.
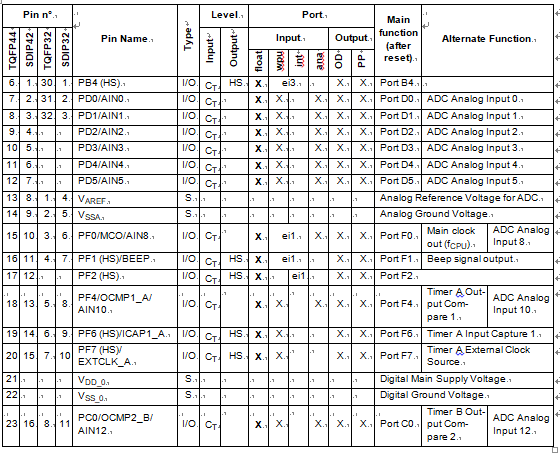
- In the interrupt input column, “eiX” defines the associated external interrupt vector. If the weak pull-up column (wpu) is merged with the interrupt column (int) when breaking st72f32ak1 microcontroller flash memory, then the I/O configuration is pull-up interrupt input, else the configuration is floating interrupt input.
- In the open drain output column, “T” defines a true open drain I/O (P-Buffer and protection diode to VDD are not implemented). See See “I/O PORTS” on page 42. and Section 12.8 I/O PORT PIN CHARACTER- ISTICS for more details.
- OSC1 and OSC2 pins connect a crystal/ceramic resonator, or an external source to the on-chip oscil- lator; see Section 1 INTRODUCTION and Section 12.5 CLOCK AND TIMING CHARACTERISTICS for more details.
- On the chip, each I/O port has 8 pads. Pads that are not bonded to external pins are in input pull-up configuration after reset and restore st72f32ak2 mcu encrypted flash heximal. The configuration of these pads must be kept at reset state to avoid added current consumption.
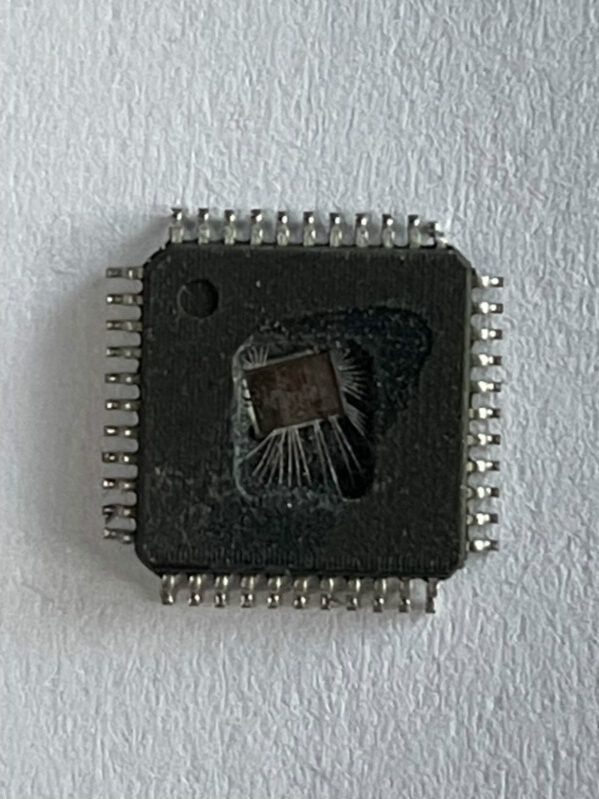
 Break STMicrocontroller ST72F32AK1 Flash Memory Protection
Break STMicrocontroller ST72F32AK1 Flash Memory Protection
Break STMicrocontroller ST72F32AK1 Flash Memory Protection needs to remove the fuse bit of mcu embedded system and readout the locked memory firmware from processor;
8K dual voltage High Density Flash (HDFlash) or ROM with read-out protection capability. In- Application Programming and In-Circuit Pro- gramming for HDFlash devices
384 bytes RAM
HDFlash endurance: 100 cycles, data reten- tion: 40 years at 85°C
■ Clock, Reset And Supply Management
Clock sources: crystal/ceramic resonator os- cillators and bypass for external clock
PLL for 2x frequency multiplication
Four Power Saving Modes: Halt, Active-Halt, Wait and Slow
■ Interrupt Management
Nested interrupt controller
14 interrupt vectors plus TRAP and RESET
6 external interrupt lines (on 4 vectors)
■ Up to 32 I/O Ports
32/24 multifunctional bidirectional I/O lines
22/17 alternate function lines
12/10 high sink outputs
■ 4Timers
Main Clock Controller with: Real time base, Beep and Clock-out capabilities
Configurable watchdog timer in order to break stm8s207k6 locked mcu memory
Two 16-bit Timers with: 2 input captures, 2 output compares, PWM and pulse generator modes
■ 2 Communications Interfaces
SPI synchronous serial interface
SCI asynchronous serial interface
– 10-bit ADC with up to 12 robust input ports
■ Instruction Set
8-bit Data Manipulation
63 Basic Instructions when recover secured stm8s207c6 microcontroller heximal file
17 main Addressing Modes
8 x 8 Unsigned Multiply Instruction
■ Development Tools
Full hardware/software development package
In-Circuit Testing capability
 Secured Microcontroller STM8S207K8T6 Flash Heximal Code Unlocking
