 Attack Microcontroller ST62T15C6 firmware
Attack Microcontroller ST62T15C6 firmware
The ST62T15C6 is an 8-bit microcontroller from STMicroelectronics, commonly used in embedded systems. Security researchers and hardware hackers often attempt to attack, crack, or reverse engineer its firmware for analysis, recovery, or cloning purposes. This article explores various techniques used to extract, decode, or dump the firmware from the ST62T15C6 microcontroller.
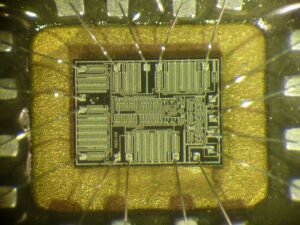
O ST62T15C6 é um microcontrolador de 8 bits da STMicroelectronics, comumente usado em sistemas embarcados. Pesquisadores de segurança e hackers de hardware frequentemente tentam atacar, crackear ou fazer engenharia reversa em seu firmware para fins de análise, recuperação ou clonagem. Este artigo explora várias técnicas usadas para extrair, decodificar ou despejar o firmware do microcontrolador ST62T15C6.
1. Firmware Extraction Methods
Dumping Flash Memory
The primary method to attack the ST62T15C6 involves dumping the contents of its flash memory or EEPROM memory. Since the firmware is stored in non-volatile memory, attackers use hardware tools like:
- Programmers/JTAG interfaces – If debug ports are accessible, firmware can be read directly.
- Logic analyzers & bus sniffers – Monitoring communication between the MCU and external memory (if any).
- Voltage glitching – Disrupting power or clock signals to bypass read protections.
Decapsulation & Microprobing
If security fuses are enabled, attackers may resort to decapsulating the chip to access the silicon die. Using microprobing, they can directly read the binary code from the memory cells. This method is expensive and requires advanced equipment.
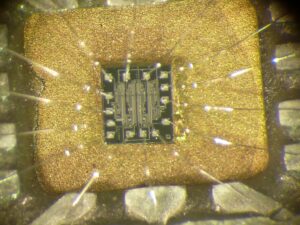
ST62T15C6 — это 8-битный микроконтроллер от STMicroelectronics, обычно используемый во встраиваемых системах. Исследователи безопасности и хакеры оборудования часто пытаются атаковать, взломать или провести обратную разработку его прошивки для анализа, восстановления или клонирования. В этой статье рассматриваются различные методы, используемые для извлечения, декодирования или дампа прошивки из микроконтроллера ST62T15C6.
2. Reverse Engineering the Firmware
Once the heximal data or binary code is extracted, the next step is decoding or disassembling it. Common techniques include:
- Static analysis – Using disassemblers like Ghidra or IDA Pro to convert machine code into assembly.
- Dynamic analysis – Running the firmware in an emulator (e.g., QEMU) to observe behavior.
- Pattern recognition – Searching for known opcode sequences to identify functions.
Since the ST62T15C6 uses a proprietary architecture, custom tools may be needed to decrypt the program file fully.
3. Cloning & Firmware Modification
After successful extraction, attackers may:
- Copy the firmware to another ST62T15C6 chip.
- Modify the source code (if decompiled) to remove security checks.
- Restore corrupted firmware for device recovery.
4. Protection & Countermeasures
To prevent such attacks, manufacturers implement:
- Read-out protection bits – Locking firmware access.
- Encrypted firmware updates – Preventing easy decoding.
- Secure boot mechanisms – Blocking unauthorized code execution.
Conclusion
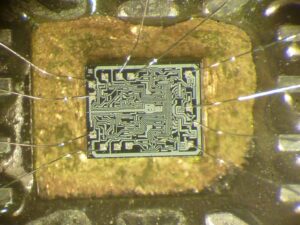
يُعد ST62T15C6 متحكمًا دقيقًا ثماني البتات من شركة STMicroelectronics، ويُستخدم عادةً في الأنظمة المدمجة. غالبًا ما يحاول باحثو الأمن ومخترقو الأجهزة مهاجمة أو اختراق أو عكس هندسة البرنامج الثابت الخاص به لأغراض التحليل أو الاستعادة أو الاستنساخ. تستكشف هذه المقالة التقنيات المختلفة المستخدمة لاستخراج أو فك تشفير أو تفريغ البرنامج الثابت من المتحكم الدقيق ST62T15C6
Attacking the ST62T15C6 microcontroller firmware requires a mix of hardware and software techniques, from dumping flash memory to reverse engineering binary code. While these methods can be used for legitimate recovery or research, they also pose security risks if exploited maliciously. Developers must implement strong protections to safeguard their firmware from unauthorized cloning or decryption.

Attack Microcontroller ST62T15C6 protective system and extract firmware from MCU ST62T15 memory, the whole tamper resistance system will be disable by Microprocessor unlocking technique
Attack Microcontroller ST62T15C6 protective system and extract firmware from MCU ST62T15 memory, the whole tamper resistance system will be disable by Microprocessor unlocking technique;
Memories
– 2K or 4K bytes Program memory (OTP, EPROM, FASTROM or ROM) with read-out protection
– 64 bytes RAM
Clock, Reset and Supply Management
– Enhanced reset system
– Low Voltage Detector (LVD) for Safe Reset
– Clock sources: crystal/ceramic resonator or RC network, external clock, backup oscillator (LFAO)
– Oscillator Safeguard (OSG)
– 2 Power Saving Modes: Wait and Stop
Interrupt Management
– 4 interrupt vectors plus NMI and RESET
– 20 external interrupt lines (on 2 vectors)
– 1 external non-interrupt line
– 20 multifunctional bidirectional I/O lines
– 16 alternate function lines
– 4 high sink outputs (20mA)
– Configurable watchdog timer
– 8-bit timer/counter with a 7-bit prescaler
Analog Peripheral
– 8-bit ADC with 16 input channels
Instruction Set
– 8-bit data manipulation
– 40 basic instructions
– 9 addressing modes
– Bit manipulation
The ST6215C, 25C devices are low cost members mable option bytes of the OTP/EPROM versions of the ST62xx 8-bit family of microcontrol-in the ROM option list applications. All ST62xx devices are based on a building block approach: a common core is surrounded by a number of on-chip peripherals for the purpose of IC program hacking.
Circuit Engineering Company Limited continues to be recognized as the Southern China Leader in Services for IC Break, MCU attack, Chip Recover, Microcontroller Copy service. With the advancement of today’s modern circuit board technology, it is more important than ever to have specialists available to help you at a moment’s notice. Our engineering and commercial teams collectively have a vast amount of electronic experience covering field include Consumer Electronics, Industrial Automation Electronics, Wireless Communication Electronics., etc. For more information please contact us through email.