 Attack Microchip dsPIC30F6011 Flash Memory
Attack Microchip dsPIC30F6011 Flash Memory
Attack Microchip dsPIC30F6011 Flash tamper resistance system and extracted heximal from locked microcontroller dsPIC30F6011, MCU dsPIC30F6011 cracking will require to use focus ion beam technique;
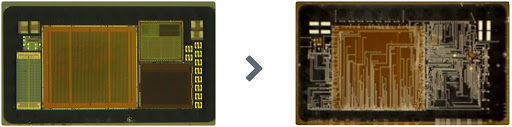
This document contains specific information for the dsPIC30F6011/6012/6013/6014 Digital Signal Controller (DSC) devices. The dsPIC30F devices contain extensive Digital Signal Processor (DSP) functionality within a high-performance 16-bit microcontroller (MCU) architecture. Figure 1-1 and Figure 1-2 show device block diagrams for dsPIC30F6011/6012 and dsPIC30F6013/6014 respectively.
This section contains a brief overview of the CPU architecture of the dsPIC30F. For additional hardware and programming information, please refer to the “dsPIC30F Family Reference Manual” (DS70046) and the “dsPIC30F/33F Programmer’s Reference Manual” (DS70157) respectively.

Mikroçip koruyucu mikrodenetleyici dsPIC30F6011 kurcalamaya karşı dayanıklılık sistemini kırın ve kilitli güvenli mikroişlemci dsPIC30F6011’den ikili dosya veya onaltılı veri formatında gömülü ürün yazılımını çıkarın, şifrelenmiş MCU dsPIC30F6011 tersine mühendislik, odak iyon ışın tekniğini kullanmayı gerektirecektir.
The core has a 24-bit instruction word. The Program Counter (PC) is 23 bits wide with the Least Significant bit (LSb) always clear (refer to Section 3.1 “Program Address Space”), and the Most Significant bit (MSb) is ignored during normal program execution, except for certain specialized instructions.
Thus, the PC can address up to 4M instruction words of user program space. An instruction prefetch mechanism is used to help maintain throughput. Program loop constructs, free from loop count management overhead, are supported using the DO and REPEAT instructions, both of which are interruptible at any point in the process of attacking encrypted mcu code.

Взлом защитного микроконтроллера микрочипа dsPIC30F6011, система защиты от несанкционированного доступа и извлечение встроенной прошивки в формате двоичного файла или шестнадцатеричных данных из заблокированного защищенного микропроцессора dsPIC30F6011, зашифрованный микроконтроллер dsPIC30F6011, обратный инжиниринг потребует использования техники фокусировки ионного луча.
The working register array consists of 16 x 16-bit registers, each of which can act as data, address or offset registers. One working register (W15) operates as a software Stack Pointer for interrupts and calls. The data space is 64 Kbytes (32K words) and is split into two blocks, referred to as X and Y data memory.
Hackear el microcontrolador de seguridad del microchip dsPIC30F6011, el sistema antimanipulación y extraer firmware en un archivo binario o datos hexadecimales del microprocesador de seguridad dsPIC30F6011 bloqueado, el microcontrolador cifrado dsPIC30F6011 y la ingeniería inversa requerirán el uso de una técnica de enfoque de haz de iones.
The upper 32 Kbytes of data space memory can be mapped into the lower half (user space) of program space at any 16K program word boundary, defined by the 8-bit Program Space Visibility Page (PSVPAG) register. This lets any instruction access program space as if it were data space, with a limitation that the access requires an additional cycle. Moreover, only the lower 16 bits of each instruction word can be accessed using this method.