Secured Microcontroller STM8S207K8T6 Flash Heximal Code Unlocking
Secured Microcontroller STM8S207K8T6 Flash Heximal Code Unlocking will be able to reset the MCU status and readout software from stm8s207k8 program flash memory directly, the fuse bit of processor’s stm8s207k8 will be cracked by focus ion beam;
Susceptibility tests are performed on a sample basis during product characterization.
Functional EMS (electromagnetic susceptibility)
While executing a simple application (toggling 2 LEDs through I/O ports), the product is stressed by two electromagnetic events until a failure occurs (indicated by the LEDs).
ESD: Electrostatic discharge (positive and negative) is applied on all pins of the device until a functional disturbance occurs. This test conforms with the IEC 61000-4-2 standard.
güvenli mikrodenetleyici STM8S207K8T6 flaş onaltılık kod kilidini açma, MCU durumunu sıfırlayabilecek ve yazılımı doğrudan stm8s207k8 program flash belleğinden okuyabilecek, işlemcinin stm8s207k8’inin sigorta biti odak iyon ışını ile kırılacaktır;
FTB: A burst of fast transient voltage (positive and negative) is applied to VDD and VSS through a 100 pF capacitor, until a functional disturbance occurs. This test conforms with the IEC 61000-4-4 standard which is an important fact for reversing stm8s005 mcu flash memory code.
A device reset allows normal operations to be resumed. The test results are given in the table below based on the EMS levels and classes defined in application note AN1709 (EMC design guide for STM microcontrollers).
Designing hardened software to avoid noise problems
EMC characterization and optimization are performed at component level with a typical application environment and simplified MCU software. It should be noted that good EMC performance is highly dependent on the user application and the software in particular by recovering stm8s005k6 microcontroller data eeprom content.
Therefore it is recommended that the user applies EMC software optimization and prequalification tests in relation with the EMC level requested for his application.
 ST STM8S207K6 Locked Microcontroller Memory Breaking
ST STM8S207K6 Locked Microcontroller Memory Breaking
ST STM8S207K6 Locked Microcontroller Memory Breaking is a process to reverse engineering stm8s207k6 microcontroller structure and disable its protection and reset the status from locked to unlocked, copy embedded firmware from stm8s207k6 mcu flash content;
Write protection of Flash program memory and data EEPROM is provided to avoid unintentional overwriting of memory that could result from a user software malfunction.
There are two levels of write protection. The first level is known as MASS (memory access security system). MASS is always enabled and protects the main Flash program memory, data EEPROM and option bytes and we have to use technique to reverse mcu stm8s005c6 flash memory code.

ST STM8S207K6 gesperrter Mikrocontroller-Speicherbruch ist ein Prozess zum Reverse Engineering von STM8S207K6-Mikrocontrollern
Strukturieren und deaktivieren Sie den Schutz und setzen Sie den Status von gesperrt auf entsperrt zurück, kopieren Sie die eingebettete Firmware aus dem MCU-Flash-Inhalt STM8S207K6
To perform in-application programming (IAP), this write protection can be removed by writing a MASS key sequence in a control register. This allows the application to write to data EEPROM, modify the contents of main program memory or the device option bytes.
A second level of write protection, can be enabled to further protect a specific area of memory known as UBC (user boot code).
The size of the UBC is programmable through the UBC option byte, in increments of 1 page (512 bytes) by programming the UBC option byte in ICP mode when break mcu stm8s103f3 flash memory.
This divides the program memory into two areas:
Main program memory: Up to 128 Kbytes minus UBC
User-specific boot code (UBC): Configurable up to 128 Kbytes
The UBC area remains write-protected during in-application programming. This means that the MASS keys do not unlock the UBC area. It protects the memory used to store the boot program, specific code libraries, reset and interrupt vectors, the reset routine and usually the IAP and communication routines.
 Hack STM8S105C6T3 Microprocessor Flash and Eeprom Memory
Hack STM8S105C6T3 Microprocessor Flash and Eeprom Memory
Hack STM8S105C6T3 Microprocessor Flash and Eeprom Memory needs to crack stm8s105 mcu protective system including remove its security fuse bit and then copy locked program from flash and eeprom memory of microcontroller;

Write protection of Flash program memory and data EEPROM is provided to avoid unintentional overwriting of memory that could result from a user software malfunction.
There are two levels of write protection. The first level is known as MASS (memory access security system) when reverse engineering stm8s105k6 data eeprom and program flash system. MASS is always enabled and protects the main Flash program memory, data EEPROM and option bytes.

pirater le flash du microprocesseur STM8S105C6T3 et la mémoire eeprom doit craquer le système de protection stm8s105 mcu, y compris retirer son bit de fusible de sécurité, puis copier le programme verrouillé à partir de la mémoire flash et eeprom du microcontrôleur ;
To perform in-application programming (IAP), this write protection can be removed by writing a MASS key sequence in a control register. This allows the application to write to data EEPROM, modify the contents of main program memory or the device option bytes to break mcu stm8s105k4 protective flash and eeprom memory.
A second level of write protection, can be enabled to further protect a specific area of memory known as UBC (user boot code). Refer to the figure below. The size of the UBC is programmable through the UBC option byte, in increments of 1 page (64-byte block) by programming the UBC option byte in ICP mode.
 Crack Texas Instrument MSP430G2230 MCU Flash Memory
Crack Texas Instrument MSP430G2230 MCU Flash Memory
Crack Texas Instrument MSP430G2230 MCU Flash Memory needs to decapsulate MSP430G2230 by chemical solution and unlock microcontroller tamper resistance system, extract embedded source code from TI IC chip;
Universal Serial Communications Interface (USCI)
The USCI module is used for serial data communication. The USCI module supports synchronous communication protocols such as SPI (3 or 4 pin) and I2C, and asynchronous communication protocols such as UART, enhanced UART with automatic baudrate detection (LIN), and IrDA. Not all packages support the USCI functionality.

çatlak Texas Instrument MSP430G2230 MCU flash belleğin MSP430G2230’u kimyasal çözelti ile kapsülünü çözmesi ve mikrodenetleyici kurcalama direnci sisteminin kilidini açması, gömülü kaynak kodunu TI IC yongasından çıkarması gerekir
USCI_A0 provides support for SPI (3 or 4 pin), UART, enhanced UART, and IrDA. USCI_B0 provides support for SPI (3 or 4 pin) and I2C.
Comparator_A+
The primary function of the comparator_A+ module is to support precision slope analog-to-digital conversions, battery-voltage supervision, and monitoring of external analog signals.
ADC10 (MSP430G2x53 Only)
The ADC10 module supports fast 10-bit analog-to-digital conversions. The module implements a 10-bit SAR core, sample select control, reference generator, and data transfer controller (DTC) for automatic conversion result handling by replicating msp430g2231 cpu flash memory file, allowing ADC samples to be converted and stored without any CPU intervention.